SecOps tools lack visibility to data context and risk, yet increasing security events & decreasing personnel to address them make prioritizing the relevant data analysts have to filter through the noise to remediate the most impactful issues.
What we need is automation and better correlation with existing data sets. Most SIEM/SOAR solutions understand devices, networks, UEBA— but not data context.
BigID’s data intelligence platform enables organizations to know their enterprise data and take action for privacy, security, and governance.
Splunk helps organizations turn data into doing. Splunk technology is designed to investigate, monitor, analyze and act on data at any scale. Splunk, as a leading SecOps solutions provider, leverages its platform to aggregate data from multiple Zero Trust Partners to create a comprehensive view of security events that can both more effectively detect a threat as well as prioritize it. Splunk invested in BigID to help fill this data visibility gap in their ecosystem.
Together, BigID + Splunk empower customers to streamline security operations by categorizing data vulnerabilities by threat level, augment their Zero Trust strategy by proactively detecting unauthorized data exposure, and accelerate incident response to mitigate business impact & disruption. BigID helps fill the security analytics gap by enriching and augmenting contextual data to more efficiently resolve security incidents.
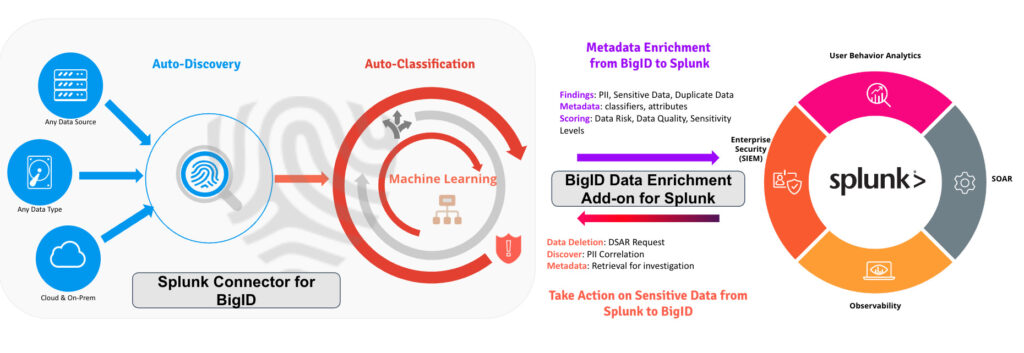
Discovering sensitive data in Splunk
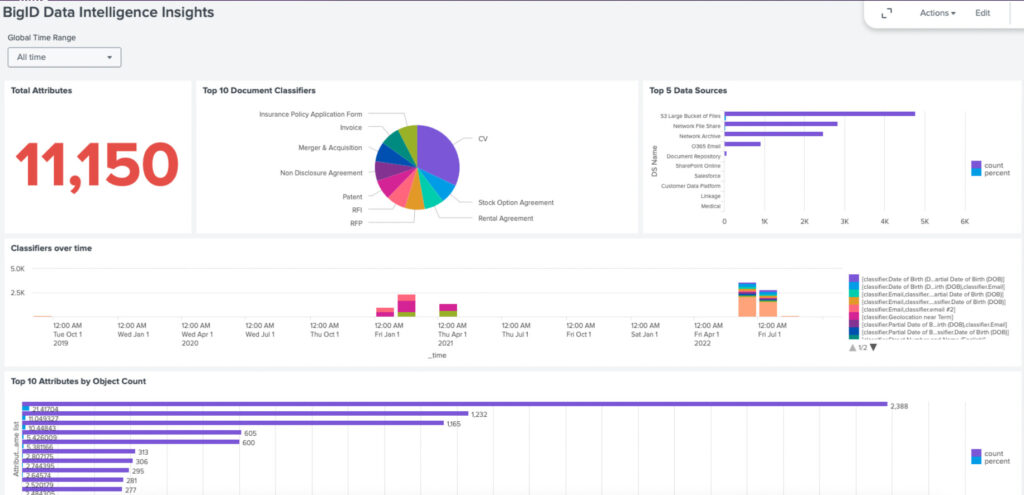
BigID’s initial integration allows for BigID & Splunk customers to scan their Splunk environment and aggregated reporting data for sensitive data discovery and DSAR support.
The Splunk Connector for BigID allows you to scan datasets in Splunk, finds personal and sensitive data in those datasets and automatically classifies the findings in a registry and catalog of metadata and tags.
