Secure, Limited, Revocable: Azure SAS Tokens Explained
In today’s cloud-centric landscape, where data security is paramount, organizations grapple with the challenge of granting controlled access to their resources without compromising sensitive credentials. Shared Access Signature (SAS) tokens emerge as a cornerstone solution within the Azure ecosystem, offering a robust mechanism for securely delegating access to specific assets.
As businesses increasingly leverage the power of Azure services for their operations, understanding the fundamentals of SAS tokens becomes essential for safeguarding data integrity and mitigating security risks. Let’s delve into the world of SAS tokens, exploring their significance, implementation, and best practices in this ever-evolving digital era.
What is a SAS Token?
SAS tokens, or Shared Access Signature tokens, are a type of security token used in Azure cloud services, particularly Azure Storage, Azure Service Bus, and Azure Cosmos DB. SAS tokens provide a way to grant limited access to resources in these services without sharing the account access keys directly. They are commonly used for granting temporary access to specific resources or operations.
There are two main types of SAS tokens:
Service SAS (Shared Access Signature)
Service SAS tokens are used to grant access to specific resources within a service, such as blobs, queues, tables, or files within Azure Storage. They are typically created with specific permissions (read, write, delete, etc.) and an expiration time. Service SAS tokens are usually associated with a particular resource URI.
Account SAS (Shared Access Signature)
Account SAS tokens provide broader access to resources within an entire storage account or other Azure services. They can be used to perform operations across multiple resources within the account, such as listing containers or queues, and are commonly used for administrative tasks. Account SAS tokens also have specific permissions and an expiration time.
Both types of SAS tokens are created based on a set of parameters that define the permissions, expiry time, and other constraints. Once generated, SAS tokens can be appended to URLs as query parameters or included in HTTP headers to authenticate and authorize access to the specified resources. They provide a secure way to delegate access to resources in Azure services without exposing sensitive credentials.

How Do SAS Tokens Work?
Imagine SAS (Shared Access Signature) tokens as special keys that allow different people or systems to access specific rooms in a building (like Azure services) without giving them the master key (account keys).
Here’s how organizations can use SAS tokens:
Delegate Access, Reduce Risk
Suppose you have a team working on a project, and they need to access certain files stored in Azure storage. Instead of giving everyone the master key to the storage (which would be risky), you can create SAS tokens for each team member. These tokens allow them to access only the files they need for their work, like giving them a key that opens just one room in the building.
Grant Flexible Temporary Access
Sometimes, you might need to share access for a limited time. For example, if you’re collaborating with a partner company for a short-term project, you can create SAS tokens that expire when the project is finished. This ensures that access is only granted for the duration needed, reducing the risk of unauthorized access after the project ends.
Enable Controlled Permissions
SAS tokens allow you to specify what actions someone can perform, such as read-only access or read-write access. This way, you have fine-grained control over who can do what with your resources. For instance, you might allow a contractor to upload files but not delete them.
Common Azure SAS Token Management Challenges
To overcome the challenges associated with managing SAS tokens, addressing security risks, and simplifying integration complexity, organizations can implement the following strategies:
Management Overhead
- Challenge: If you have many users or services that need access to different resources, managing all the SAS tokens can become complex. Keeping track of who has access to what and ensuring tokens are regularly rotated and revoked can be challenging.
- Solution: Establish a centralized system or tool for managing SAS tokens across the organization. This system should allow administrators to create, monitor, and revoke SAS tokens centrally. It can include features such as role-based access control (RBAC) to delegate token management responsibilities to specific teams or individuals.
Security Risks
- Challenge: While SAS tokens are a secure way to grant access, mishandling them can still pose risks. For example, if a token is accidentally shared or leaked, it could grant unauthorized access to your resources.
- Solution: Implement encryption mechanisms to protect SAS tokens both in transit and at rest. Utilize encryption protocols such as HTTPS for secure communication and encryption at rest for stored tokens. Implement access controls to restrict access to token management systems and enforce authentication and authorization mechanisms to prevent unauthorized access.
Integration Complexity
- Challenge: Integrating SAS token generation and management into your applications or workflows can require some effort, especially if you’re dealing with a diverse set of services and access scenarios. Ensuring consistent and secure token generation across your organization may require careful planning and implementation.
- Solution: Establish standardized processes and guidelines for token generation and integration across different applications and services. Define clear naming conventions, parameter configurations, and access policies to ensure consistency and security across the organization. Provide developers with tools, libraries, or SDKs to simplify token integration and enforce security best practices.
Despite these challenges, SAS tokens are a valuable tool for securely delegating access to Azure resources within organizations, providing a balance between security and convenience. With proper planning and implementation, organizations can effectively leverage SAS tokens to manage access to their cloud resources.

