As our IT environments continue to increase in size, complexity, and heterogeneity, the challenge to protect and secure our most critical and sensitive data assets becomes increasingly difficult. There’s no silver bullet solution — but a variety of methods to cover your bases when protecting your environment from malicious activity or accidental exposure.
At BigID, we pride ourselves on working with the leading data security technology providers — as well as those within data privacy and governance — to help our customers maintain a strong security posture across their environment.
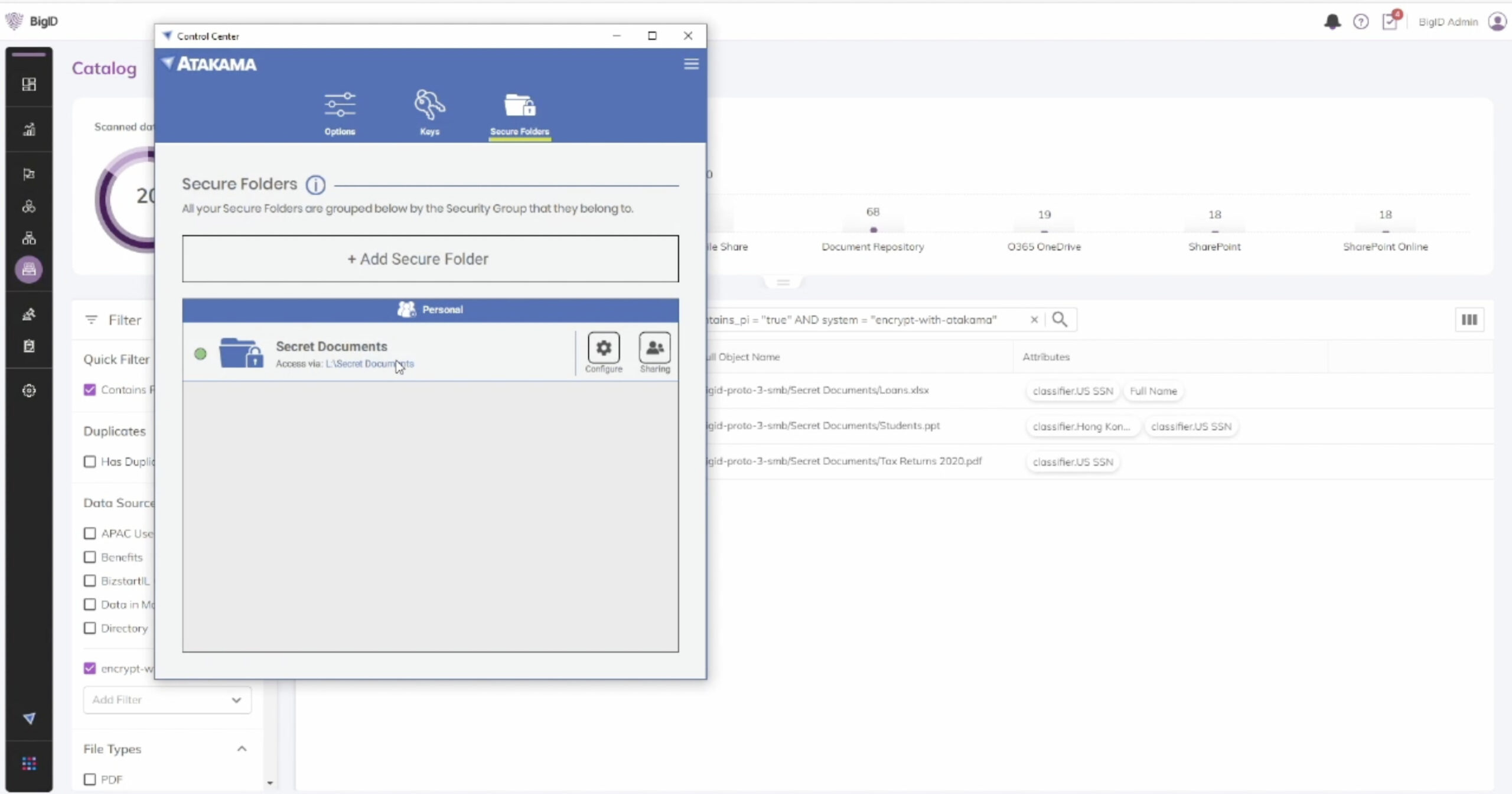
Today, we’re happy to announce the availability of our integration with Atakama. Atakama is one of several integral partners who are building applications on top of the BigID platform for publication on the BigID App Marketplace. The marketplace is geared toward helping our customers enrich, augment, and solidify their end-to-end data security strategy through seamless integrations and partnerships.
One area where traditional data security misses the mark is understanding which data requires which level of protection. BigID provides the data intelligence needed to enable the appropriate level of encryption based on the actual sensitivity or criticality of the data; not of the opinion or intuition of an end-user.
Alongside Atakama, this integration enables organizations to apply adequate safeguards around their data, proactively manage risk, and maintain compliance. The joint solution helps mitigate user error by leveraging BigID’s unparalleled data classification and identification accuracy — plus enabling appropriate controls with Atakama’s innovative multi-factor encryption and distributed key architecture optimized around a data asset’s level of sensitivity. Per defined policies, Atakama protects files by automatically applying file-level encryption without relying on usernames or passwords.
BigID helps organizations of all sizes to manage, protect, and get more value out of their data anywhere it exists — on-prem or in the cloud. Understand the power of these new partnerships for your data security stack. Get a 1:1 demo with our experts to see it in action today.


