What is a toxic data combination?
When multiple pieces of sensitive information converge within a particular area, it creates what is known as “toxic combinations” – unnecessarily elevating your data risk profile. For example, having credit card numbers, names, and addresses colocated together either in a table or within the same Google Doc servers is a very toxic combination. It’s a critical data security concern that demands your focused attention and prioritization.
It’s not uncommon for multiple types of sensitive data to be colocated within the same data source or data set. In fact, toxic combinations are becoming more and more prevalent, as seen in some of the largest breaches over the last few years.
What’s the big deal about Toxic Data Combinations?
Toxic combinations of sensitive data pose significant risks to organizations in three main ways:
Inadvertently Helping Insider Threats
Insider threat attacks have been steadily growing in the last few years. The problem worsens when sensitive data types combine, raising the risk for organizations and giving insiders easier access to valuable information. For example, when insiders can freely access one type of sensitive data like names, they could possibly have access to related information, such as Social Security Numbers or addresses, all in the same data source, set, or file. This unwittingly facilitates the intended lateral movement and breach strategies employed by internal adversaries, expediting their malicious actions, especially in the age of remote work.
Needlessly Expanding the Magnitude of a Breach
They can also exponentially elevate the exposure profile of data breaches. When highly sensitive data is colocated within the same data source, a breach involving such combined information can have far-reaching consequences. Not only does it provide cybercriminals with a more comprehensive view of an individual, but it also increases the potential damage that could arise from a single breach. The cumulative impact of such breaches can result in severe financial losses, legal repercussions, and regulatory fines, thereby inflicting substantial harm to the organization’s bottom line and overall operational stability.
Elevating Privacy Issues
The convergence of toxic combinations can culminate in confidentiality breaches, thereby jeopardizing the privacy of individuals and entities alike. When disparate fragments of personal information amalgamate, they give rise to sensitive data that has the potential to exponentially unveil personal details initially intended to be safeguarded. This erosion of privacy trust not only impacts clients, customers, and partners but also inflicts significant harm upon an organization’s reputation and credibility.
Automatically Find Toxic Combinations with BigID
