What Is Data Privacy?
Data privacy is a function within data management, focused on the collection, handling, storage, and protection of personal information. Essentially, data privacy is the balance between sharing data with third parties while remaining compliant with various privacy laws.
Why Is Data Privacy Important?
More than 70% of countries around the globe either currently have data privacy laws in place or are in the process of drafting new privacy legislation. The increase in regulations worldwide highlights that lawmakers understand the importance of data privacy. With new rules, comes new privacy rights requirements — and the pressing need for organizations to adapt to the constantly evolving privacy landscape.
Data privacy regulations worldwide aim to give individuals control over their data and hold organizations accountable to assure personal data is processed ethically and legally. However, as the data economy has evolved, businesses have found tremendous value in compiling, sharing, and using data. Brands such as Amazon, Google, and Facebook sit at the top of the data economy, with extensive business models focused primarily on using personal data.
But transparency in how businesses govern consent, follow privacy policy guidelines and manage the data that they’ve collected is essential to building trust and accountability with customers, employees, and partners.
According to Pew Research, 81% of Americans think the potential risk of data collection by companies about them outweighs the benefits. This highlights the disconnect between businesses and customers. Many organizations understand the risks of cyber-attacks and data breaches but still struggle to understand the importance of individual data rights as a civil liberty.
Data Privacy Risks & Challenges
Today, data is the focal point of most business decision-making, but businesses often make those key decisions based on data that isn’t visible or understood. Companies rely on data driven decision making to reach and engage their customers, but consumers have grown more concerned about their privacy. Companies must navigate challenges like protecting customer and employee data throughout its lifecycle, building consumer trust, and remaining compliant with changing regulations. Organizations that don’t comply with data privacy regulations and fail to protect personal, customer, and employee data are risking more than just financial penalties
Here are some examples of how data privacy can truly impact the business:
Regulatory Consequences
Data privacy and protection regulators may enforce mandatory audits, request access to documentation and proof, or even mandate that an organization stop processing personal data.
Reputational Damage
Non-compliance with the law could result in brand damage, loss of consumer trust, employee trust, customer attrition, and revenue reduction. In October 2016, Uber suffered a significant data breach but didn’t disclose the details. Instead of being transparent Uber paid hackers to delete the data and kept the incident quiet. The data breach was eventually disclosed in November 2017, this resulted in financial penalties and also had a negative impact on consumer trust.
Financial Fines
There are financial consequences, criminal fines, and prison sentences can be enforced based on the type of violation. It can also include loss of revenue, high litigation, and remediation costs. Recently Amazon was hit with the largest penalty to date of 746 million-euro ($888 million), as the EU privacy watchdog fined Amazon for violating the data protection policy.
Operational Debt
Most data privacy laws give people more rights over their data, such as the right to access, change or delete their data. However, this can be a significant operational burden if it isn’t implemented effectively, as organizations need to discover and classify data where any personal data exists
Loss of Consumer Confidence
Arguably the most valuable asset to any organization is consumer trust. Without it, businesses face an uphill battle to regain faith from their customers, much like the incident where a Capital One data breach exposed the records of nearly 106 million people.
Data Privacy vs. Data Security
Data privacy and data security are not interchangeable, even though some organizations may think otherwise. Some may think that keeping sensitive data secure is sufficient for compliance with data privacy regulations but that perspective may be a bit short sighted.
- Data privacy regulates how personal information (PI) and personally identifiable information (PII) should be properly collected, accessed, processed, stored, protected, and shared.
- Data security protects sensitive data from being compromised by data breaches, hackers, unauthorized access, and malicious attacks.
There are even scenarios where data security can exist without data privacy, but never the other way around. For example, an organization can have sophisticated technology and elaborate data security methods to protect personally identifiable information (PII). Still, if the data was captured without consent, that would be a violation of data privacy.
Governing Laws of Data Privacy
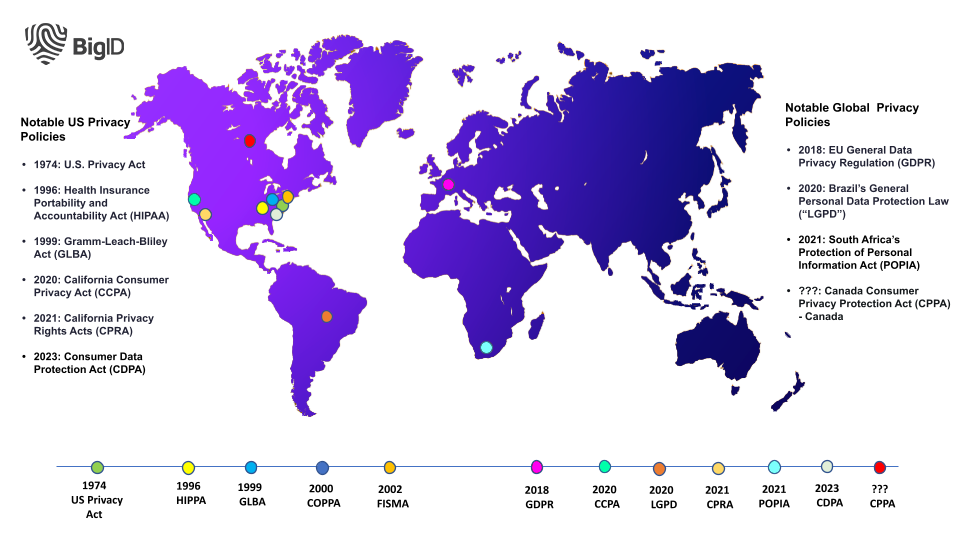
Regulations in the data privacy space are constantly evolving and expanding. It is up to companies to determine which privacy laws impact their specific regions and affect their users.
