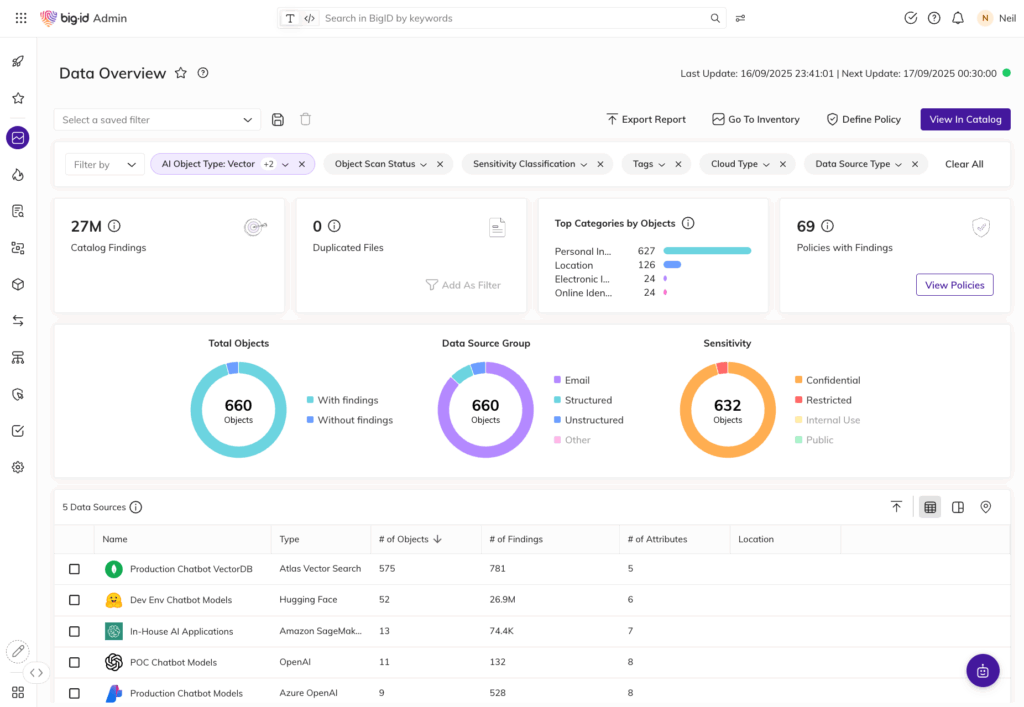
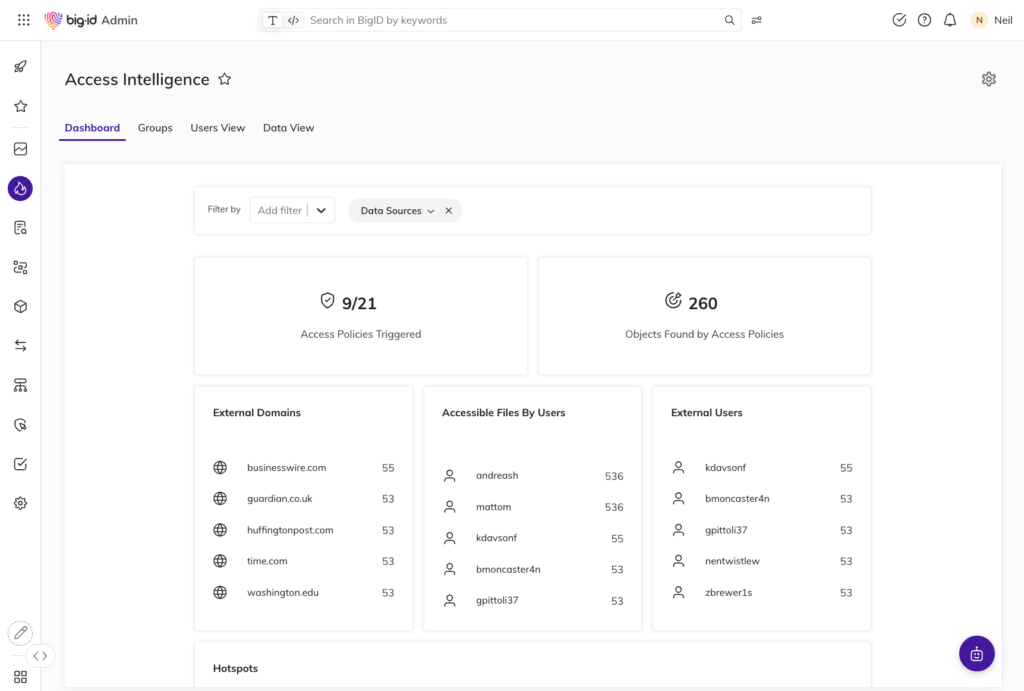
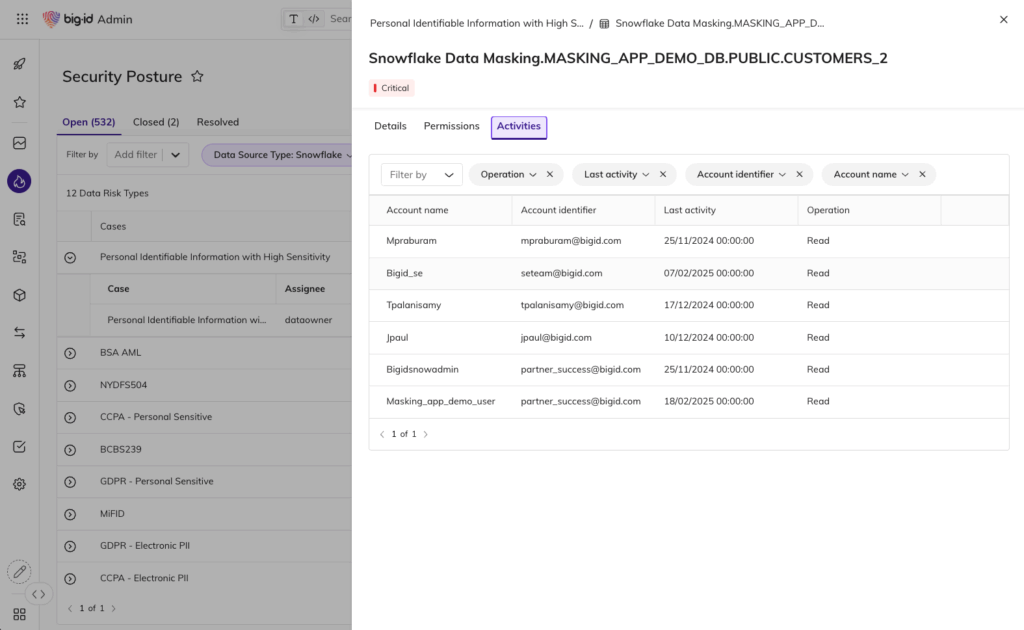
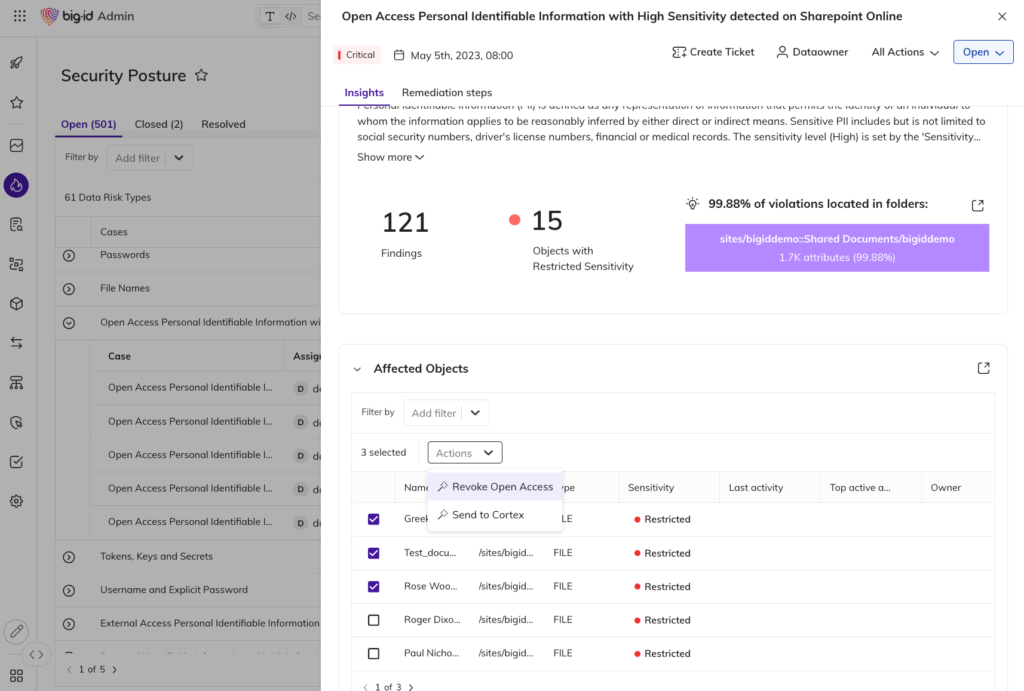
Unified Access Visibility Across All Data
- See who — and what (AI models, NHIs, service accounts) — has access to sensitive data
- Eliminate blind spots across hybrid, multi-cloud, SaaS, and unstructured environments
- Build a single, risk-aware view of entitlements, ownership, and usage