BigID helps identify all of your toxic combinations with precision, remediate risk, and manage toxic combos. Here’s how we do it:
Know Your Data
In the age of hybrid and multi-cloud, a strong data security strategy requires complete data visibility, context, and control. BigID can find sensitive data, including toxic combinations of such, across any type of data – unstructured like files and PDFs, as well as structured data – across the cloud and on-prem. Go beyond basic and traditional pattern-matching measures and leverage advanced AI and ML to better, more accurately classify, and pinpoint toxic combinations of data. We have hundreds of OOB classifiers, as well as trainable classifiers, that can find sensitive information including various types of PI, PII, payment-related information, healthcare records, SSNs, and much more.
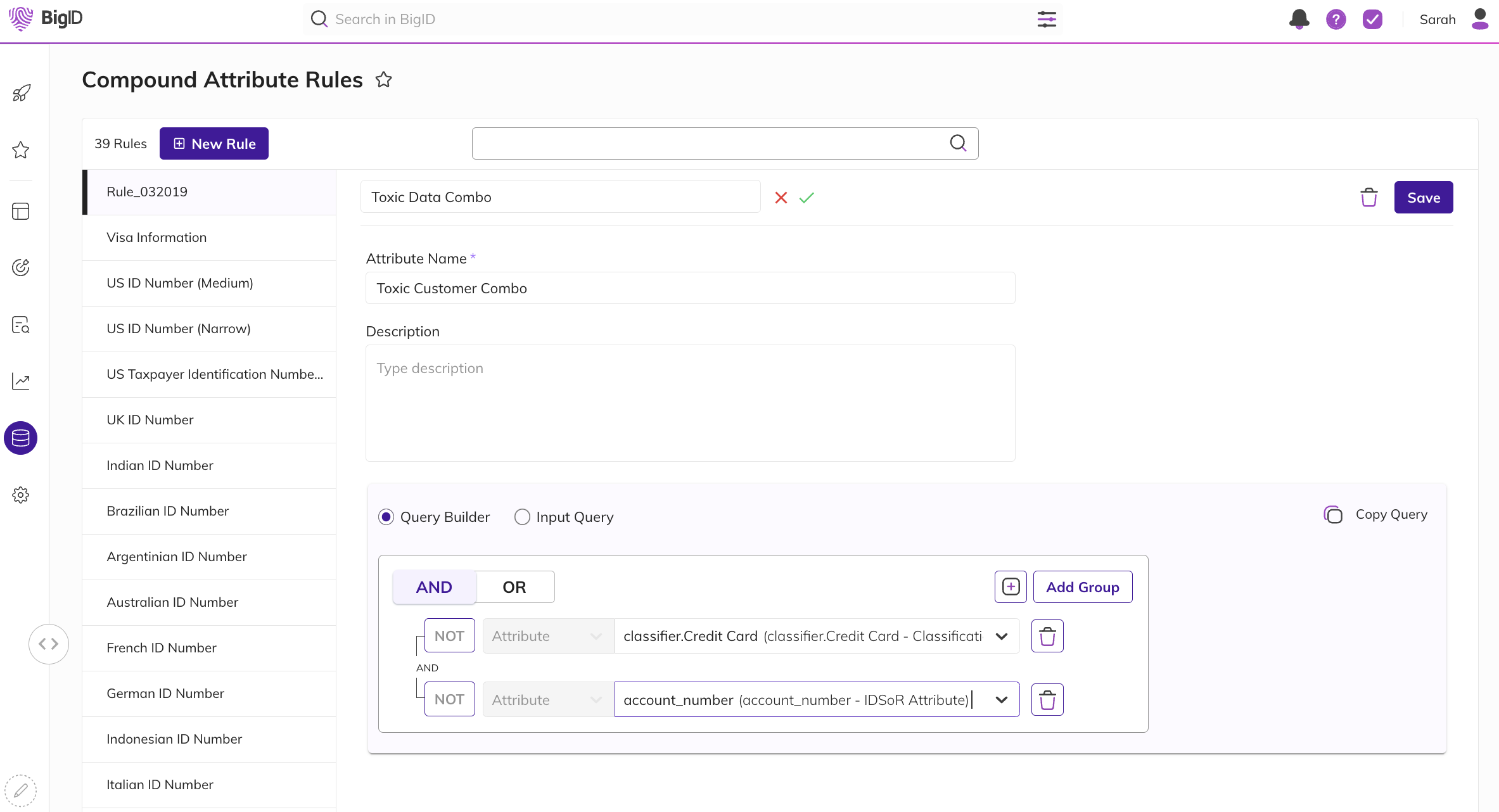
Find Toxic Combos
Build and configure unique, composite identifiers that represent toxic combinations you’d like to highlight and deem highly risky. For instance, you can set a composite identifier ruleset to detect when personal information like names, account numbers, or addresses come together. You may consider this combination a critical threat to exposure, access, and misuse – impacting both the security and privacy of that individual. Just as a skilled detective connects the dots to solve a complex case, BigID helps piece together sensitive data fragments to highlight critical data risks. This intricate understanding of data interdependencies allows organizations to proactively mitigate risks and enhance their data protection strategies.
Defuse the Toxicity
Understanding your toxic combinations is one thing – doing something about them is another. BigID’s DSPM workflows can help you streamline and accelerate the way you prioritize and remediate your most critical data risks, including toxic data combinations. Build out policies to detect specific toxic combinations and surface these as critical alerts within the Security Posture Management Console. Drill down and investigate; then automatically kick off remediation workflows and actions across the right people and tools – whether it be encryption, deletion, masking, and more. Continue to validate remediation actions and reduce risk with confidence.
BigID empowers you to proactively identify, analyze, and neutralize toxic combinations, ensuring the security and confidentiality of sensitive information. In an increasingly interconnected data landscape, this capability becomes an invaluable asset for organizations striving to maintain trust, compliance, and data integrity.
Want to learn more about defusing data toxicity? Schedule some time with one of our data security experts today.


