Zero Trust from the Data Up
Strengthen your zero trust strategy with a data first approach: understand the data you have, get to a least privileged model, and reduce risk on your data.
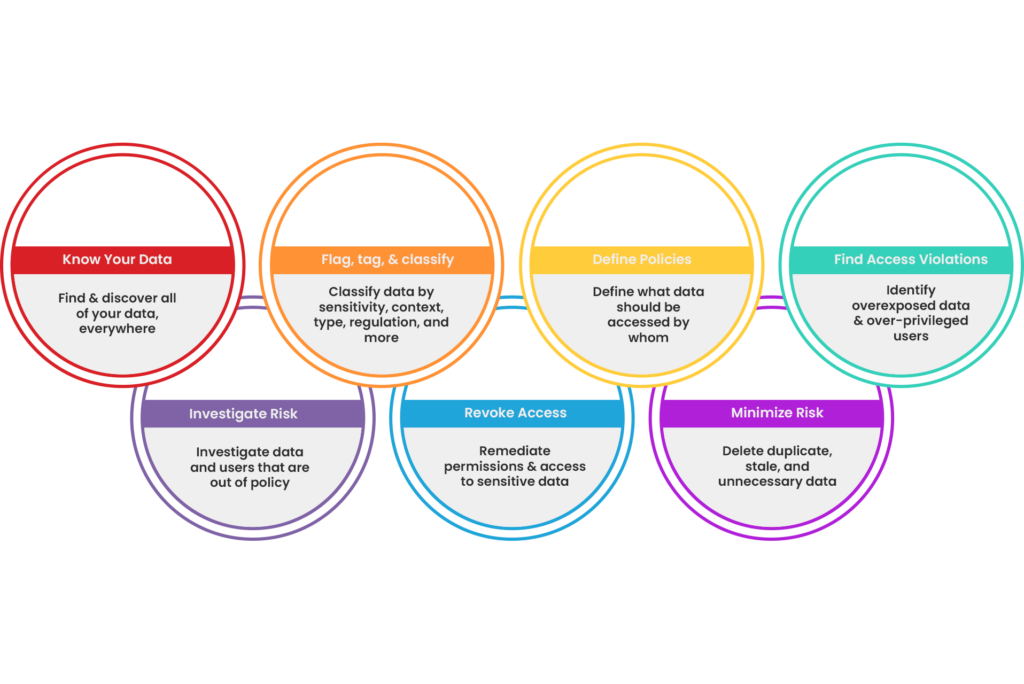
Solutions for Zero Trust
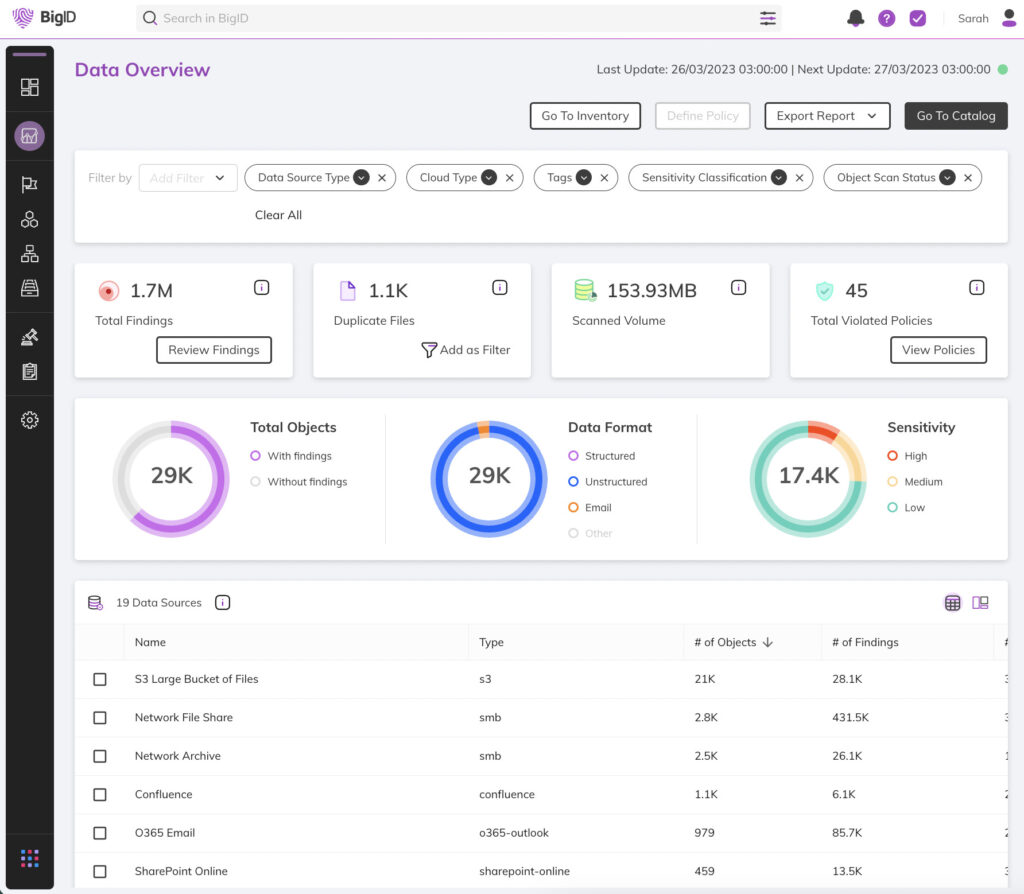
- Find and classify all of your data, everywhere
- Inventory your data by type, sensitivity, regulation, risk, and more
