Insider threats have become one of the most pressing issues when addressing security strategy and risk across all industries over the past couple of years. At its core, an insider threat is a human-centric risk that can cause reputational or financial damage that negatively affects the organization.
Addressing insider threats has been a challenge for a majority of organizations due to the complexity of security tooling, eliminating human risk factors, procedural gaps, and understanding how to mature such a program. Some of the most important gaps when it comes to initially starting an insider threat program is the context of existing data and understanding the exposure of that data.
There are a multitude of security tools that have features that can fulfill subsections of an insider threat program, but there’s a consistent gap that security teams always find—context.
Contextualize Data
BigID’s data discovery and classification capabilities allow organizations to immediately start providing some context to their data. As there are points during an insider threat investigation when analysts don’t have an understanding of what data was shared. BigID can alleviate this burden and rapidly enrich their investigation to see if emails, social security numbers, medical data, or even passwords were shared outside of the organization. This removes the ambiguity of what data was passed to an unauthorized party which may do future damage to the organization.
Even with data discovery and classification capabilities, we are able to do more by auto-labeling the sensitive data discovered. This helps differentiate what data is or is not considered your “crown jewels”. By auto-labeling, this enriches additional security tooling already in place, such as Sharepoint or Google Workspace security features, to alert more accurately. As a result, it can mitigate some of the human risks associated with insider threat techniques. Let’s take a look at how this can be achieved.
Labeling with BigID
In the BigID platform, there are some initial steps to take in order to successfully auto-label your sensitive information. Under Data Management > Sensitivity Classification this is where you can align internal data classification standards to reflect not only within the BigID platform, but also Sharepoint and Google Workspace. Every organization has unique definitions on how they want to classify their sensitive data.
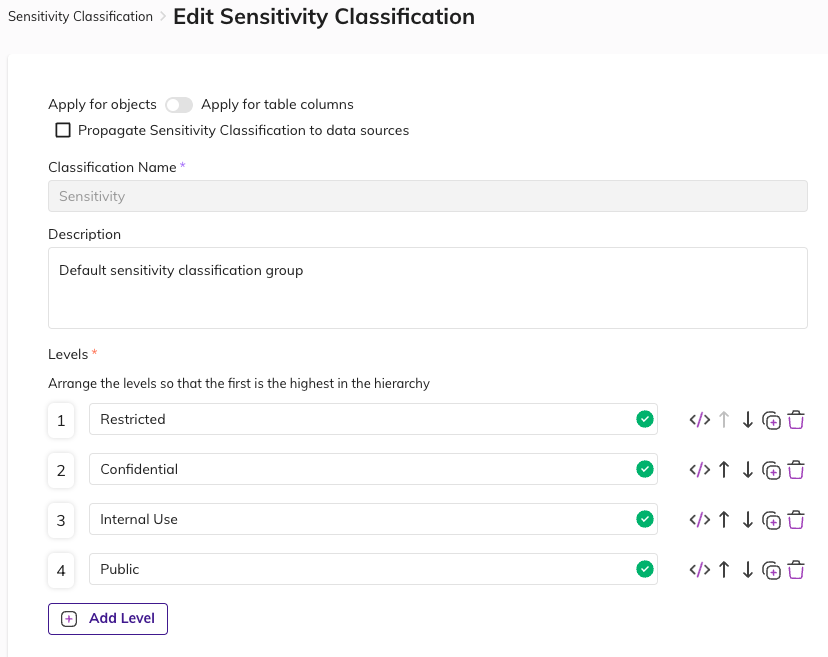
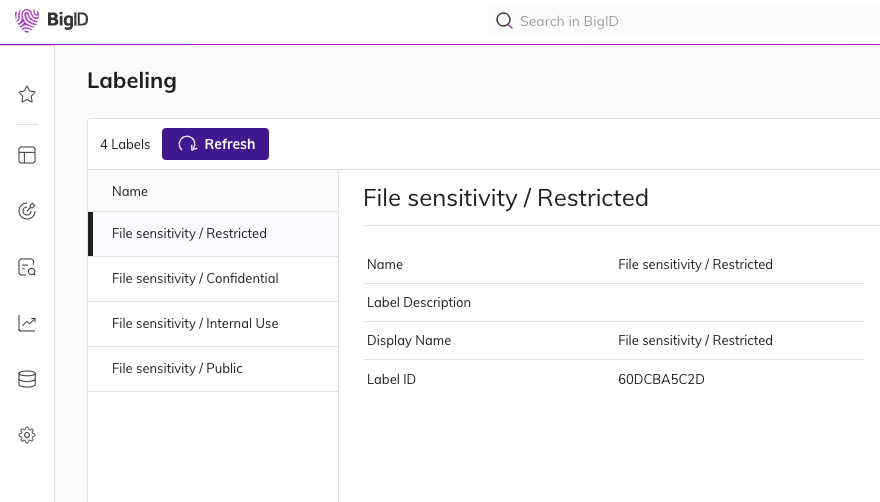
In order to promote more accurate findings during an insider threat investigation, tagging this information beforehand is a necessity. After aligning the sensitivity classifications, leveraging the File Labeling application is the next step. In the File Labeling application, users can configure the application with GDrive or MIP labeling capabilities.
