Since it went into effect in 1996, the Health Insurance Portability and Accountability Act (HIPAA) has aimed to provide privacy rights for patients, protect patients’ sensitive and personal health data from threats and attacks, modernize the flow of healthcare data, simplify healthcare administration, and prevent healthcare fraud.
HIPAA provisions go through frequent updates to adapt to new technologies and changing conditions. Even companies that prioritize HIPAA compliance and the safeguarding of PHI — or “protected health information” — face multiple hurdles that require constant attention and the ability to take quick action on data procedures and practices.
In addition to frequent updates to the law, these challenges include constant attack threats on highly coveted data, interoperability issues, a gargantuan influx of patient data every day, and many more.
What Is HIPAA Compliance?
HIPAA is a federal regulation that pertains to organizations in healthcare and their affiliates and subcontractors. Regulated and enforced by the Department of Health and Human Services’ (HHS) Office for Civil Rights (OCR) — as well as some state governing bodies — HIPAA refers to these organizations as “covered entities.”
Covered entities may include:
- Health plans: Includes health insurance companies, health maintenance organizations, government programs that subsidize programs like Medicare, and military and veteran health programs.
- Healthcare providers: Includes hospitals, clinics, doctors, psychologists, dentists, chiropractors, nursing homes, pharmacies, home health agencies, and any provider that transmits health information electronically.
- Healthcare clearinghouses: Organizations that process nonstandard health information and convert data.
What Is Protected Health Information (PHI)?
Protected health information (PHI) is the term used by HIPAA to describe any information about an individual’s past or present health status or treatment that can be used to identify them. This includes all records, documents, and other information related to an individual’s diagnosis, payment history, care delivery processes, claims processing, claims adjudication and dispute resolution activities; clinical trial information; test results; mental health information; genetic information; biometric identifiers used for identification and much more.
The HIPAA Act requires every covered entity—which includes health plans and medical practices as well as any business involved with health care—to safeguard any PHI data that comes into its possession or control.
PHI data under HIPAA may fall under a different category of personal information under other regulations. For example, while a social security number may qualify as PII (personally identifiable information) under the EU’s General Data Protection Regulation (GDPR) and PI (personal information) under the California Consumer Privacy Act (CCPA), it would be considered a PHI identifier according to HIPAA.
To effectively handle sensitive data — particularly that which is covered by more than one regulation — organizations need to adopt technology that can automatically find, classify, map, and catalog all sensitive data and PHI across an entire data ecosystem, with comprehensive coverage of all data systems and sources.