- Flag, tag, and label your data for more granular control
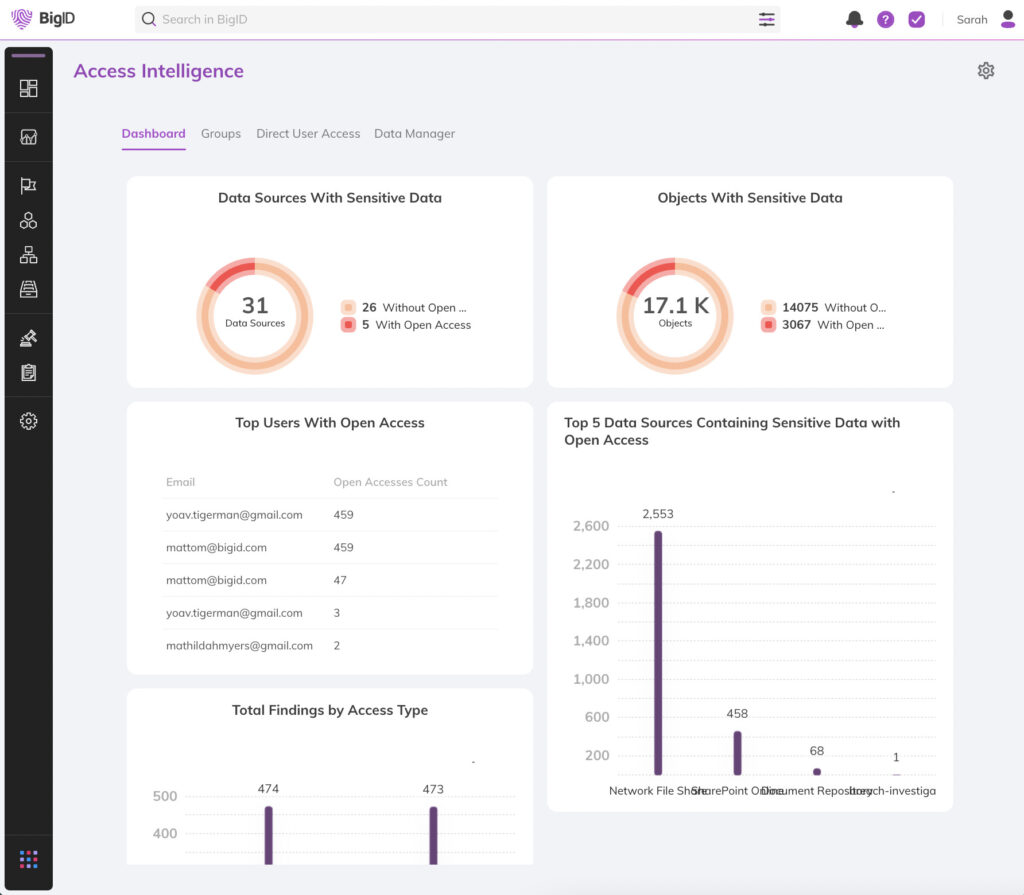
- Automatically find overexposed data & overprivileged users
- Reduce access on sensitive & high risk data
- Remediate over-permissioned users
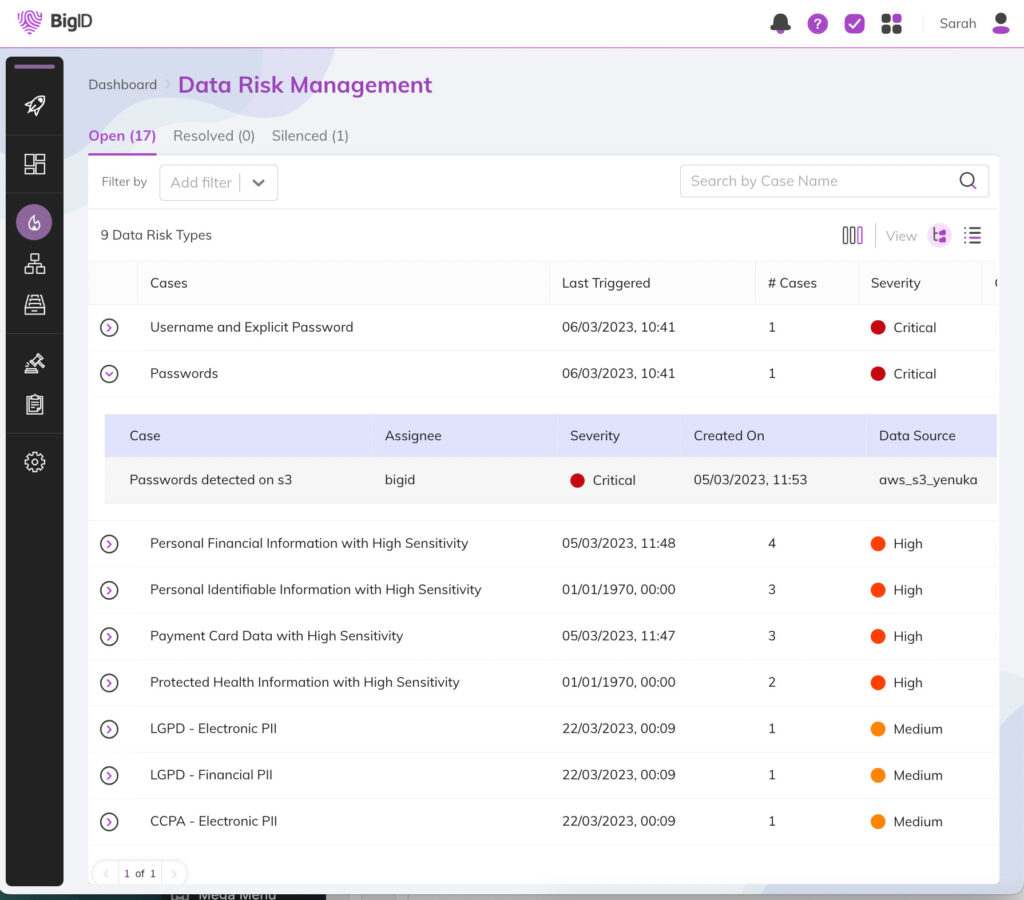
- Automatically identify risks in your environment
