For more than a decade, Data Loss Prevention (DLP) has been positioned as the last line of defense against data breaches. Yet heading into 2026, most security leaders quietly acknowledge the truth: traditional DLP no longer matches how data is created, accessed, and exposed.
Cloud-first architectures, SaaS sprawl, AI-driven access, and unstructured data growth have fundamentally changed the problem. The result? A widening gap between traditional DLP vs modern DLP, and a growing shift toward DSPM, data discovery at scale, and AI-driven context as true DLP alternatives.
Legacy DLP can’t see the modern data landscape. DSPM + discovery + automation delivers the visibility and control security leaders actually need.
This article explains:
- Why legacy DLP tools aren’t effective in 2026
- What modern data protection actually looks like today
- Which technologies replace DLP
- How DSPM + discovery + context-aware intelligence outperform traditional prevention models
What Traditional DLP Was Built to Do
Traditional DLP emerged in a very different era of security. Its core assumptions were simple:
- Data lives in known locations (endpoints, email, network gateways)
- Sensitive data can be identified with signature-based policies
- Blocking or alerting on data movement prevents loss
At its core, traditional DLP relies on:
- Deterministic detection (exact matches, regex, fingerprints)
- Static policy rules
- Inline prevention controls (block, quarantine, encrypt)
This worked reasonably well when data flows were predictable and infrastructure was centralized.
But those assumptions no longer hold.
Why Legacy DLP Isn’t Effective in 2026
1. Data Has Escaped the Perimeter
Modern organizations operate across:
- SaaS platforms
- Cloud data stores
- Collaboration tools
- AI copilots and third-party integrations
Data loss prevention in the cloud is no longer about stopping files at a gateway. Data is accessed directly via APIs, identities, and applications—often without ever “moving.”
Traditional DLP can’t protect what it can’t see.
2. Signature-Based Policies Don’t Scale
Legacy DLP depends heavily on signature-based policies:
- Regex for PII
- Static classifiers
- Predefined content patterns
These approaches break down when:
- Data is semi-structured or unstructured
- Context determines sensitivity
- The same data is sensitive in one use case and harmless in another
This is the core limitation of deterministic vs. context-aware detection. Deterministic rules are brittle; modern environments are not.
3. Alert Fatigue Replaces Real Risk Reduction
Most DLP programs fail not because they miss alerts—but because they generate too many.
Security teams face:
- Thousands of low-confidence alerts
- Little clarity on blast radius or exposure
- Manual triage with no prioritization
Without context-aware risk scoring, DLP becomes noise rather than protection.
4. DLP Was Never Built for Unstructured Data Governance
Today, the majority of sensitive data lives in:
- Documents
- Spreadsheets
- Chat messages
- Wikis
- Code repositories
Traditional DLP was not designed for unstructured data governance at scale. It lacks:
- Ownership awareness
- Business context
- Lifecycle visibility
Blocking data doesn’t fix data sprawl.
What Modern Data Protection Looks Like in 2026
Modern data protection flips the DLP model entirely.
Instead of asking:
“Can we block this action?”
Security leaders now ask:
“Why is this data exposed, who can access it, and what’s the real risk?”
Core Principles of Modern DLP
Modern DLP is not a single tool—it’s a strategy built on visibility, context, and automation.
It includes:
-
Data discovery at scale across cloud, SaaS, and AI surfaces
-
Identity-aware security that ties access to real users and roles
-
Continuous risk assessment, not point-in-time blocking
-
Policy automation instead of static rule management
This is where DSPM becomes foundational.
From Traditional DLP to Modern Data Security: Why DSPM is Foundational
Traditional DLP: Control the Exit
DSPM: Reduce the Exposure
DSPM (Data Security Posture Management) focuses on:
- Where sensitive data exists
- Who can access it
- Whether access is excessive, risky, or unnecessary
- How exposure changes over time
DSPM fills the critical gaps traditional DLP misses—delivering real-time visibility, risk prioritization, and automated action.
