Imagine logging into your work email only to find a ransom note demanding tens of thousands in cryptocurrency. Panic sets in as you realize your company’s most important data has been encrypted – the culprit? A single exposed password, carelessly shared in a Slack chat, that unlocked your environment for cybercriminals. This scenario, unfortunately, is far from fiction. Loose credentials, like usernames and passwords, help bad actors wreak havoc through data breaches and ransomware attacks. Exposed secrets have been the source of some of the most prominent security incidents in recent news.
Secrets That Hide in Plain Sight
The term “secret” has often been used colloquially in IT and security circles but can be misunderstood. Think of secrets as any sensitive information that grants access to critical systems and data. This includes database passwords, API keys, encryption keys, and even seemingly innocuous details like user logins for collaboration tools. According to the 2022 Verizon Data Breach Investigations Report, compromised credentials were involved in a staggering 80% of breaches! The cost? An average of $4.24 million per incident.
In the quest for efficiency and teamwork, developer teams often keep static secrets and password-filled configuration files alongside their code. This practice is particularly common when multiple teams collaborate on different parts of an application. In DevOps, where speed and collaboration are key, code snippets containing secrets are frequently shared openly.
Where Do I Begin?
The most effective and optimal method for mitigating loose passwords and other secrets is through a proactive, automated, and comprehensive approach to data discovery and risk remediation. Due to the sheer size and scale of data and application environments today, it’s critical to be able to detect the secrets anywhere they could exist – whether that’s credentials within code repositories in GitHub, or a file containing usernames and passwords sitting on an on-prem SMB file share system. And then being able to take remediation actions against these secrets to quickly mitigate exposure risk before a bad actor can take advantage of them.

Know Your Data. Know Your Secrets
Protecting against loose passwords and secrets exposure starts with knowing your data. BigID’s the only solution that can give you complete data visibility and control across your entire environment – whether that’s in the cloud, or on-prem – across structured, unstructured, and semi-structured data.
With BigID, understand where your secrets live, what they are with context, and who’s got access to the data sources they reside in to mitigate the risk of a breach. Take action and implement the proper security controls and protective measures around secrets, as well as all other types of sensitive, regulated, and personal data.
Detect, investigate, and remediate secrets exposure across your entire environment, including:
- Support chat applications like Slack, Teams, Zendesk, and Salesforce.
- Code repositories like GitLab, GitHub, and Bitbucket to secure your development pipelines.
- Ticketing systems like Jira, and Confluence to ensure sensitive data doesn’t lurk within issue reports.
- Product design tools like Confluence and Adobe to protect intellectual property (IP) within design mockups.
- Email applications like Gmail and Outlook to identify accidental credential sharing.
- Documents to unearth secrets hidden in Google Docs, Microsoft Excel sheets, and more.
- Cloud storage to secure your data lakes across AWS S3, Google Cloud Storage, or Azure Blob.
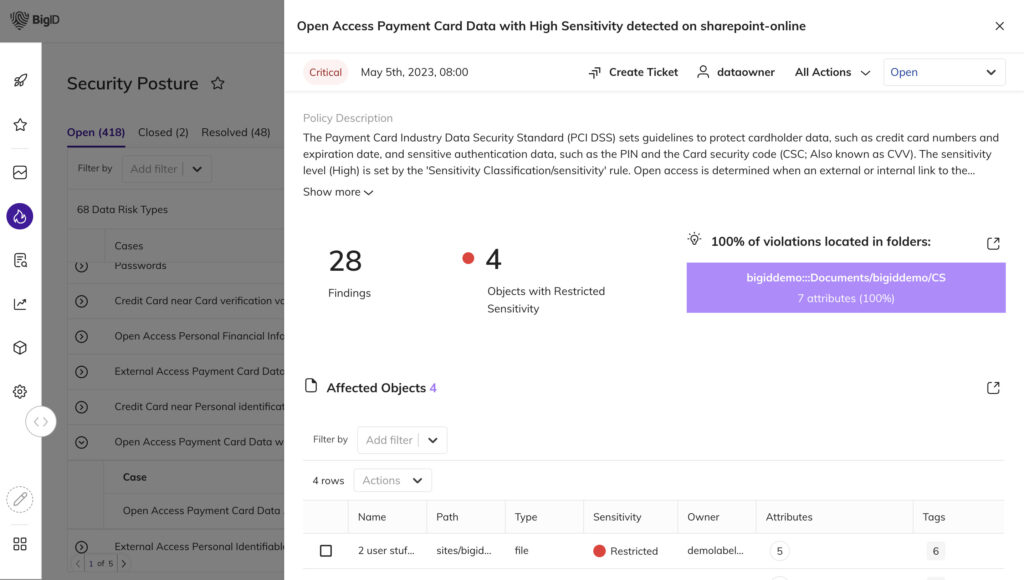
BigID provides your security team with a data-centric, risk-aware approach to effectively improve your security posture, streamline remediation, ensure compliance, shrink your attack surface, and ultimately reduce data risk.
Connect To Your Data Sources
With BigID, connect to and scan an unparalleled number of data sources across the entire environment. Connect to and scan mainframes, messaging, pipelines, big data, NoSQL, IaaS, on-prem SMB file shares, applications, and more, including everything across your dev stack. Scan unstructured data files and sources 95% faster with Hyperscan. Save time and avoid sensitive data blind spots across the cloud with Auto-Discovery, which other tools can’t provide.
Find Secrets & Sensitive Data with AI & ML Precision
Classify, categorize, flag, tag, and label more types of data, more accurately, at enterprise scale. Combine traditional pattern-matching techniques with BigID’s industry-leading ML and NLP-based classification to achieve unparalleled accuracy and scalability in data classification. Customize and fine-tune classifiers to find and classify specific types of secrets – whether they are API keys, tokens, certificates, passwords, and more. Classify, categorize, flag, tag, and label your data with accuracy, speed, and precision.
Create & Enforce Policies
Use pre-built sensitivity classification and security policies around detecting secrets across the environment and surfacing potential risks. Align these policies around compliance and frameworks such as NIST, CISA, and PCI, enabling effective management and protection of secrets and sensitive data. Track the location and movement of secrets and establish necessary controls for compliance.

Detect, Investigate, & Remediate Secrets Risks
Centralize detection, investigation, and remediation of critical secrets exposure and other data risks. BigID is the only solution to provide smarter data risk analysis by looking across various attributes around your data, including data type, regulation category, sensitivity level, metadata, relationship, similarity, identity, and more. Prioritize critical data risks by severity level according to sensitivity, location, accessibility, and more. Unique remediate data your way – centrally manage remediation workflows or decentralize them across your data security stack. Execute various remediation actions against secrets including encryption, deletion, masking, tokenization, and more.
Monitor & Assess Your Data Risks & Exposure
Consistently monitor for secret detection, identify potential insider threats, and conduct in-depth analysis. Leverage the industry’s first hybrid data risk assessments to get a complete overview of your most critical data risks across your entire environment (regardless of where that risk resides). Automatically generate concise yet comprehensive data risk reports covering posture, governance, and compliance to help foster ongoing awareness and enhance data-driven decision-making.
Want to learn more about how BigID can help your security team find and mitigate loose passwords and other secrets across your entire environment? Set up a 1:1 with one of our data security experts today!



