Bucket Configuration Management: Find & Fix Misconfigured S3 Buckets – at Cloud Scale!

To secure cloud services like Amazon S3, a robust CSPM strategy is vital. Managing bucket configurations is a key aspect of CSPM, as misconfigurations can lead to unauthorized data exposure and contribute to major data breaches.
Why does this persist? It’s due to limited visibility, lack of scalable control, and human error. AWS and similar dynamic cloud environments pose security challenges when managing numerous instances and services. Bucket configuration changes by developers or administrators can unwittingly expose vulnerable buckets. Storing sensitive data in the cloud intensifies this security nightmare. Picture a publicly accessible S3 bucket holding unknown sensitive data – a potential disaster.
Ready to end this nightmare? Meet Bucket Configuration Management, where our industry-leading DSPM meets crucial CSPM capabilities. Proactively identify, investigate, and remediate misconfigured, sensitive AWS S3 buckets, at cloud scale!
Leverage data-centric, risk-aware policies, insights, and automation to find and fix misconfigured sensitive S3 buckets:
Identify Misconfigurations
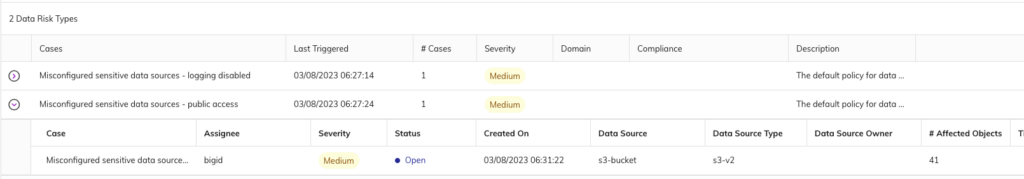
Leverage out-of-the-box or custom policies that help detect and pinpoint misconfigured S3 buckets that hold sensitive data. Define security policies to pinpoint when buckets with sensitive data objects are publicly accessible and/or not monitored (logging disabled). Use these policies to trigger the right notifications to the people and tools, at the right time.
Streamline Risk Management
Centralize risk remediation with BigID’s Data Risk Management dashboard to accelerate your security operations. Get a prioritized list of misconfiguration alerts based on severity level measured by the sensitivity of that data that resides in the bucket. Drill down, investigate, and kick off seamless remediation workflows within a single pane of glass.
By integrating configuration management into DSPM, realize the synergistic benefits when both are orchestrated seamlessly:
Mitigate Cloud Data Exposure
Reduce the window of vulnerability and minimize the likelihood of cloud data exposure and use. Elevate and maintain your cloud data security posture by validating configurations. Monitor risk reduction over time knowing your S3 environment is markedly more secure.
Reduce Insider Risk
Lock down publicly accessible buckets from unwanted insiders and third parties. Ensure that access logging is enabled across all sensitive, S3 buckets for security and access audit purposes.
Accelerate Risk Management
Save time and resources by centralizing and automating cloud data risk management with BigID. Reallocate those savings back to more strategic initiatives or more pressing security issues across your environment.
If you’re at BlackHat 2023, stop by our booth (#2600), join us for a VIP happy hour, or book a 1:1 meeting to learn more. Can’t make it? Schedule a virtual 1:1 demo with one of our data security experts to get started!













