With cyber threats rising, data is at risk. That is why organizations need robust and proactive approaches to safeguard their valuable data. Data Security Posture Management (DSPM) is one such solution that has emerged.
DSPM provides data-centric security and protects sensitive information wherever it resides — whether the data is stored on-premise in a single data store, scattered among several repositories, or in hybrid and multi-cloud environments.
This comprehensive DSPM guide will explain the fundamental aspects of DSPM, how it works, its key capabilities, benefits, and best practices. Moreover, we will explore how it fits within the broader cloud security landscape, comparing it with Cloud Security Posture Management (CSPM), and outlining essential considerations for successful DSPM implementation.
What is Data Security Posture Management (DSPM)?
The term ‘DSPM’ was coined by Gartner in April 2022. It refers to an advanced approach designed to help organizations manage and enhance their security posture across diverse cloud environments and data stores. DSPM proactively identifies and remediates security vulnerabilities, misconfigurations, and potential threats to sensitive data.
This groundbreaking approach encompasses “Discovery Plus,” a fusion of data discovery and security management capabilities.
DSPM helps organizations of all sizes manage data security risks across their complex environments.
Risk management is central to DSPM. Security and risk management leaders must effectively identify, understand, and remediate data security risks. As data becomes increasingly valuable and vulnerable, a robust strategy to assess and mitigate these risks is essential.
How Does DSPM Work?
DSPM vendors use a combination of automated tools, intelligent algorithms, and data monitoring capabilities. These tools continuously scan and assess your data infrastructure to evaluate security configurations, access controls, and potential risks. They analyze data movement, access patterns, and user behavior to provide insights that help strengthen your overall security posture.
This process functions as a dynamic shield for your organization’s sensitive data assets. It combines automated tools, intelligent algorithms, and advanced data monitoring capabilities.
At its core, DSPM acts as a vigilant sentry. It scans and assesses your data infrastructure with precision. It conducts thorough evaluations of security configurations, access controls, and potential risks.

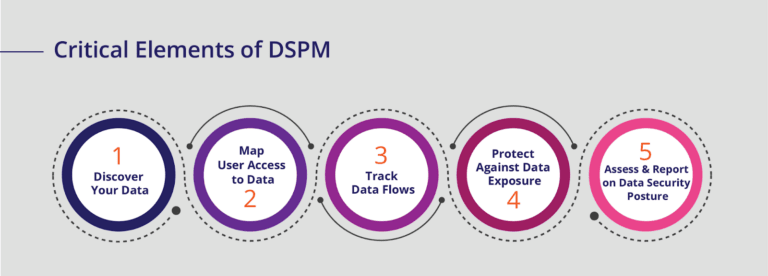
Key Capabilities of DSPM
As a security and risk leader, you should look for a DSPM solution that meets certain essential requirements. Some of those critical DSPM capabilities include:
Find, classify, and map sensitive data across your environment:
- Automatically discover, tag, and inventory unstructured, structured, and semi-structured data across all environments.
- Covers both on-premises and cloud environments in a single view.
Get a 360° view of data:
- Uncover all types of data, known and unknown, as well as hidden cloud data.
- Identify duplicate, similar, redundant, obsolete, and trivial (ROT) data.
- Detect sensitive and critical data like regulated data, secrets, intellectual property, and business data.
Identify potential access & exposure risks:
- Understand data access permissions for different users.
- Monitor data sharing both internally and externally.
- Utilize access intelligence to reduce insider risks, accelerate zero trust, and achieve least privilege.
Alert on high-risk vulnerabilities and critical issues:
- Automatically trigger alerts based on risk levels and policy violations.
- Detect insider risks and accelerate investigation processes.
- Enable security teams to investigate, resolve, and track security alerts efficiently.
Easily report and assess risk:
- Conduct data risk assessments to understand the risk posture.
- Provide granular and high-level reporting on crown jewel data regularly.
- Monitor progress and improvements in risk posture over time.
Take action:
- Offer guidance on remediating identified risks.
- Automate, guide, and orchestrate remediation for high-risk data.
- Trigger alerts based on relevant activity without causing unnecessary noise.
Be enterprise ready:
- Provide enterprise-grade security and scan management.
- Ensure minimal disruption to business operations.
- Offer granular Role-Based Access Control (RBAC) and scope down roles.
- Support iterative scanning and seamless integration with existing tech stack.