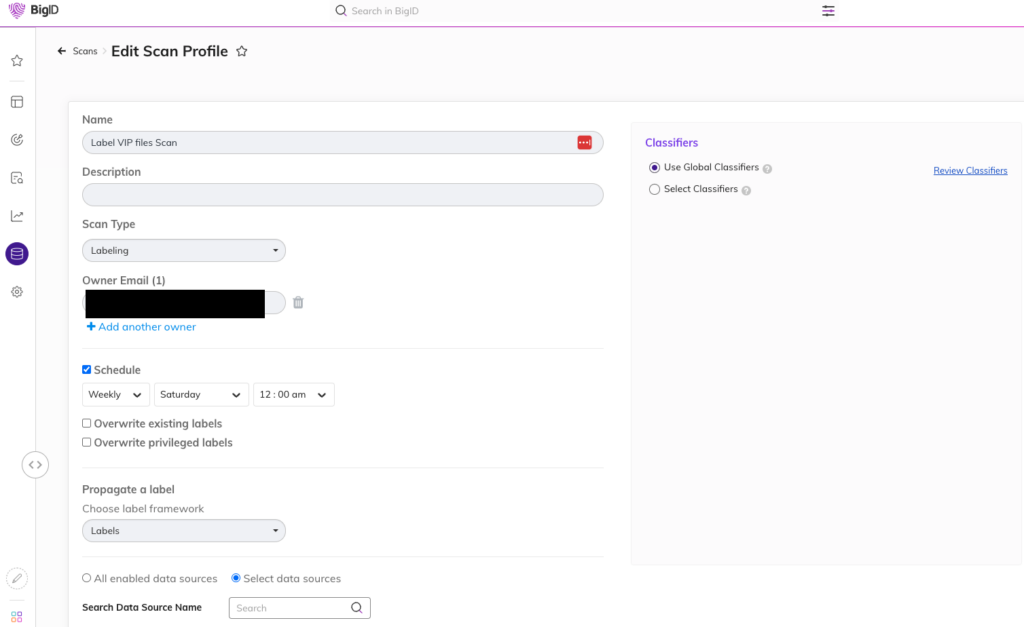
The scan profile is what is needed to be configured in order for the Labeling application to apply the classification labels to the object. As BigID performs scans on the data sources, it will assign the defined sensitivity label based on the query you would like to assign those labels.
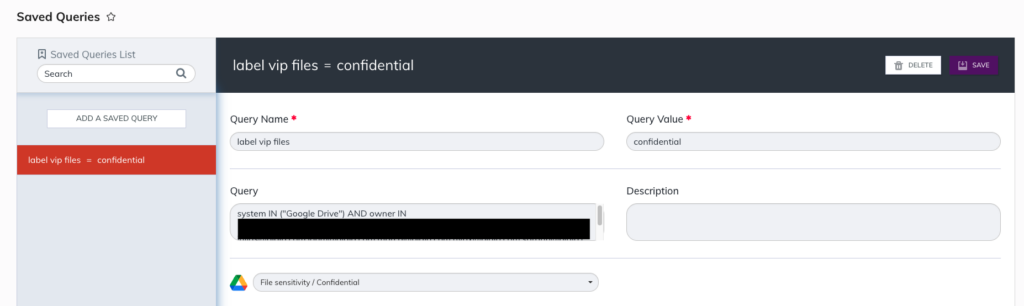
For example, you want to ensure that every file E-Staff has created is applied with a label of Confidential. Within Saved Queries, the user will explicitly call out each member of E-Staff and execute the scan and labeling action. At this point, all your sensitive data will be tagged with the sensitivity classification you have defined that will reflect in both the BigID catalog and the native collaboration tool in place.
Auto-labeling based on the classification of the data is where DLP could never evolve to. As DLP solutions trigger events based on policy violations, majority of the time the data still needs to be confirmed if it’s really PII, PHI, PCI, or etc meaning more wasted time than needed.
Additionally DLP really only operates on the endpoint which is already too late, or integrated with a CASB solution where the classifications are nowhere as robust as BigID’s. Being able to integrate BigID into an insider threat program is only a benefit to help streamline the technical capabilities needed for a successful insider threat program.