BigID’s platform solution takes a machine-learning-based approach to automatically classify and tag all PHI, ePHI, HIPAA, and sensitive data — by regulation, document type, policy, attributes, individual, and more.
What Are the Three Rules of HIPAA?
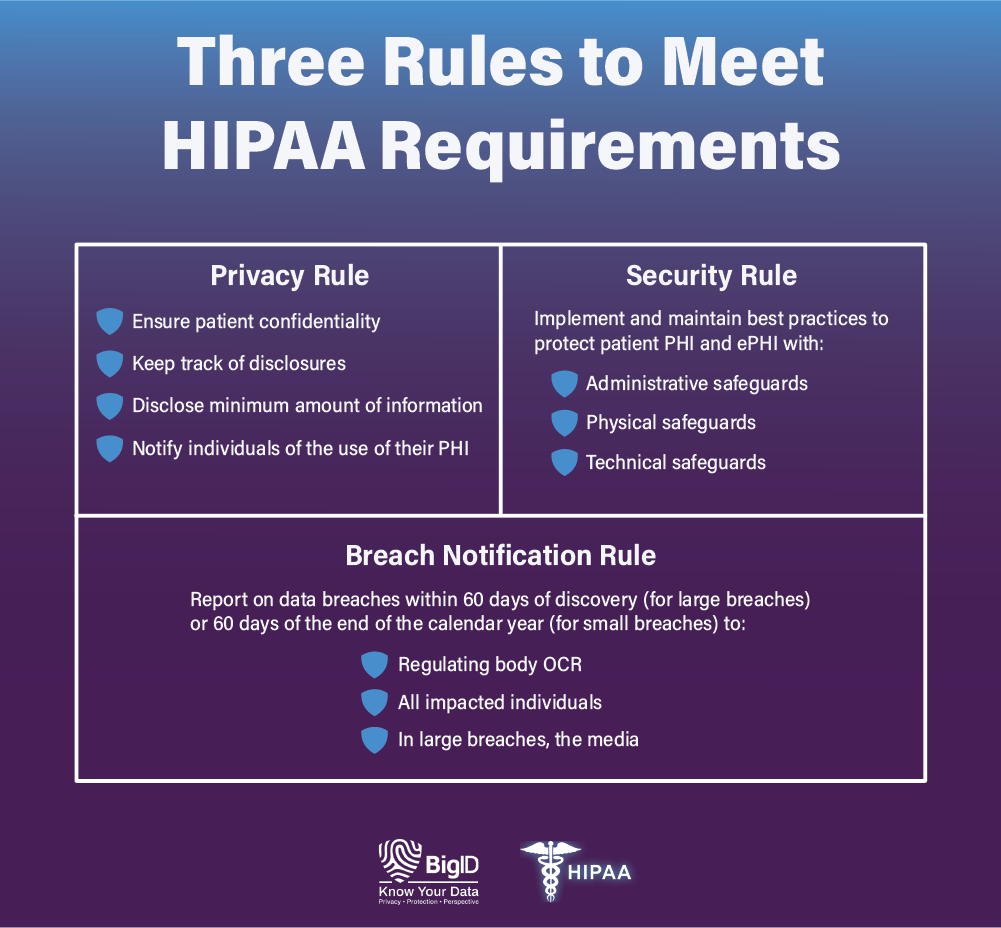
HIPAA Privacy Rule
The Privacy Rule under HIPAA gives individuals rights over their health information. Patients have the legal right to access and obtain copies of their health records — and request that inaccurate or outdated information be corrected.
The Privacy Rule also requires that covered health organizations take reasonable steps to ensure patient confidentiality, track disclosures, disclose only the minimum amount of information needed to perform a specific function, and notify individuals of the use of their PHI.
HIPAA requirements also state that covered entities must train staff on how to handle PHI — and appoint a privacy official to receive complaints about mishandled PHI.
While most disclosures require written authorization from the individual, HIPAA does allow for covered entities to disclose PHI without express consent in the cases of facilitating treatment, payment, or healthcare operations.
To properly disclose data to the right individuals at the right time while ensuring patient confidentiality, organizations need full coverage of all their data, everywhere.
BigID enables organizations to know their data — all of it, across all types, in any language, in the data center or the cloud, structured, or unstructured, at rest or in motion, at petabyte-scale — and enable workflows to delete redundant, obsolete, or trivial (ROT) data. This covers files and documents, images and mail, Big Data, and more — no matter how siloed, hidden, legacy, or hard-to-find the data is.
HIPAA Security Rule
The Security Rule under HIPAA covers three areas — and mandates that covered entities use best practices to safeguard PHI and ePHI (electronic protected health information) in the areas of:
- Administrative security: Covered entities must have written policies and procedures in place that clearly show how they comply with HIPAA — and these policies must cover everything from oversight, employee training, access controls, and the safe handling and monitoring of data they outsource to third parties. It also regulates the specific documentation of routine and event-based audits, as well as the use of contingency plans.
- Physical security: Covered entities must implement physical access controls and monitoring — including hardware and software removals and workstation security — to prevent unauthorized exposure of sensitive data. Physical safeguards extend to facility security plans, visitor and escort protocol, and contractor access — and include third-party training on physical access responsibilities and restrictions.
- Technical security: Covered entities must have technical safeguards in place to prevent unauthorized access of PHI that is transmitted electronically. This includes the maintaining of data integrity, authentication controls, and proper documentation and reporting practices — as well as the use of encryption on data transmitted over open networks.
