Companies deal with a great variety of secrets, such as API Keys and other types of credentials, used for accessing the most diverse types of platforms and services integrations. For that, developers need to handle these secrets constantly in their products. This often leads to developers being unsafe and practical, ending up uploading that information to a code repository, making it accessible to unauthorized users.
The Dangers of Hard-Coded Secrets
Depending on the characteristics of the exposed secret, a leaked secret can result in nefarious security consequences. A great example is a credential that gives access to a whole Cloud environment. If it becomes stored in a code repository— in a manner that anyone ends up with access to that repository— it can use the secret to execute a variety of unexpected actions. Or even worse, secrets that are hard-coded in code that is served to the client, such as mobile apps, which would allow basically any user to access that credential. That’s a great amount of power in hands, which can lead to exposure of sensitive data, service interruption and very likely financial losses.
The Solution Architecture
The BigID Application Security team is taking advantage of these features to handle all detections programmatically, with automations that will run on a regular basis to check for new secrets found in our code bases. Any detection will generate a notification that will be sent for human analysis, who will assert if the risk is real or not. In case it is, the necessary security measures can be taken to eradicate this risk and enforce the protections so that it won’t happen again.
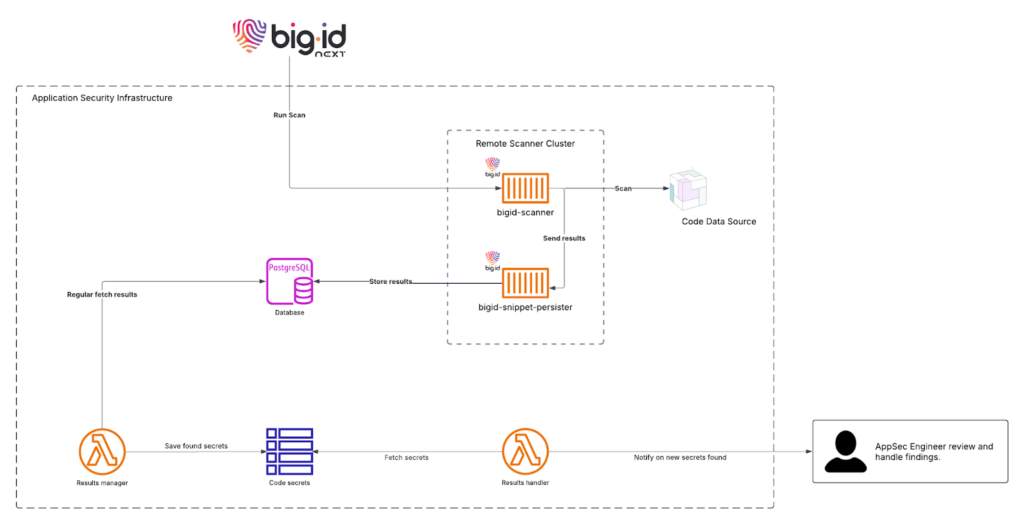
To assist in the automated detection, a complementary and easy to deploy serverless architecture is responsible for handling, checking and filtering for new results in the complete results set. That being done, each new valid detection can be stored separately in another secure database that allows internal management, granting the expected emphasis to every issue, which will then become the previously mentioned notification. Lastly, as part of the process, an Application Security Engineer will be able to individually validate the findings and go with the right security response according to the context of the issue, ensuring that every risk is cared for and treated.
Advantages Behind the Snippet-Persister’s “Bringing Your Own Database”
This means the customer will be able to provide and manage their own database instance, and instead of storing data in BigID managed warehouses, the Snippet Persister will be plugged to the Scanner and store the resulting snippets from scanning and detecting the data according to the classifiers set – in this case the classifiers detecting secrets. With this, a few security advantages take place, avoiding that the affected data spreads further more to undesired places. This will facilitate increased control over it even in terms of jurisdiction or desired specific security controls, such as encryption type. The “Bring your own database” model allows the customer to continue managing their data smoothly and with security.
Fine Tuning Your Search with Classifier Management
There may be cases where an application handles secrets that have uncommon formats that are not covered by the BigID’s native classifiers. For these cases, BigID provides a Classifier Management capability that enables viewing and managing settings for out-of-the-box classifiers as well as creating and configuring your own custom classifiers (using, for example, Regular Expressions). This feature provides the assurance that scans can cover every case needed.
BigID’s Approach to Hardcoded Secret Detection
Among other useful resources, BigID offers the possibility of creating scans exclusively focused on secret identification among data, using classifiers with dedicated Regex rules, such as the “Username and Explicit Password” classifier, containing rules definitions that aim to detect hard-coded passwords and usernames.
BigID has more than 70 native classifiers that are related to detection of different types of secrets and tokens, including specific cloud-native tokens, which allows a very broad detection. In case the needed pattern is not found as a classifier at first, it is always possible to create custom ones to attend to different kinds of data you’re aiming to locate.
For further programmatic access and flexibility while handling the results of the scan, BigID offers the Snippet Persister service, which will store these results along with the enclosing data around the detected secret, providing also more insights for a final analysis, since most times a single random string is not enough for a realistic assessment. This storage happens separately in a “bring your own” database that will allow safe storage and access of results. BigID’s very own Application Security team is implementing this solution today.
Take a test drive today to see BigID in action or book a 1:1 demo with our experts.


