In today’s digital landscape, the fusion of sensitive data exposure and the formidable power of artificial intelligence has reshaped the battleground of cybersecurity. As we navigate this complex terrain, it’s evident that AI isn’t just a tool in the hands of cyber adversaries— it’s a catalyst for the evolution of data breaches. Read on to uncover how AI-driven innovations have transformed the methods and scale of data exposure.
What is Sensitive Data Exposure?
Today, more than ever, understanding sensitive data exposure is paramount to safeguarding the integrity of our information. Core aspects include:
Defining Sensitive Data and Its Significance
Sensitive data encompasses the crown jewels of information – personally identifiable information (PII), financial data, intellectual property, and more. It’s the backbone of businesses and individuals alike, holding immense value and importance.
Understanding Sensitive Data Exposure Attacks and their Tactics
Sensitive data exposure attacks are stealthy maneuvers orchestrated by cyber adversaries to access, steal, or compromise sensitive information. These attacks come in various forms, from phishing and malware to sophisticated hacking techniques. Their tactics evolve constantly, exploiting vulnerabilities in systems and human behavior.
Common Sensitive Data Vulnerabilities
Vulnerabilities are typically in abundance within most organizations. Understanding these vulnerabilities is crucial for building robust defenses against data exposure threats. Some contributors to the expanding surface area for potential breaches include:
- AI-Powered Intrusion: With the rise of AI, cybercriminals are leveraging advanced algorithms to breach systems, exploiting vulnerabilities with unprecedented speed and precision.
- Phishing Renaissance: AI-driven phishing attacks now mimic human behavior, making them harder to detect. These attacks often lure users into sharing sensitive information through deceptive emails, messages, or websites.
- IoT Vulnerabilities: The Internet of Things (IoT) devices collect vast amounts of data but often lack robust security measures. AI-enabled attacks can exploit these vulnerabilities to gain unauthorized access to sensitive information.
- Insider Threats Enhanced by AI: Employees or insiders with access to sensitive data pose a significant risk, especially when combined with AI tools that can swiftly navigate systems and bypass security protocols.
- Cloud Insecurity: While cloud services offer convenience, misconfigured settings or weak access controls can expose sensitive data to AI-driven attacks, leading to devastating breaches.
- Supply Chain Exploitation: AI algorithms can identify weak links in supply chains, allowing attackers to infiltrate trusted networks and access sensitive data through third-party vendors or partners.
- Deepfake Impersonation: Deepfake technology powered by AI can fabricate convincing audio or video recordings, leading to social engineering attacks where individuals are manipulated into divulging confidential information.
- Social Media Mining: AI algorithms comb through vast amounts of social media data, extracting personal information that can be exploited for targeted attacks or identity theft.

Impacts of Sensitive Data Exposure
In the wake of sensitive data exposure, organizations grapple with multifaceted repercussions that extend far beyond mere digits and bytes. Let’s explore the profound implications:
Financial Ramifications: Calculating the Costs of Breaches
From remediation efforts to regulatory fines, the financial toll of data breaches can be staggering. Every compromised record reverberates through balance sheets, prompting organizations to reevaluate their risk management strategies in the face of mounting expenses.
Reputational Damage: Effects on Trust and Brand Integrity
Trust, once shattered, is not easily regained. The erosion of consumer confidence can tarnish even the most resilient brands, underscoring the critical importance of safeguarding reputation in an era of heightened transparency and scrutiny.
Legal and Regulatory Consequences: Navigating Compliance Challenges
Navigating the labyrinth of legal and regulatory frameworks becomes an arduous task in the aftermath of a data breach. Non-compliance not only invites hefty penalties but also undermines organizational credibility, necessitating a proactive approach to compliance management.
Operational Disruption: The Toll on Business Continuity
As operations grind to a halt amidst the chaos of a data breach, the toll on business continuity becomes painfully evident. From disrupted workflows to compromised supply chains, the ripple effects of sensitive data exposure underscore the imperative of resilience and preparedness.
In essence, understanding the profound impacts of sensitive data exposure empowers organizations to fortify their defenses and mitigate risks, fostering a culture of resilience in the face of evolving threats.
.
Examples of Sensitive Data Exposure
No two industries are alike, and neither are their cybersecurity challenges. From healthcare to finance, each sector grapples with its own unique blend of regulatory requirements, threat landscapes, and operational constraints. Some examples across various industries include:
Incident: Hackers exploited a vulnerability in Equifax’s website, gaining access to sensitive personal information of approximately 147 million consumers.
Lessons Learned: This breach underscored the importance of timely patch management and robust cybersecurity measures. It highlighted the need for organizations to prioritize the security of customer data and invest in robust detection and response capabilities to swiftly mitigate breaches.
Marriott International Data Breach (2018):
Incident: Marriott disclosed a data breach affecting its Starwood reservation system, compromising the personal information of up to 500 million guests.
Lessons Learned: The Marriott breach highlighted the significance of due diligence during mergers and acquisitions, emphasizing the importance of integrating cybersecurity assessments into the due diligence process. It also underscored the need for organizations to monitor third-party systems and vendors closely to detect and mitigate potential risks.