Benefits of DSPM
DSPM is quite important in today’s digital landscape. It offers several invaluable benefits to organizations of all sizes. It improves the security posture of the data with enhanced data protection and features that ensure the confidentiality, integrity, and availability of critical information.
It uses deep data discovery and classification, access controls, and real-time monitoring to mitigate the risk of, and prevent data breaches and unauthorized access. Coupled with proactive risk management capabilities, continuous monitoring, and analysis, DSPM helps your business identify potential vulnerabilities and security gaps. You can then take preemptive measures to protect your data and ensure it is protected before threats materialize.
Compliance assurance is yet another area where DSPM can be useful. It helps your business navigate the complexities of data security regulations and standards so you can avoid potential penalties and reputational damage.
Additionally, DSPM streamlines operations and reduces costs by automating security processes to free up valuable resources for strategic initiatives.
DSPM: Data-centric Security
DSPM acknowledges that data is the most critical asset and ensures its protection across different cloud platforms and applications. It focuses on protecting the data within rather than just the perimeter.
Instead of relying solely on the traditional “castle and moat” approach, which might still leave the data vulnerable inside, data-centric security places a protective layer around the sensitive data, making it resilient to potential attacks.
Adopting a data-centric security strategy allows your organization to shift focus from building stronger and more fortified outer defenses to implementing robust controls and secure access protocols for data. Only authorized individuals can access sensitive information, which mitigates the risk of data breaches and unauthorized disclosure.
How DSPM Fits in the Greater Cloud Security Landscape
DSPM complements other security strategies, such as CSPM. These two approaches work synergistically to provide comprehensive protection.
CSPM monitors and assesses the configuration and compliance of cloud resources to minimize potential misconfigurations and vulnerabilities. It ensures that cloud services and applications are deployed in alignment with industry best practices, and security and compliance standards.
By examining cloud infrastructure from a holistic perspective, CSPM reduces the risk of security breaches that could stem from configuration errors or inadequate access controls.
On the other hand, DSPM prioritizes safeguarding the core asset of cloud environments— data. It addresses the data security challenges in the cloud, including privacy, access controls, encryption, and data lifecycle management.
DSPM’s granular approach empowers your organization to enforce data-centric security policies, where only authorized users can access sensitive information and that data remains protected even in the event of unauthorized access attempts.
DSPM, CSPM, or Both?
While both DSPM and CSPM are essential for robust cloud security, organizations need to understand their specific requirements and risk profiles to determine the ideal mix. If data protection is a top priority, integrating DSPM with existing CSPM practices would create a comprehensive and effective security posture.
Combining these two approaches helps your organization create a cohesive cloud security ecosystem that fortifies the infrastructure and the data it hosts.
This harmonious integration not only minimizes the risk of data breaches but also facilitates compliance with various data protection regulations.
Advantages of DSPM Solution Over Other Approaches
Real-time Protection
DSPM focuses on real-time protection. It uses continuous monitoring and real-time alerts to stay one step ahead of emerging threats. Instant response to potential security incidents significantly reduces attackers’ window of opportunity.
DSPM restricts access to sensitive data to minimize the risk of data breaches and limit potential damage. This proactive approach to security ensures that potential threats are detected and addressed before they escalate into major security incidents.
Holistic Data Visibility
DSPM fortifies your organization’s data security posture with granular insights into data movement, access patterns, and usage. This comprehensive data visibility ensures that there are no blind spots in data security. You know where sensitive data resides, who has access to it, and how it is being used. This level of visibility empowers your security team to identify potential security gaps and take proactive measures to secure data assets effectively.
With this complete picture, your organization can implement targeted security controls and ensure that data is adequately protected across the entire infrastructure.
Automated Remediation
DSPM’s automated remediation capabilities set it apart from traditional security approaches. They streamline security processes and reduce the potential for human errors. When security incidents are detected, DSPM can automatically trigger predefined actions or remediation steps. This saves valuable time and effort for security teams and assures consistent and swift responses to security incidents.
Challenges of Implementing Data Security Posture Management
While DSPM offers robust data security, it also comes with implementation challenges that organizations need to address to fully leverage its potential benefits:
Data Complexity
Organizations often deal with data across all environments, such as various cloud platforms and on-premises systems. Managing and protecting this vast amount of data can be complex and challenging.
The right DSPM solution should be capable of handling diverse data types, formats, and locations while ensuring consistent security policies across your entire data landscape. Data classification, mapping, and discovery become critical components to streamline data management and security efforts.
Integration with Existing Systems
Integrating DSPM can be difficult for organizations with legacy security systems. You need seamless interoperability between DSPM and existing security solutions for a unified and cohesive security ecosystem.
