Identify All Your Sensitive Data
See a clear, complete view of all your sensitive data across the enterprise — not just the data you know about — to protect it.
Regulations established by NYDFS Cybersecurity Requirements (NYCRR 500) mandate that financial services protect their customer data and manage cyber risk.
NSDFS encourages a risk-based approach to protecting customer information from being revealed or stolen for illicit purposes.

The NYDFS Cybersecurity Regulation (NYCRR 500) requires that covered institutions — organizations in financial services — implement phased cybersecurity policies that involve:

Financial services firms must understand where their customers’ personal data resides, who it belongs to, how long they need to retain it, and who has access to it.
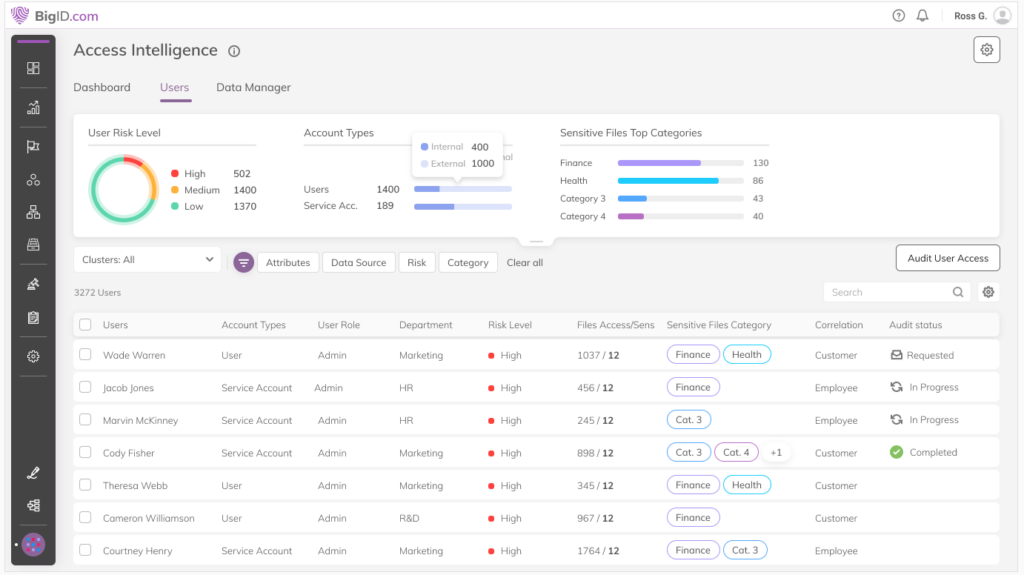
With the expansive definition of nonpublic personal information (NPI), the NYDFS extends scope to data that might cause material harm if exposed.
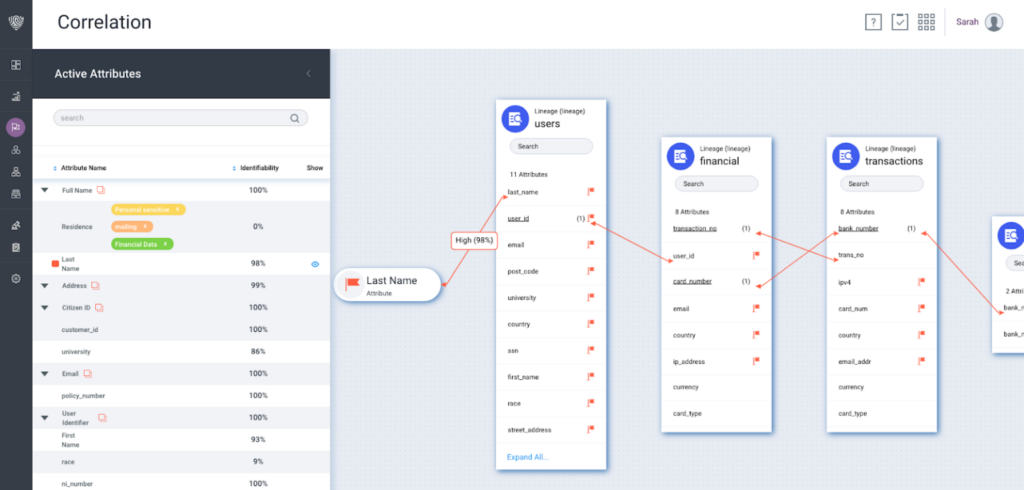
Companies must maintain a comprehensive map of all sensitive data — on-prem and in the cloud — identify high-risk data, alert on violation risks, and manage retention timelines.
