
Protect Your Crown Jewel Data
Automatically find & protect critical, sensitive, regulated, dark, shadow, and business data.
Get data security that scales with you – and go beyond legacy solutions with BigID’s ML-driven data security solutions.
Reduce risk, protect your data, simplify incident response, and improve your security posture for all of your data, everywhere.
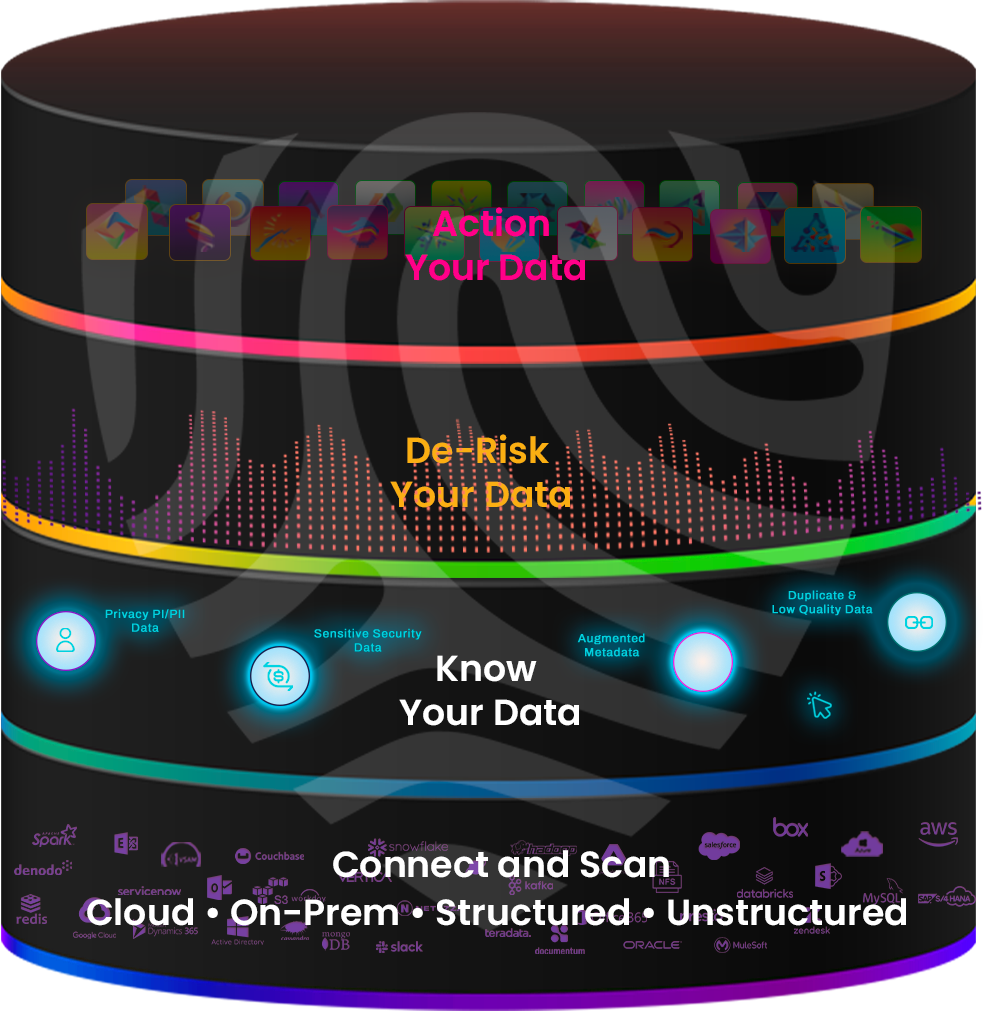
Find the data that matters most to you with customizable, ML-driven classification and automatically inventory your data by sensitivity, type, policy, context, and more.
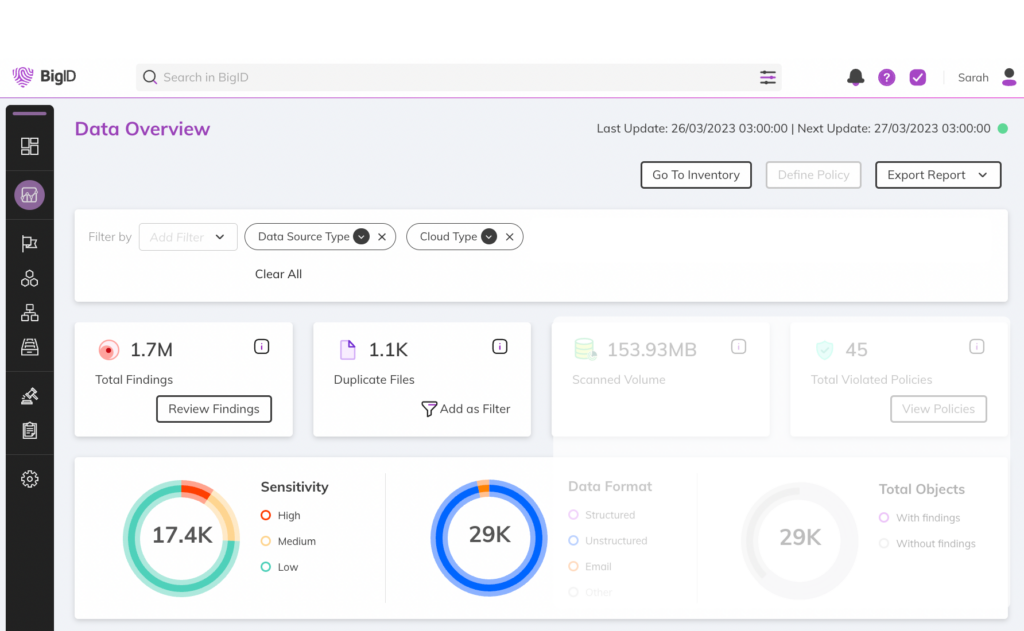
Identify vulnerabilities, remediate high risk, sensitive, and regulated data, reduce your attack surface, and track & manage your risk.

