§164.308(a)(1)(ii)(A)
Identify & Classify PHI
Automatically discover and classify PHI across cloud, on-prem, and hybrid environments—including structured and unstructured data
The Health Insurance Portability and Accountability Act (HIPAA) sets strict requirements for protecting patient health information (PHI). But compliance isn’t just about checking boxes—it’s about knowing exactly what data you have, where it lives, who can access it, and how it’s being used.
BigID helps healthcare organizations go beyond surface-level compliance to build a smarter, stronger approach to PHI protection. From automatic PHI discovery to granular access visibility, BigID gives you the tools to comply with HIPAA and stay ahead of risk.
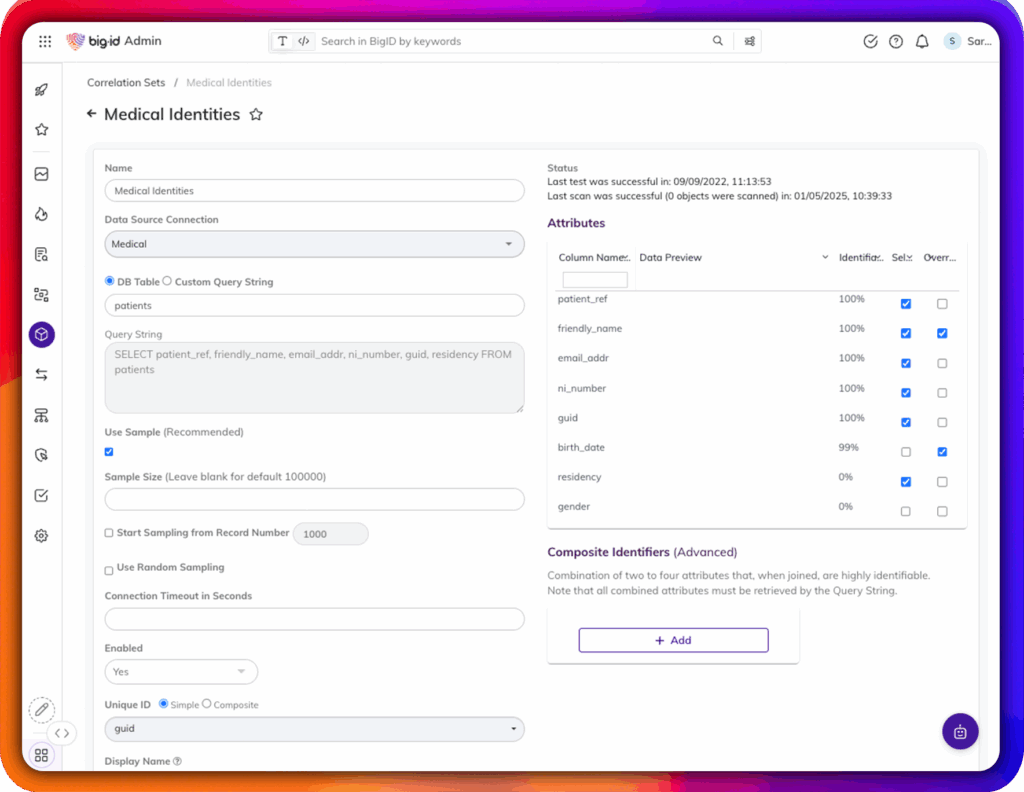
§164.308(a)(1)(ii)(A)
Automatically discover and classify PHI across cloud, on-prem, and hybrid environments—including structured and unstructured data
§164.312(a)(1), §164.308(a)(1)
Get full visibility into who has access to PHI and where it’s exposed. Monitor data access patterns and generate audit-ready reports
§164.514(d), §164.530(c)
Identify stale, unused, or over-retained PHI. Apply policies for deletion, minimization, or retention based on regulation and risk
§164.308(a)(1)(ii)(A)
Continuously scan for sensitive data risks, misconfigurations, overexposed PHI, and policy violations
§164.308(a)(6)(ii)
Accelerate breach response by pinpointing what PHI was impacted, where it lived, and who accessed it—within minutes
§164.308(b)(1), §164.314(a)(1)
Understand what PHI is shared with vendors or processors. Monitor risk and ensure partners meet contractual obligations
§164.524, §164.526
Automatically fulfill access and amendment requests by locating all relevant PHI tied to an individual across systems—streamlining DSARs and compliance with patient rights
§164.312(c)(1)
Monitor PHI for unauthorized changes with metadata analysis and integrity checks. Detect anomalies and flag data integrity issues automatically
BigID is trusted by leading hospitals, insurers, and healthcare networks to:
Move from reactive to proactive: Identify PHI exposure before it becomes a breach
Unify fragmented data silos: Discover PHI across EHRs, SaaS, cloud storage, and legacy systems
Operationalize policies: Enforce data retention, consent, and minimization with automation
Scale for future regulation: Be ready for HITECH updates, state-level mandates, and new patient privacy laws
Whether you’re launching a compliance program, refreshing risk assessments, or modernizing your security stack – BigID helps you prove HIPAA compliance while improving patient data protection.
HIPAA compliance doesn’t live in a silo. BigID brings together security, privacy, and compliance with a unified view of patient data risk—so every team can act with insight.
See how BigID can help your team reduce risk, automate compliance, and protect patient trust. Schedule your HIPAA compliance demo today.



















