Data Intelligence Enrichment: The Mainstay of Security

With the ever changing threat landscape, the Security industry has leveraged Threat Intelligence data and research to enrich telemetry collected from various sensors. We have taken the step to learn about the adversary and understand their tactics, techniques and procedures in an effort to provide precision, detection, and alerting mechanisms.
Over the last several years we have seen the evolution of Threat Intelligence from the days of reports on threat actors with list of Indicators of compromise to direct data enrichment (“actionable threat intelligence”) in SIEMs or SOAR platforms for “real time threat detection”.
And what is all this for… Ultimately, to be able to protect systems that contain sensitive data.
As an industry we have missed the mark and are significantly behind understanding our data. It’s imperative we understand the information we possess, who has access to it, and what systems are storing this information. The advancements in security technologies have given us the ability to identify malware, misconfigurations, and vulnerabilities while overlaying actionable threat intelligence and correlating all of these telemetry points for alert prioritization.
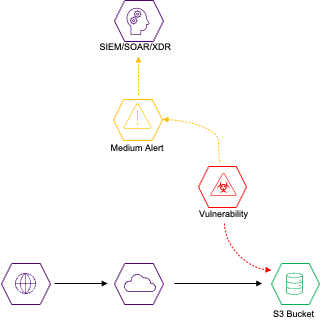
But can you really prioritize alerts from systems if you are not aware of which systems possess critical or sensitive data? This is where the concept of Data Intelligence Enrichment was born. Discovering all of the critical or sensitive data in your environment and integrating that information with your security tools for an even higher validity alert prioritization.
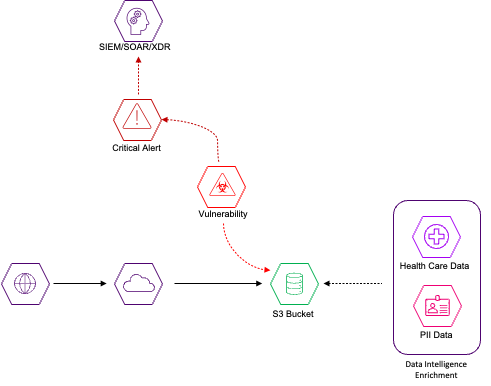
How to get started with data intelligence enrichment
From threat detection to incident response, here are 5 steps to start your journey:
-
- Develop you security strategy to mitigate attack vectors that may persist in your environment
- Depending on the attack vector you are solving for, ensure your detection tooling (in this case we will refer to Cloud Security Posture Management tooling) has the capability to ingest telemetry data from data discovery solutions (BigID or SmallID)
- Utilizing BigID discover and classify all of the data in your environment
- Utilizing BigID integration(s) with your CSPM alert severity will automatically be calculated due to the data contained within the system being alerted on, and prioritization will be adjusted accordingly
- Your Security team, Security Operations Center (SOC), or Managed Detection and Response (MDR) will be able to respond to the alerts that are crucial to reducing the risk to you business
You can finally cut through the noise, reduce alert fatigue, and arm your security team to become better, faster, and stronger— all while staying one step ahead of the evolving threat landscape. Get a 1:1 demo today.