- Manage security alerts by case, policy, type and more
- Investigate, drill down, and resolve cases by severity
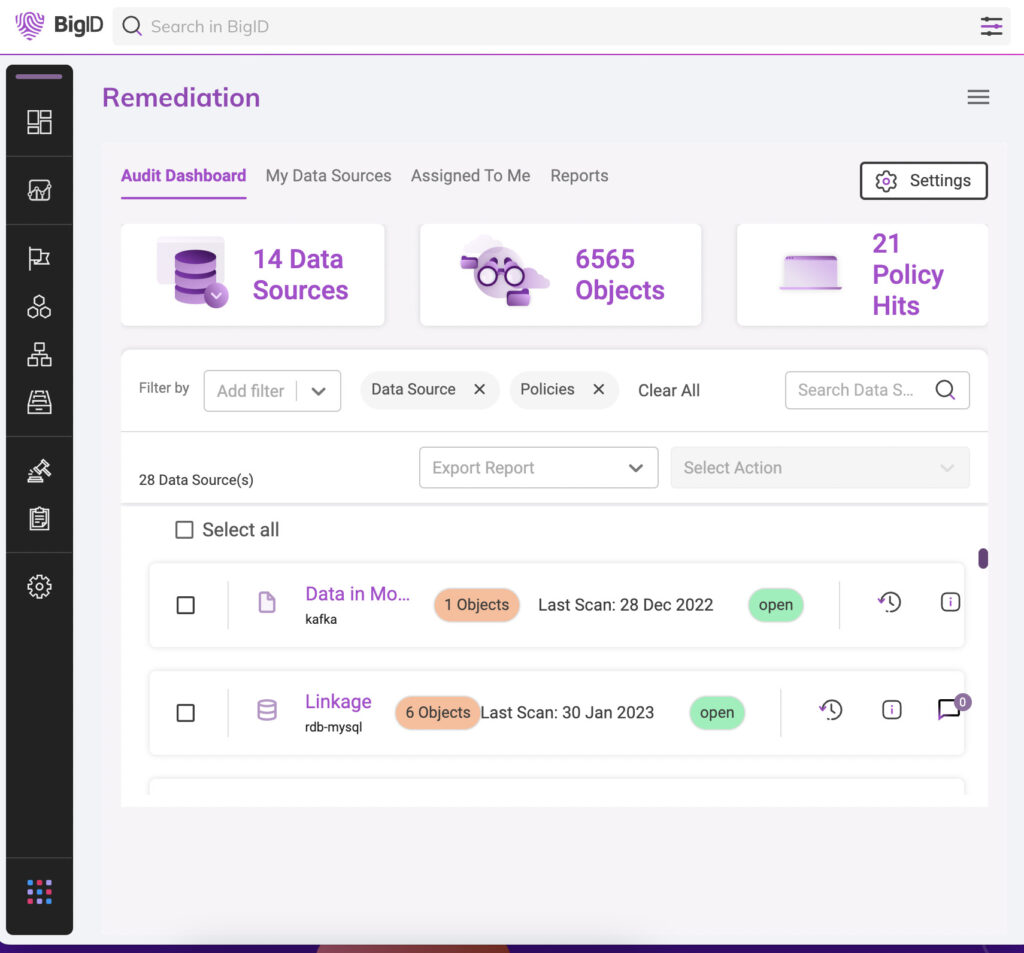
- Eliminate data exposure & protect your sensitive data
- Remediate data & access by sensitivity, type, policy, and more
- Reduce risk on overexposed data & overprivileged users
- Maintain an audit trail with advanced reporting to track progress