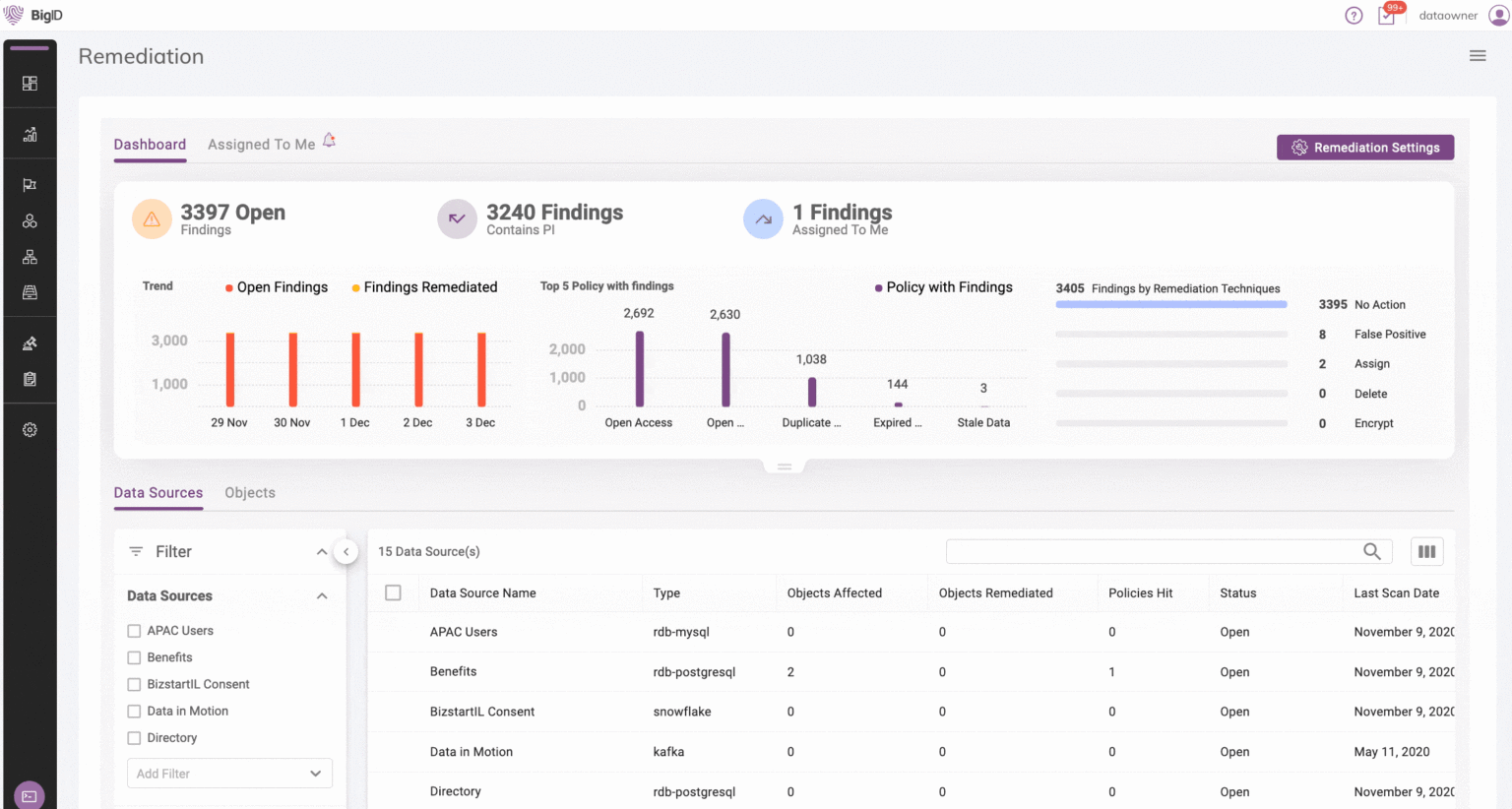
See a clear, complete view of all your sensitive data across the enterprise — not just the data you know about — to protect it.
Discover and inventory personal, sensitive, and critical data — and then associate it with specific users.
Minimize duplicate and redundant data, fix data quality issues, and automate workflows based on retention timelines.
Identify high-risk data and where it resides, flag vulnerable data flows and access patterns, and continuously monitor access activity.
Discover all sensitive and regulated data that falls under NYDFS, wherever it’s stored across the enterprise.
Take an ML-based approach to automatically classify and tag NPI and high-risk data that is regulated by NYDFS.
Leverage data retention policies and business rules, define custom policies, and apply them consistently across all data types and all data sources
Remediate sensitive and regulated NYDFS data and manage high-risk-data with remediation workflows and audit trails.




























































Get a custom demo with our data experts in privacy, protection, and perspective – and see BigID in action.



















