In an age of unprecedented data proliferation and stringent regulatory oversight, organizations in the Kingdom of Saudi Arabia (KSA) navigate increasingly complex National Data Management Office (NDMO) requirements. Compliance with these regulations is paramount for legal reasons, safeguarding sensitive information, and maintaining public trust.
Saudi Arabia’s NDMO has emerged as a critical player in ensuring data privacy, security, and governance. With regulations like the Saudi Data Governance Framework and the Personal Data Protection Law (PDPL), organizations must adopt a proactive approach to compliance. This article provides a roadmap for automating compliance with NDMO requirements, making the process efficient and effective.
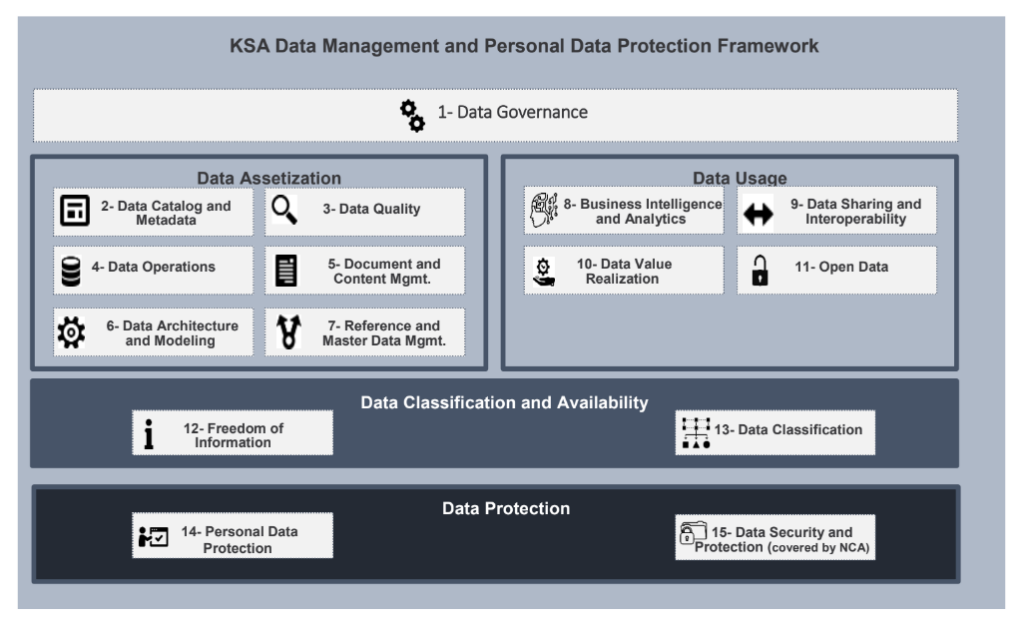
NDMO Data Management Guiding Principles
The NDMO framework aims to regulate the collection, processing, storage, and transfer of personal data by public and private organizations in KSA. This framework includes all individuals and entities that collect, process, store, or transfer personal data in KSA. The standards include controls and specifications across 15 Domains presented in the framework that spans the data lifecycle from creation, storage, movement, usage, and deletion.
How Does NDMO Define Personal Data
The most fundamental definitions of personal data according to the NDMO framework are as follows:
- Personal Data: Any element of data, individually or connected with other data, that would enable the identification of a Saudi Arabian citizen, such as name, address, credit card numbers, Saudi National Identity ID Number, health data, images, or videos of an individual.
- Processing Personal Data: Automated or manual processing and analysis of personal data, including collecting, transferring, documenting, storing, sharing, or deleting.
Understanding the NDMO Requirements
The NDMO plays a central role in overseeing and enforcing data protection regulations in Saudi Arabia. The key regulatory requirements organizations must address include:
- Data Protection: Safeguarding personal data’s confidentiality, integrity, and availability.
- Data Governance: Establishing clear data ownership, classifications, and data lifecycle management practices.
- Incident Reporting: Promptly reporting data breaches to the NDMO and affected individuals.
- Cross-Border Data Transfers: Complying with regulations when transferring data outside Saudi Arabia.
- Consent and Transparency: Obtaining informed consent from data subjects and providing transparency in the data processing.
- Data Rights Management: Provide mechanisms for data subjects to manage personal information, including requests for data access, correction, deletion of unnecessary data, and data portability.

8 Steps to Adopt the NDMO Framework
Automating compliance with NDMO requirements can streamline efforts, reduce human error, and ensure consistency. Here are eight steps to guide organizations towards compliance in Saudi Arabia:
- Data Discovery and Classification:
- Identify Data: Begin with a comprehensive data discovery process. Locate, catalog, and classify your organization’s personal, sensitive, and critical data.
- Automate Scanning: Utilize data discovery tools that automate the scanning and classification of data based on predefined policies and rules.
- Access Controls and Encryption:
- Implement Access Controls: Automate role-based access control to ensure only authorized personnel can access sensitive data.
- Data Encryption: Automate encryption for data at rest and in transit to meet security requirements.
- Incident Response Automation:
- Incident Detection: Deploy automated tools for real-time monitoring and detection of security incidents.
- Automated Alerts: Set up automated alerts that trigger when suspicious activities or breaches occur.
- Incident Reporting: Automate the reporting process, ensuring timely notifications to the NDMO and affected individuals.
- Consent Management:
- Consent Collection: Automate consent collection processes, allowing individuals to provide, update, or revoke consent easily.
- Documentation: Automatically maintain records of consent to demonstrate compliance.
- Data Lifecycle Management:
- Automated Deletion: Implement automated data deletion processes to ensure data is retained only for the necessary duration.
- Archiving: Automate data archiving to preserve information as needed for legal or business requirements.
- Cross-Border Data Transfers:
- Assessment and Approval: Automate the assessment of cross-border data transfers and seek automated approvals as necessary.
- Data Protection Assessments: Utilize automated tools to conduct privacy impact assessments (PIA) for such transfers.
- Compliance Monitoring and Reporting:
- Real-Time Compliance Monitoring: Deploy automated compliance monitoring solutions to continuously assess adherence to NDMO requirements.
- Automated Reporting: Generate automated compliance reports for internal monitoring and reporting to the NDMO.
- Employee Training:
- Automated Training Modules: Implement automated training modules for employees to ensure they are aware of their roles in compliance.
- Testing and Certification: Automate testing and certification processes to confirm that employees understand their responsibilities.
Meeting NDMO Standards with BigID
BigID is well-positioned to enable organizations to align with NDMO requirements to comply with the PDPL. BigID delivers unique capabilities for compliance with the NDMO framework and PDPL requirements. With BigID, an organization can:
- Discover and classify all impacted KSA data across the enterprise
- Map, inventory, and categorize KSA data by individual
- Operationalize data flow mapping and monitor privacy risk
- Leverage workflows to automate and validate end-to-end data rights fulfillment
- Execute data retention policies at scale
- Implement data minimization practices to reduce risk
- Conduct privacy risk assessments for security purposes
- Monitor and manage third-party data sharing
- Limit data access to unauthorized users
- Manage data breach investigation and response
Schedule a demo to see how BigID can help your organization navigate full compliance with NDMO requirements.