This integration may require careful planning, testing, and adjustments to ensure that data security measures are not disrupted during the implementation process. You must also consider how DSPM will interact with your current security incident response processes to facilitate a smooth transition.
User Adoption
The success of any security initiative relies on user buy-in and compliance. Encouraging users to embrace data security best practices and adhere to DSPM policies can be a significant challenge. Employees may perceive data security measures as cumbersome and hindering productivity, which leads to potential resistance to change.
To overcome this challenge, you should invest in user education and training programs to raise awareness about the importance of data security. You could also use incentives, rewards, and gamification strategies that motivate employees to follow best practices and adopt DSPM policies willingly.
DSPM Best Practices
To maximize the benefits of the data-centric security approach, organizations should adopt the following best practices:
Define Clear Security Policies
Develop and implement clear and comprehensive data security policies for a successful data-centric security strategy. Your organization must define precise guidelines on data classification, access controls, encryption, and data handling.
These policies should align with the overall security objectives and comply with relevant industry regulations and data protection laws. By establishing well-defined security policies, you can create a consistent and unified framework for safeguarding sensitive data throughout its lifecycle.
Regular Assessments
Regular security assessments and audits help identify potential vulnerabilities, weak points, and gaps in the data security posture.
These assessments should encompass both technical evaluations of security tools and processes and evaluations of employee adherence to security policies.
Employee Training
Employees play a pivotal role in data security, and their awareness and adherence to best practices are vital for the success of the data-centric security approach.
Educate employees about the significance of data security and their role in safeguarding sensitive information with ongoing training and awareness programs. Training sessions could cover topics such as data handling procedures, recognizing phishing attempts, understanding the importance of data classification, and the proper use of data security tools.
Encourage Accountability and Ownership
Data security is a collective responsibility that involves everyone in the organization. Encourage a culture of accountability and ownership of data security, where every individual understands their role in protecting sensitive information.
Managers and leaders should adhere to security policies to set an example and promote a strong security mindset within their teams. They should also encourage open communication about security concerns, so that employees feel comfortable reporting security incidents or potential risks.
DSPM and Dynamic Monitoring
Dynamic monitoring continuously observes and analyzes data-related activities, access patterns, and security events as they happen. This real-time analysis empowers your organization to detect and respond to security incidents swiftly to prevent potential data breaches and unauthorized access attempts.
This monitoring provides a comprehensive view of your data security landscape by monitoring data movements, access permissions, and usage patterns. It enables you to adapt to rapidly evolving data environments and emerging threats, and stay ahead of potential risks and protect data effectively.
DSPM Use Cases
- Insider Threat Detection: DSPM plays a crucial role in detecting and mitigating insider threats within an organization. Insiders with legitimate access to data can pose significant risks by intentionally or accidentally mishandling data or attempting unauthorized access. By continuously monitoring data access and usage, DSPM can promptly detect and prevent unauthorized access, data exfiltration, or potential insider threats.
- Data Loss Prevention: Data leaks can occur due to various factors, such as human errors, system misconfigurations, or malicious activities. DSPM solutions are designed to prevent accidental or intentional data leaks by setting up robust policies and access controls. These policies can restrict the transfer or sharing of sensitive information outside the organization’s secure environment. DSPM also employs encryption and data classification mechanisms to ensure that sensitive data remains protected at all times, reducing the risk of data loss.
- Cloud Migration Security: As more organizations embrace cloud computing, securing data during the migration processes becomes important. DSPM solutions assess the security posture of the cloud environment, verify compliance with relevant regulations, and monitor data transfers to prevent unauthorized access or exposure. They also facilitate secure data migration by adequately encrypting sensitive information to protect it throughout the migration journey.
Getting Started with BigID
BigID is the leader in Data Security Posture Management (DSPM), recognized by CB Insights for its groundbreaking approach to data security. It pioneers cloud-native security for multi-cloud and hybrid cloud environments, offering a comprehensive data-first solution for data visibility and control.
With years of R&D and customer collaboration, BigID’s platform seamlessly drives security from a data-risk standpoint.
Key features that differentiate BigID’s DSPM include comprehensive data coverage in cloud and on-premises environments, accurate risk management with patented ML and customizable tuning, remediation tailored to your preferences, and scalable data security that involves the right people across the business.
To start fortifying your organization’s most critical data and embrace the power of DSPM— get a 1:1 demo with BigID today.



