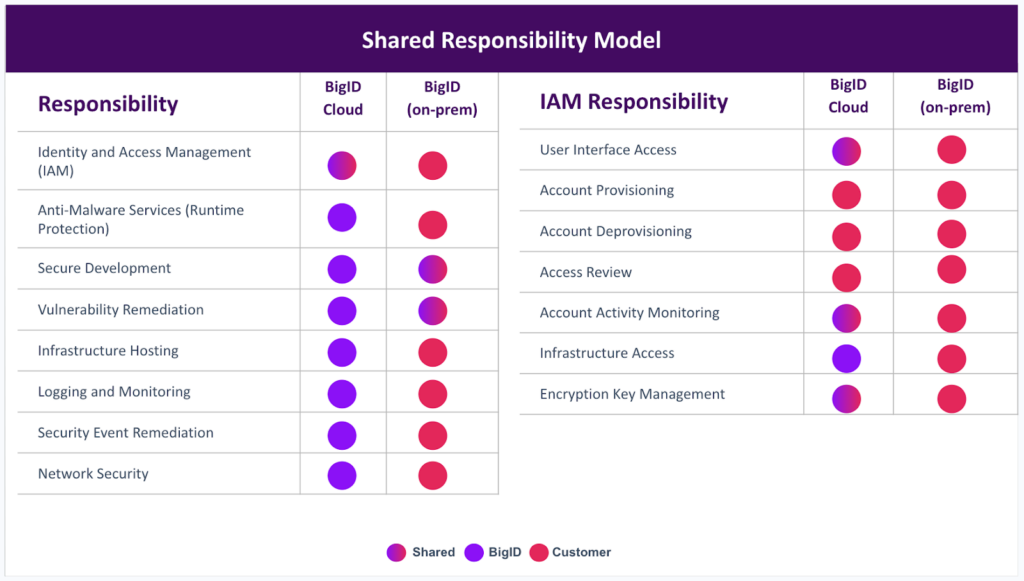
Customer Controls
Our customers have full control of the systems they connect to BigID including setup and configuration. BigID offers training, professional services support, detailed documentation, and customer support to help them get there securely.