Here are four of the most impactful privacy laws to date:
GDPR: General Data Protection Regulation
In May 2018, the European Union’s General Data Protection Regulation (GDPR) became the first prominent data privacy and protection regulation to have a global impact.
GDPR forced businesses to rethink how they collect, manage, and govern access to personal data — and unlike previous generations of privacy laws, it includes a compelling incentive to comply, with penalties for violation as high as 4% of a company’s global revenue.
The GDPR gives consumers more rights over their data while also holding companies accountable for the necessary measures to protect data. However, the most challenging part of staying compliant with GDPR is responding to data subject access requests (DSARs) for most companies.
It’s not easy for organizations to find, supply, or delete an individual’s data upon request. As a result, many IT and data privacy teams need data rights automation applications to automatically discover and classify personal data for protection and accelerate DSAR requests.
CCPA: California Data Privacy Act
Similar to GDPR, the California Consumer Privacy Act (CCPA) extends data privacy protections on the personal data of California residents. The CCPA — which requires businesses operating in California to identify and discover personal data, fulfill data subject access requests, and protect personal data — went into effect on January 1, 2020.
California residents can ask organizations what personal data they have stored on them, ask them to delete it and find out what information was given to third parties. These measures apply to data gathered within the state. That means companies need to quickly and accurately find and classify sensitive data that falls under the CCPA — and should have process in place to fulfill DSARs.
HIPAA: Health Insurance Portability and Accountability Act
One of the most established US data privacy laws at the federal level is the Health Insurance Portability and Accountability Act (HIPAA) — a regulation designed to protect patients’ health and medical-related data.
Congress passed HIPAA in 1996, but with the healthcare industry being a primary target for data breaches, demands for greater data privacy protections increased after its enactment. As a result, the U.S. Department of Health and Human Services (HHS) issued the Privacy Rule in 2000 to carry out HIPAA’s mandate to safeguard health information. Regardless, healthcare continued to incur the highest average breach cost at $7.13 million, according to IBM.
GLBA: Gramm-Leach Billey Act
Another significant privacy law is the Gramm-Leach-Bliley Act (GLBA), a U.S federal law that controls how financial institutions manage people’s sensitive information.
There are three areas of this law: The Financial Privacy Rule regulates how personal financial data is disclosed and collected; the Safeguards Rule requires financial institutions to protect data by implementing a security program; the Pretexting provisions forbid using false pretenses to access private data. Under this act, financial institutions are also responsible for giving customers written notice explaining their data-sharing process and practice.
How BigID Helps Organizations Automate Data Privacy
Data privacy is a staple of any organization—necessary but often a painful and time consuming challenge. Organizations need a solution that best fits their needs. BigID offers tailored solutions that help businesses:
Protect Your Enterprise Data
The first step in data privacy alignment is to inventory all personal data across the entire IT infrastructure. BigID supports all discovery methods— from discovery of data assets to discovery of PI and PII through full scans. BigID’s data discovery foundation allows organizations to inventory, map, classify, and align data to regulatory policies. BigID can discover structured, unstructured, and semi-structured data sources and business applications, whether deployed on-premise or in the cloud, with hundreds of connectors.
Prevent Data Breaches
BigID enables organizations to generate documentation and reporting of data processing activities. This way, organizations can maintain an accurate set of data processing flows, with the ability to show how data is processed and shared across the enterprise and third parties.
Reduce Risk
Managing access to data is one of the easiest ways to reduce risk, as it lessens a company’s exposure to data breaches, theft, or misuse. The BigID Access Intelligence App can flag and investigate high-risk users, groups, and data across the organization. This allows companies to review file clusters and categories containing sensitive data with open access and produce an audit report of high-risk targets for permissions review and risk reduction.
Help Achieve Compliance
Specific privacy laws GDPR, CCPA, and GLBA, help consumers exercise their data rights by obtaining opt-in consent before an organization can process their personal and sensitive data. BigID’s consent capabilities extend to multi-channel consent: including minor, employee, and regulatory consent, across an organization’s data stores, ensuring compliance for your organization.
Get a 1:1 demo to see how BigID enables companies to automate and operationalize their privacy programs.