Example of Azure SAS Keys
Let’s say you have a storage account named “examplestorage” with a container named “examplecontainer” and you want to generate a SAS key to allow read access to blobs within that container for a limited time.
Here’s how a SAS key might look like:
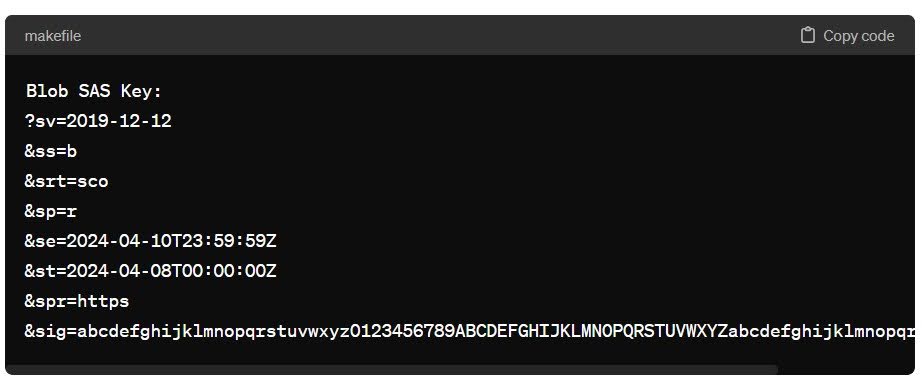
Explanation of parameters:
sv: The storage service version.
ss: The signed services, in this case, blobs.
srt: The signed resource types, in this case, service (s), container (c), and object (o).
sp: The signed permissions, in this case, read (r).
se: The expiry time for the SAS token (2024-04-10T23:59:59Z).
st: The start time for the SAS token (2024-04-08T00:00:00Z).
spr: The signed protocol, in this case, HTTPS.
sig: The signature, which is a hashed value generated using your account key and the specified parameters.
This SAS key allows read access (sp=r) to blobs within the container example container from April 8, 2024, to April 10, 2024, using HTTPS protocol.
Please note that the actual SAS key would have a longer signature (the sig parameter) generated using your account key and other parameters. Additionally, you may include other parameters depending on your specific requirements, such as IP restrictions or stored access policies.
This SAS key allows read access (sp=r) to blobs within the container example container from April 8, 2024, to April 10, 2024, using HTTPS protocol.
Please note that the actual SAS key would have a longer signature (the sig parameter) generated using your account key and other parameters. Additionally, you may include other parameters depending on your specific requirements, such as IP restrictions or stored access policies.
Best Practices for Securing Azure SAS Tokens
To keep SAS tokens secure, you should follow some best practices:
- Limit Access: Only grant permissions that are necessary for the task. For example, if someone only needs to read files, don’t give them permissions to delete or modify them.
- Set Expiry: SAS tokens have an expiration time. Set it to be as short as possible while still allowing enough time for the task to be completed. This helps minimize the risk if the token is somehow leaked.
- Use HTTPS: Always use HTTPS when transmitting SAS tokens. This encrypts the communication between your client and the Azure service, making it much harder for anyone to intercept or tamper with the token.
- Protect Secrets: Treat SAS tokens like passwords. Don’t hardcode them in your application code or share them openly. Store them securely, such as in a secure vault or as environment variables.
- Rotate Tokens: Regularly rotate (change) SAS tokens, especially if you suspect they might have been compromised. This ensures that even if a token is leaked, it won’t be valid for long.
- Monitor and Audit: Keep track of who is using the SAS tokens and what they’re doing with them. Monitor for any unusual activity, and regularly review access logs and permissions to ensure they’re still appropriate.
How BigID Helps Reduce and Mitigate Risk with SAS Tokens
Risk is an unavoidable factor in every modern business, but what often defines a successful one is how they choose to mitigate that risk. BigID is the industry leading platform for data privacy security, compliance, and AI data management leveraging advanced AI and machine learning to give organizations more intuitive insight into all their enterprise data— wherever it resides.
With BigID you can:
- Know Your Data: Automatically classify, categorize, tag, and label sensitive data with unmatched accuracy, granularity, and scale.
- Reduce Your Attack Surface: Shrink the attack surface by proactively eliminating unnecessary, non-business critical sensitive data
- Improve Data Security Posture: Proactively prioritize and target data risks, expedite SecOps, and automate DSPM.
- Remediate Data Your Way: Centrally manage data remediation – delegate to stakeholders, open tickets, or make API calls across your stack.
- Enable Zero Trust: Reduce overprivileged access & overexposed data, and streamline access rights management to enable zero trust.
To start proactively protecting your enterprise data and mitigating risk— get a 1:1 demo with our security experts today.