Understanding Access
Majority of organizations today really do not have a clear way of representing who has access to certain files or cloud storage solutions. This is paramount to understand what risks are already active in their environments today in order to effectively mitigate unwanted exposure. Luckily, BigID has this ability through our Access Intelligence App.
Essentially what makes this app so critical to an insider threat program, is that you can see who else has access to your information outside of your domain.
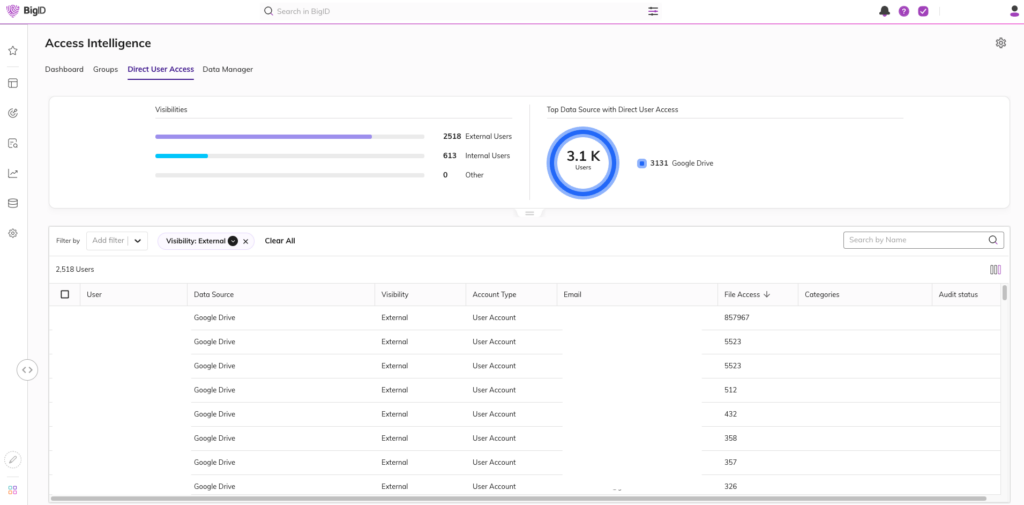
As organizations build out their insider threat program there is a period of backtracking audit logs through collaboration platform logs to see who shared documents outside of their organization. Unfortunately, that is a very point in time method and runs the risk of missing those logs pending on your log retention periods or let alone log volume.
With the Access Intelligence application, analysts will have another data point to refer to in regards to who is sharing sensitive information outside their organization that could make them a potential insider threat.
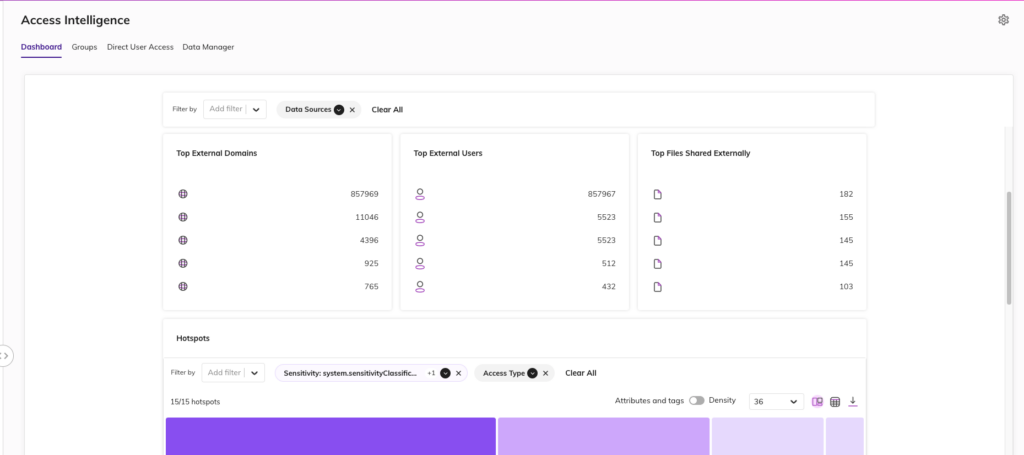
Having this information readily available is extremely powerful for a security team. This alongside the context of the data in question streamlines the investigation process to have a better understanding if someone is indeed an insider threat. This enables the security team to have the ability to move forward and revoke access, provide training to employees, and reduce your overall data risk.
Combined with DSPM
These two key features alongside our flagship DSPM product are a must for any organization looking to elevate their insider threat program. There is no magic tool or solution that is going to cover all insider threat risks. Insider threats are a human-centric risk and multiple variables play a part in that. Though BigID can help close those gaps in new or existing insider threat programs. BigID’s DSPM platform is here to fill in those gaps to provide more context in investigations, understand your existing exposure, and harmonize with existing tooling.
To learn more about how BigID can help your organization minimize insider threats— get a 1:1 demo with our experts today.