In essence, the Security Rule mandates that organizations secure records, encrypt data, protect against breaches and malicious attacks, prevent the loss or theft of devices, train employees on sound security practices, secure PHI with third parties, and dispose of records when appropriate — among other requirements.
With BigID’s scalable and extensible data protection functionality, health organizations can reduce risk by effectively securing sensitive PHI across every Security Rule requirement — and leverage remediation workflows to take action on high-risk and overexposed data. Get high-level permission analysis around targeted datasets based on category and type, and monitor users with access to large, sensitive datasets.
HIPAA Breach Notification Rule
The HIPAA Breach Notification Rule requires that covered entities that experience a data breach report the incident. HIPAA requirements differ based on how many patients are affected.
- Breaches affecting 500 or more patients must be reported to the OCR, the impacted patients, and the media within 60 days of the breach being detected. These breaches are also publicly published by the OCR.
- Breaches affecting 499 or fewer patients must be reported to the OCR and the impacted patients within 60 days from the end of the calendar year in which the breach was detected.
BigID’s Breach Data Investigation app empowers healthcare organizations to determine the full scope of a data breach, know whose data was impacted, enact an incident response plan, and uphold reporting standards for both regulators and impacted individuals — all within the timeframes necessary for HIPAA compliance.
HIPAA Minimum Necessary Rule
This rule states that when disclosing protected health information (PHI), these organizations must take steps to limit the amount of information shared to the minimum necessary to accomplish the intended purpose of the disclosure.
In practice, this means that healthcare providers and other covered entities must make a reasonable effort to minimize the amount of PHI disclosed, whether it be in electronic or paper form. This is particularly important in today’s digital age, where personal information is easily shared and transmitted.
It’s essential for healthcare organizations to be aware of the HIPAA Minimum Necessary Rule and implement the necessary measures to ensure they are compliant and protecting their patients’ sensitive information.
2023 HIPAA Regulations Updates
The proposed changes to the HIPAA Privacy Rule include allowing patients to inspect their PHI in person, shortening the maximum time to provide access to PHI, limiting requests to transfer ePHI to a third party, allowing individuals to request their PHI be transferred to a personal health application, and requiring covered entities to inform individuals of their right to obtain or direct copies of their PHI.
Additionally, covered entities will be required to post estimated fee schedules for PHI access and disclosures, provide individualized estimates of fees for providing an individual with a copy of their own PHI, and respond to certain records requests when directed by an individual.
