Security by Design: Meaning, Principles, and Approach
Security by Design: The Blueprint for Resilient Digital Systems
Beyond the SbD Checklist Mentality
Cybersecurity threats are evolving faster than ever, yet many organizations still treat security as an afterthought—a box to check off once software is already built. Security by Design (SbD) flips this reactive model on its head. Instead of patching vulnerabilities post-launch, SbD integrates security principles into the very foundation of digital products and services.
But what does this approach entail? How can organizations effectively embed security without stifling innovation? And where does AI fit into this evolving landscape? Let’s break it down.
What Is Security by Design?
Security by Design (SbD) is a proactive approach to cybersecurity, ensuring that security considerations are embedded at every stage of the software development lifecycle (SDLC). Rather than bolting on security controls later, SbD integrates protective measures from the ground up.
Key Principles of Security by Design:
- Least Privilege: Grant only the minimum access necessary.
- Defense in Depth: Layer multiple security controls for redundancy.
- Fail Securely: Ensure systems handle failures safely.
- Zero Trust Architecture: Assume no user or device is inherently trustworthy.
- Secure Defaults: Prioritize security-friendly configurations out of the box.
Why Security by Design Matters More Than Ever
1. The Rising Cost of Security Failures
A study by IBM found that the average cost of a data breach in 2024 was $4.88 million. The earlier security flaws are detected, the cheaper they are to fix. Integrating security from the start significantly reduces these risks.
2. Regulatory and Compliance Pressures
With regulations like GDPR, CCPA, and NIST 800-53, organizations must demonstrate a commitment to security best practices. SbD ensures compliance isn’t a last-minute scramble.
3. Trust and Competitive Advantage
Customers are increasingly concerned about data security. Companies that prioritize SbD differentiate themselves as trustworthy brands, which can lead to better customer retention and business growth.
How to Achieve Success with Security by Design
1. Adopt a Secure Development Lifecycle (SDLC)
Security must be woven into every phase of development:
- Requirements Gathering: Identify security needs early.
- Design Phase: Incorporate threat modeling.
- Coding: Implement secure coding practices.
- Testing: Use automated security scans and penetration testing.
- Deployment: Monitor and respond to threats in real-time.
2. Leverage Security Frameworks
Several frameworks guide organizations in implementing SbD effectively:
- NIST Cybersecurity Framework (CSF): Provides a structured approach to managing cybersecurity risks.
- OWASP Software Assurance Maturity Model (SAMM): Helps developers assess and improve security practices.
- ISO/IEC 27001: Establishes a global standard for information security management.
3. Embed Security Culture Across Teams
Security is not just an IT problem. Developers, designers, product managers, and executives must all understand and embrace security as part of their workflows.
The Role of DSP and DSPM in Security by Design
1. DSP & DSPM: Strengthening Security by Design
DSP (Data Security Posture) refers to the overall security health of an organization’s data across cloud, on-prem, and hybrid environments. DSPM (Data Security Posture Management) provides continuous monitoring, classification, and risk assessment to enforce security best practices throughout the data lifecycle.
2. Where DSPM Enhances Security by Design
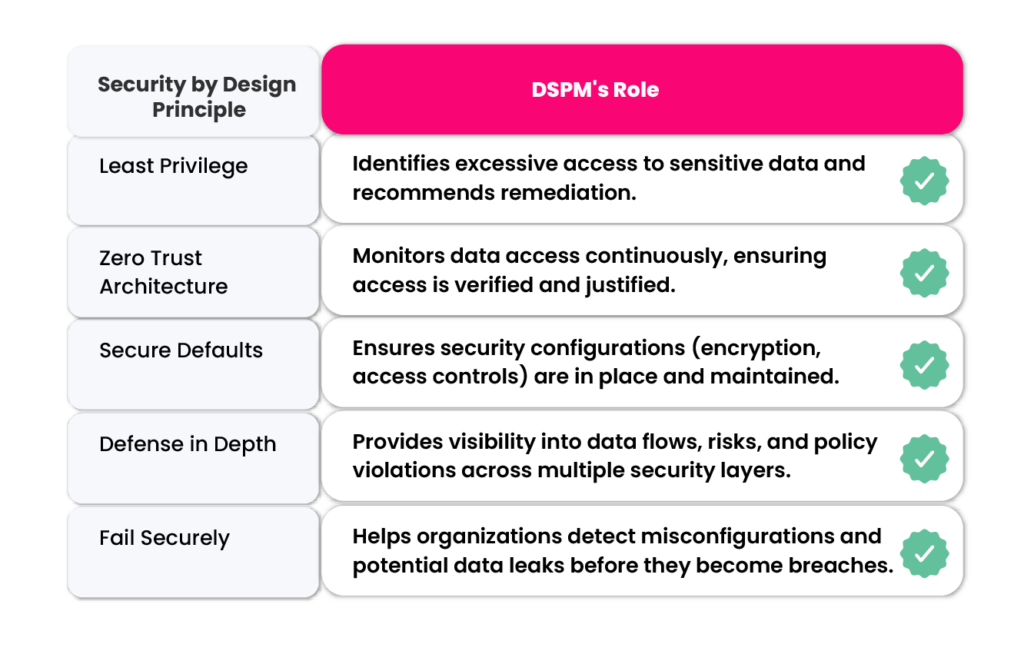
3. DSPM in Action: A Security by Design Use Case
Imagine a SaaS company handling customer financial data:
- Without DSPM: Sensitive data could be stored in the cloud without proper encryption, excessive user access, or weak permissions—violating Security by Design principles.