In essence, exploring examples of sensitive data exposure offers a roadmap for navigating the tumultuous waters of cybersecurity. By distilling lessons from high-profile incidents, staying vigilant against emerging trends, and tailoring responses to industry-specific challenges, organizations can fortify their defenses and safeguard sensitive data in an ever-changing digital landscape.
The Role of AI in Sensitive Data Exposure
Unlocking the potential of artificial intelligence (AI) in the realm of sensitive data exposure heralds both promise and peril. Some of the ways AI can be used include:
Leveraging AI for Detection and Prevention
Harnessing the prowess of AI empowers organizations to stay one step ahead in the perpetual arms race against cyber threats. From anomaly detection to predictive analytics, AI augments traditional security measures, fortifying defenses with unprecedented agility and efficacy.
AI-Powered Threats: Understanding the Risks
Yet, as AI evolves, so too do the capabilities of malicious actors. AI-driven threats loom large on the horizon, wielding sophisticated tactics to exploit vulnerabilities and infiltrate fortified defenses. Understanding the nuanced landscape of AI threats is paramount to staying vigilant in an era of perpetual innovation.
Future Outlook: Anticipating AI’s Evolving Role in Data Security
Peering into the future, the trajectory of AI’s role in data security remains both exciting and uncertain. As AI algorithms grow ever more sophisticated, so too must our defenses evolve to meet the challenge. Anticipating the trajectory of AI’s evolution equips organizations with the foresight needed to adapt and thrive amidst shifting paradigms of cyber warfare.
The intersection of AI and sensitive data exposure offers a nuanced tapestry of opportunities and risks. By harnessing the transformative potential of AI while remaining vigilant against its inherent dangers, organizations can navigate the digital landscape with confidence and resilience.
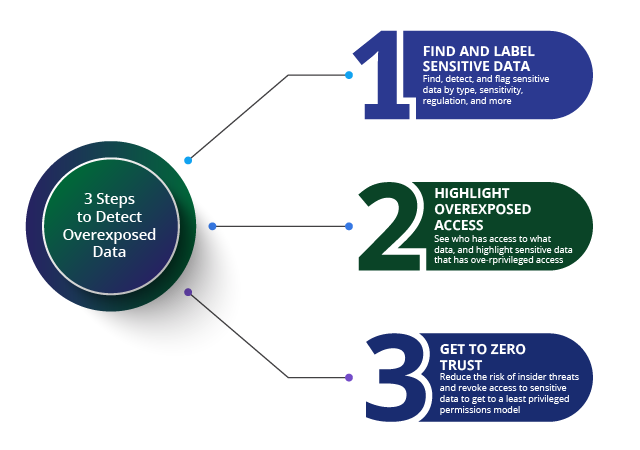
Mitigating Sensitive Data Exposure Risks
In the relentless battle to safeguard sensitive data, proactive measures stand as the cornerstone of defense. Best practices for mitigating risks include:
Implementing Robust Security Protocols and Best Practices
At the forefront of defense lie robust security protocols meticulously crafted to withstand the onslaught of cyber threats. From access controls to encryption standards, implementing best practices fortifies the digital fortress, erecting barriers against would-be intruders.
Employee Training and Awareness: Strengthening the Human Firewall
In an era where human error ranks among the greatest vulnerabilities, empowering employees with knowledge becomes paramount. Through comprehensive training and heightened awareness, individuals transform into the first line of defense, bolstering the human firewall against social engineering and phishing attacks.
Adopting Advanced Technologies: From Encryption to Behavioral Analytics
Embracing the vanguard of technological innovation unlocks new avenues for fortifying sensitive data against intrusion. From robust encryption algorithms to cutting-edge behavioral analytics, advanced technologies stand poised to revolutionize data security, offering insights and protections previously unimaginable.
Mitigating the risks of sensitive data exposure demands a multifaceted approach that combines technological prowess with human vigilance. Organizations can navigate the digital landscape with confidence and resilience by embracing proactive measures and fostering a culture of security consciousness.
BigID’s Proactive Approach to Sensitive Data Protection
For organizations looking to stay up to date with emerging cyberthreats— BigID has your back. Our data-centric approach to security combines deep data discovery, next-gen data classification, and risk management. Know where your data is located, how sensitive it is, and who’s accessing it to protect your enterprise’s most valuable assets
With BigID you can:
- Know Your Data: The ability to identify your data is the first critical step for protecting sensitive data. In order to reduce risk, organizations need to identify all their data, everywhere. BigID’s data discovery and classification helps organizations automatically identify their sensitive, personal, and regulated data across the entire data landscape.
- Data Classification: Classify all data, everywhere in order to meet compliance for data privacy and data protection. Classify by category, type, sensitivity, policy, and more with BigID’s advanced data classification capabilities.
- Reduce Risk: Manage access to sensitive and critical business data – organizations need to incorporate access control to identify who has (and who shouldn’t have) access to sensitive data. BigID’s Access Intelligence App helps organizations identify and remediate high-risk data access issues with ML-based insight to identify and prioritize file access risk.
- Incident Response: When incidents happen, every second counts. BigID’s identity- aware breach analysis effectively assesses the scope and magnitude of a data breach. Quickly determine which users and personal data have been compromised and respond accordingly. Read more about data breach prevention here.
To see how BigID can bolster your security program and help you start protecting your enterprise data— schedule a 1:1 demo with our experts today.