The requirement for written confirmation of the Notice of Privacy Practices has been dropped, and covered entities will be allowed to disclose PHI to avert a threat to health or safety under certain conditions. A minimum necessary standard exception has been added for individual-level care coordination and case management uses and disclosures.
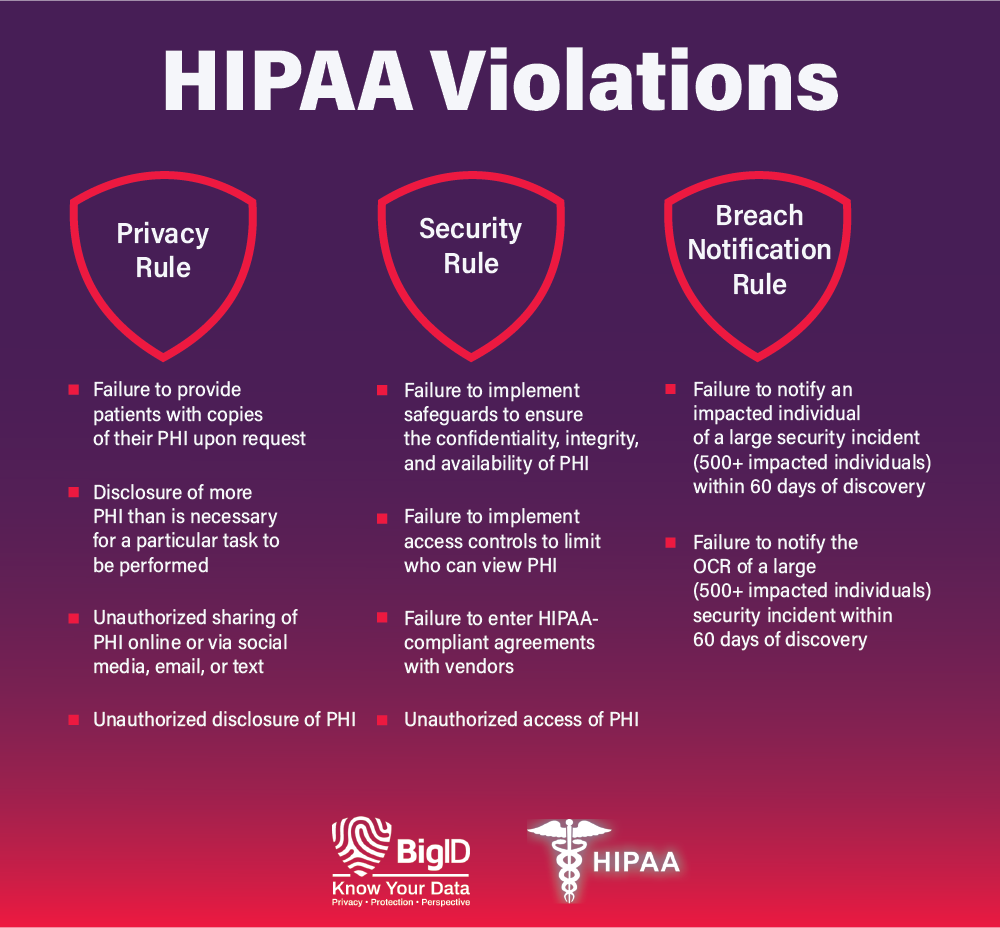
What Is Considered a Violation of HIPAA?
When covered entities fail to comply with one or more of HIPAA’s provisions, they can incur steep fines and penalties. HIPAA violations fall into four tiers that depend on:
- the severity of the offense
- the amount of harm caused by the violation
- the degree of willful neglect
- the company’s prior history with compliance
- other factors the OCR might deem relevant
Depending on the tier, financial penalties range from a minimum $100 penalty per violation to a $50,000 penalty per violation. There are hundreds of possible reasons for a violation, but some common ones include:
With BigID, health organizations can maintain detailed records of information systems and up-to-date info on audits — and be able to report on HIPAA compliance.
What Triggers a HIPAA Audit?
Internal audits and self-reporting uncover many HIPAA violations. Apart from that, the OCR — the main enforcing body of HIPAA — prioritizes the investigation of covered entities who report breaches of 500 or more records. The OCR also conducts periodic audits of HIPAA-covered entities and business associates.
State attorneys general may also investigate breaches. These investigations are often conducted due to complaints about potential HIPAA violations and in reaction to reports of breached of patient records.
BigID’s Approach to HIPAA Compliance
To achieve and maintain HIPAA compliance with regulations like the HIPAA Privacy Rule, HIPAA Security Rule, and HIPAA Breach Notification Rule, health organizations and their affiliates can implement a single data intelligence platform to gain full visibility into their data.
BigID’s data management platform — offers custom tailored, data discovery and scalable automation — enabling health organizations to begin meeting HIPAA requirements right now.
With BigID, you can:
Know your data: With BigID, companies can discover, manage, and catalog all of their sensitive PHI and ePHI across the entire organization — no matter how siloed — and enforce policy across all of their data, everywhere.
Get full data coverage: Companies need full visibility into all of their data — not just part of it. BigID provides broad coverage of unstructured, structured, and semi-structured data, big data, data in motion, and more — all in a single pane of glass.
Monitor data quality: Maintain a comprehensive map of all PHI — on-prem and in the cloud — alert on violation risks, and be able to report on all sensitive patient data for HIPAA compliance.
Reduce risk — everywhere: Reduce risk on PHI with risk scoring, flagging data flows and access patterns, and continuously monitoring file access.
Enable remediation: Quickly take action to remediate high risk data, sensitive, dark data, and all of your regulated health information.
Schedule a free 1:1 demo to see how BigID can empower your organization to achieve ongoing HIPAA compliance.