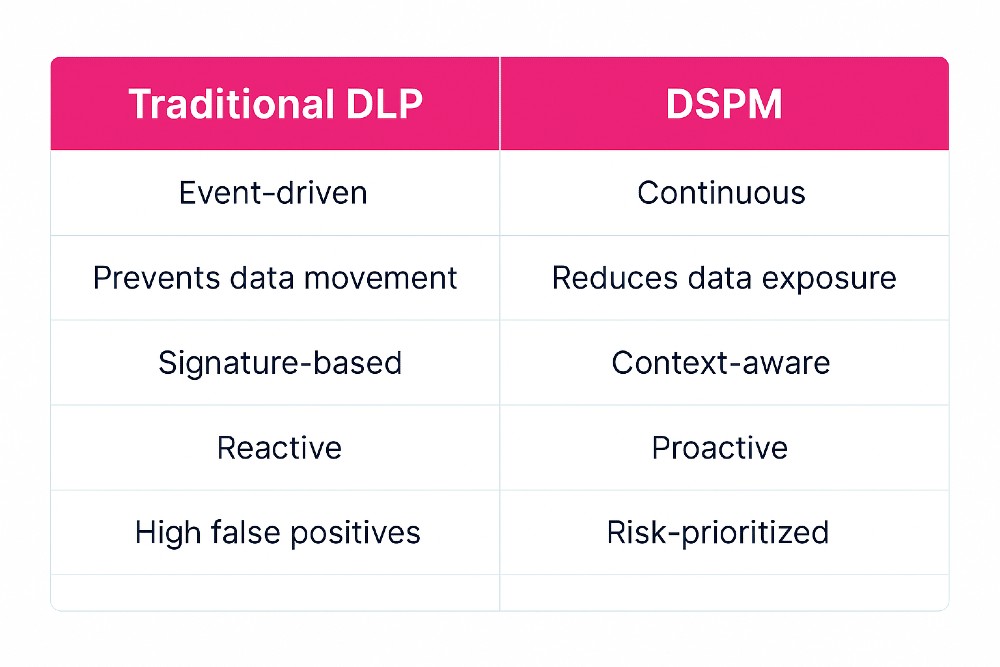
DSPM addresses the root cause of breaches: overexposed data, not just data in motion.
Technologies Replacing DLP in 2026
Modern organizations are adopting DLP alternatives in 2026 that align with how data actually works.
1. DSPM + Data Discovery at Scale
Modern tools continuously discover:
- Structured and unstructured data
- Shadow data stores
- Forgotten and orphaned data
BigID’s discovery platform surfaces sensitive, regulated, and toxic data across all environments to enforce zero trust data principles.
2. Identity-Aware Security
Instead of blocking files, modern data protection evaluates:
- Who is accessing the data
- From where
- Under what role or privilege
- Whether access is justified
BigID delivers this across SaaS sprawl, contractors, machine identities, and agentic AI—providing real-time insight into who has access and whether it’s justified.
3. AI-Driven, Context-Aware Detection
Modern systems move beyond deterministic detection toward:
- Behavioral analysis
- Business context
- Sensitivity in use, not just content
BigID goes beyond classification—leveraging business context and behavioral analytics to surface high-impact risk, not just anomalies.
4. Automated Remediation Workflows
Instead of endless alerts, modern platforms trigger:
- Permission right-sizing
- Public link removal
- Ownership reassignment
- Policy-based remediation workflows
BigID automates critical workflows—like permission right-sizing and ownership reassignment—so security teams can act at scale with precision and speed.
The Role of AI in Modern DLP
AI doesn’t just classify data—it changes how data is accessed.
With copilots, agents, and autonomous workflows:
- Data is queried, summarized, and reused dynamically
- Access is indirect and continuous
- Traditional DLP controls are bypassed entirely
Modern data protection platforms are designed for:
- AI-aware access patterns
- Continuous permission evaluation
- Risk assessment for agentic AI data access
BigID is built to secure this new paradigm—evaluating dynamic access patterns and mitigating AI-related risk continuously, not just reactively.
Legacy DLP simply cannot operate at this layer.
Rethinking “Prevention” in Data Loss Prevention
The biggest mindset shift in traditional DLP vs modern DLP is this:
Prevention no longer means blocking events.
Prevention means eliminating unnecessary exposure.
By:
-
Discovering sensitive data everywhere
-
Enforcing zero trust data principles
Modern organizations prevent breaches before a violation ever occurs.
Modern data protection also supports compliance with evolving frameworks like NIS2, DORA, and the EU AI Act—by ensuring continuous visibility, auditability, and risk control.
Final Takeaway: DLP Isn’t Dead—But It Has Been Replaced by Strategy
Traditional DLP hasn’t failed because security teams misused it.
It failed because the data landscape changed faster than the model.
In 2026, modern DLP is no longer a standalone prevention tool. It’s the outcome of:
- DSPM
- Data discovery at scale
- Identity-aware security
- Context-aware, AI-driven intelligence
- Automated remediation
For CISOs, CIOs, and data protection leaders, the question is no longer “How do we tune DLP?”
It’s:
“How do we protect data everywhere it lives—before it’s ever lost?”
That’s the future of modern data protection.
Ready to replace outdated prevention with real protection? Schedule a demo to see how BigID can modernize your DLP strategy—built for where data lives and how it’s used today.