Automatically find & protect critical, sensitive, regulated, dark, shadow, and business data.

Accurately inventory all your data, everywhere – by sensitivity, type, policy, risk, and more.

Minimize your attack surface to reduce risk of data breaches & leaks – delete duplicate, redundant, and unnecessary data.

Proactively monitor and mitigate potential insider risk with risk investigation, data minimization, and remediation.

Simplify and automate data lifecycle management from collection to destruction.

Get to zero trust faster from the data up: reduce access to sensitive data based on activity and context

Reduce risk, improve security posture, and orchestrate controls: across cloud, data-centers, and hybrid environments.

Make DLP smarter and more accurate with ML classification and additional context for consistent enforcement.

Build your own apps, and easily operationalize and customize APIs and SDKs for Developers.
Uncover dark data, shadow data, and all data across the cloud and on-prem. Identify critical, high risk, and regulated data across your tech stack.
Automatically classify more types of data in more places: regular expression is just the start. Get native ML-insight with customizable NLP models that you can tune for even greater accuracy.
Manage data risk and security alerts by severity and type, investigate alerts, and delegate for remediation. Detect, manage, and protect critical data elements in your environment.
Manage remediation for high risk, sensitive, and regulated data. Take action with confidence with custom workflows, full audit trails, alerts, and notifications for data remediation.
Enforce policy at scale, label & tag data accurately. Seamlessly integrate with MIP and google labels to extend enforcement – and assign custom labels by sensitivity, residency, identity, and risk.
Define custom data retention policies, import existing policies, or activate over 190,000 OOB retention policies. Keep the data you need and delete the data you don’t with automated data retention.
Identify and manage over-privileged access and overexposed data, and enable zero trust. Lock down overexposed data and easily remediate access control risks and access rights violations, and reduce risks of insider threats, data leaks, and data breaches.
Manage, delegate, and execute data deletion. Easily and automatically delete data by user and system – and accelerate data minimization & data lifecycle management.
Get more from the tools you’ve got: easily integrate across your tech stack with native apps to enrich and extend your security posture.
Enrich your ecosystem by layering in advanced data risk insight and data sensitivity classification to make better decisions, faster.



























































Get a custom demo with our data experts in privacy, protection, and perspective – and see BigID in action.



