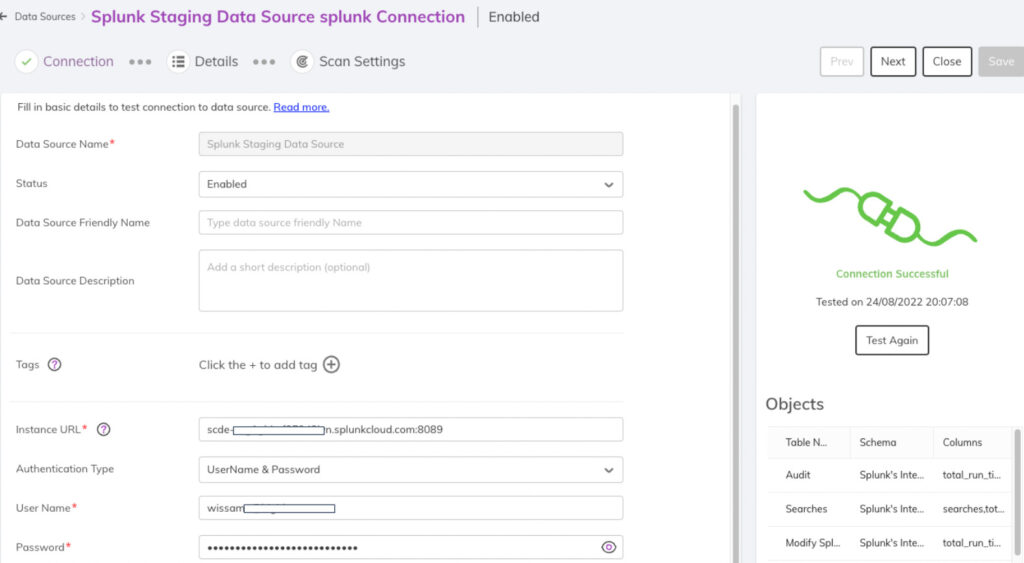
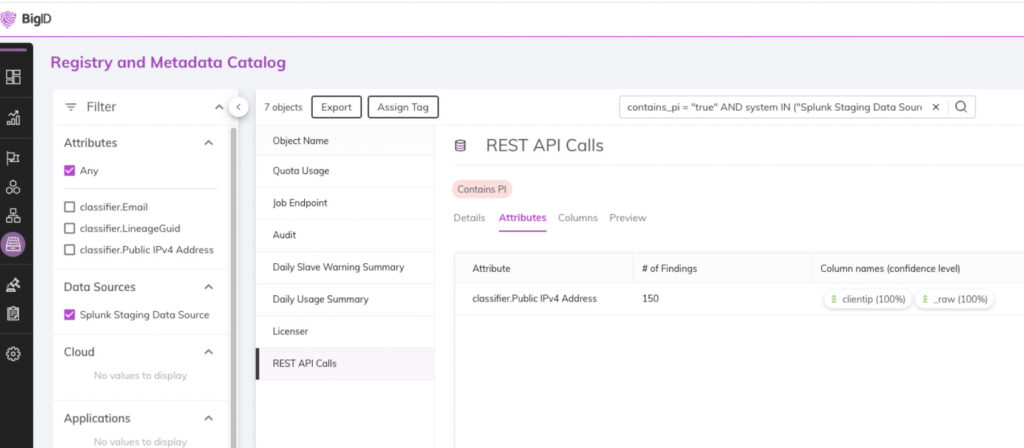
Ingesting data classification findings in Splunk
As an API-first platform, Splunk can ingest all the data classifications and tags for further analytics and enhancement of security detections.
Today, we are happy to announce the availability of the BigID Enrichment Add-on for Splunk. Using the add-on, all of BigID’s data classification objects are ingested into Splunk.
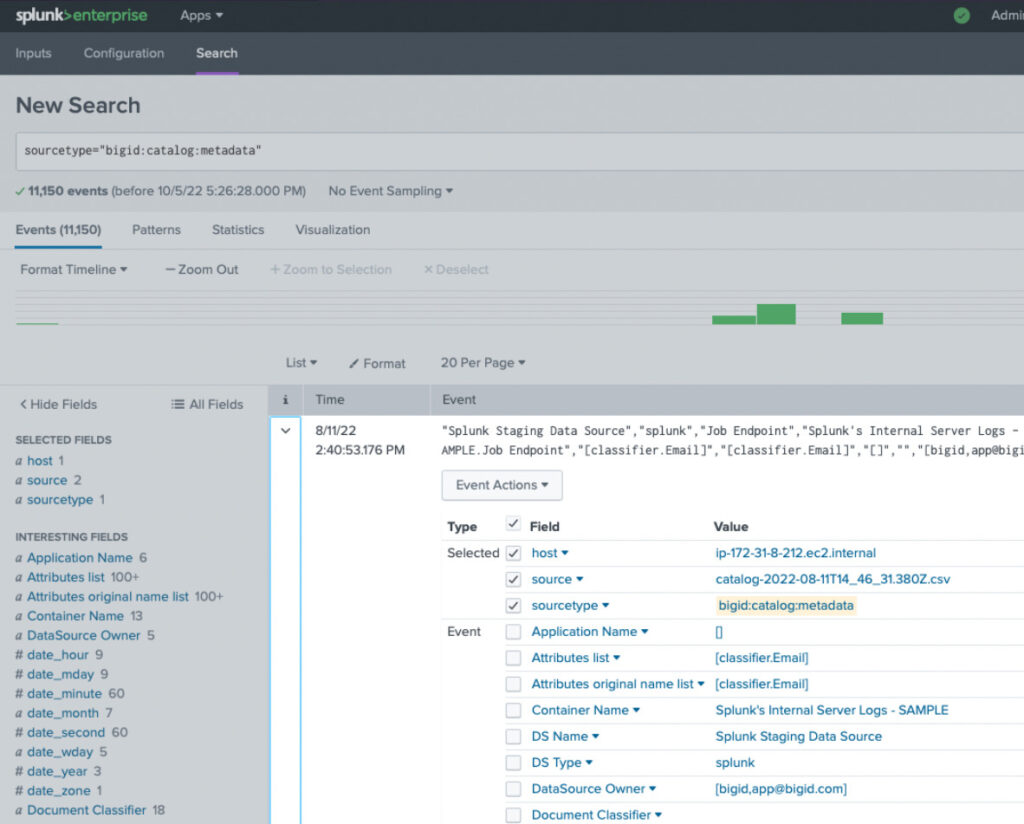
Enriching Splunk Enterprise Security for faster threat response
Using the data ingested by the BigID Add-on for Splunk, and having that mapped to the Splunk CIM Model, Splunk searches can be enriched with BigID’s classification metadata on sensitive assets.
Get started with BigID & Splunk today!
Now that we covered the essentials and benefits of BigID and Splunk together, let us go over the How-To for getting started today. With both BigID and Splunk being open platforms, we have built API-driven integration apps to exchange metadata and trigger actions on both sides.
To learn more about BigID and Splunk’s seamless integration—get a 1:1 demo today.