- With DSPM: The system automatically detects misconfigured S3 buckets, flags excessive permissions, and ensures encryption policies are enforced.
4. Measuring Success: DSPM Metrics in Security by Design
To know if your Security by Design approach is working, use DSPM to track:
- Data Risk Score: How exposed is your sensitive data?
- Access Control Violations: Are permissions following least privilege?
- Data Movement & Shadow Data: Are sensitive data copies being created outside of security policies?
- Compliance Readiness: Does your data posture align with GDPR, CCPA, or NIST standards?
The Hurdles in Implementing Security by Design (And How to Overcome Them)
1. Perceived Complexity and Cost
- Challenge: Many teams see SbD as too complicated or expensive.
- Solution: Start small with high-impact security measures and use automation to streamline security testing.
2. Developer Resistance
- Challenge: Developers may feel security slows down innovation.
- Solution: Provide security training, integrate security seamlessly into development tools, and reward secure coding practices.
3. Balancing Security and User Experience
- Challenge: Overly strict security measures can frustrate users.
- Solution: Implement adaptive security measures, like risk-based authentication, that adjust based on user behavior.
Where AI Helps (and Hurts) Security by Design
AI as a Security Ally
- Threat Detection & Response: AI-driven security tools analyze massive datasets to detect anomalies faster than humans.
- Automated Code Review: AI can identify vulnerabilities in code before deployment.
- Behavioral Analytics: AI enhances Zero Trust by detecting suspicious user behavior in real time.
AI as a Security Risk
- AI-Powered Cyberattacks: Attackers use AI to automate sophisticated phishing or malware campaigns.
- False Positives: AI may flag normal behavior as a threat, leading to alert fatigue.
- Data Privacy Concerns: AI models require vast amounts of data, which could introduce new security risks if mishandled.
Build Security into Your DNA with BigID
Security by Design is not a one-time initiative but an ongoing commitment. The next time you launch a new product or service, ask yourself: Is security embedded in the foundation, or is it just an afterthought?
BigID is the first modular data platform to address the entirety of data risk across security, regulatory compliance, and AI. It eliminates the need for disparate, siloed solutions by combining the capabilities of DSPM, DLP, data access governance, AI model governance, privacy, data retention, and more — all within a single, cloud-native platform.
With BigID organizations can:
- Know Your Data: Automatically classify, categorize, tag, and label sensitive data with unmatched accuracy, granularity, and scale.
- Improve Data Security Posture: Proactively prioritize and target data risks, expedite SecOps, and automate DSPM.
- Remediate Data Your Way: Centrally manage data remediation – delegate to stakeholders, open tickets, or make API calls across your stack.
- Enable Zero Trust: Reduce overprivileged access & overexposed data, and streamline access rights management to enable zero trust.
- Best-in-Class Labeling & Tagging: BigID applies deep classification metadata, sensitivity labels, and usage tags automatically and consistently – powering downstream enforcement in Microsoft Purview, Google Workspace, and beyond.
- AI Intelligence and AI Security: BigID’s AI-driven approach not only identifies sensitive content but also safeguards AI models and pipelines from exposure and unauthorized training on risky data.
To see how BigID can kickstart your security initiatives— get a 1:1 demo with our experts today.













