As organizations scale their cloud, SaaS, and on-prem environments, data activity has exploded. Files are uploaded, synced, accessed, shared, copied, downloaded, and deleted across dozens of systems — often by a growing mix of identities that now include not only human users but service accounts, automated workflows, and emerging AI agents.
Yet despite all this movement, most security teams still struggle to answer the foundational question behind every investigation:
Who did what, when, and to which data?
The answer is rarely simple. It’s often buried across siloed logs, inconsistent audit trails, and tools that weren’t designed for modern data ecosystems. With Activity Explorer, BigID is closing that gap — giving teams a unified, contextual, and fully searchable view of all data activity across their hybrid environment.
The Visibility Gap: Scattered Logs, Slow Investigations, Missed Signals
Audit and monitoring tools weren’t built for today’s reality. They were built when data was centralized, identities were human, and activity patterns were predictable. Now, teams must navigate:
- Cloud object stores with inconsistent visibility
- Collaboration tools with delayed or partial audit logs
- On-prem systems with no unified access history
- DSPM tools that highlight risks but lack usage insight
- Activity monitoring tools that detect behavior but ignore data sensitivity
This fragmentation creates blind spots and real risk:
- Gaps across cloud, SaaS, and on-prem systems
- Difficulty distinguishing normal vs. suspicious behavior
- Limited insight into service accounts and automated processes
- No oversight of AI-driven or machine identities
- Slow, incomplete breach investigations
- Challenges in meeting HIPAA, GLBA, GDPR, and CCPA audit requirements
Security teams are left piecing together evidence from half a dozen systems — often under pressure, and without full confidence in the story the logs tell.
Activity Explorer: One Place to Understand All Data Activity
Activity Explorer, part of BigID’s Data Activity Monitoring solution, provides a unified and context-rich view of how data is accessed and used across systems like AWS S3, SharePoint, OneDrive, Google Drive, NetApp, and on-prem file shares.
Rather than stitching together logs from separate platforms, teams can now see activity enriched with meaningful context: data sensitivity, classification, identity details, permissions, ownership, and access exposure.
Activity Explorer is built for the way modern data actually moves.
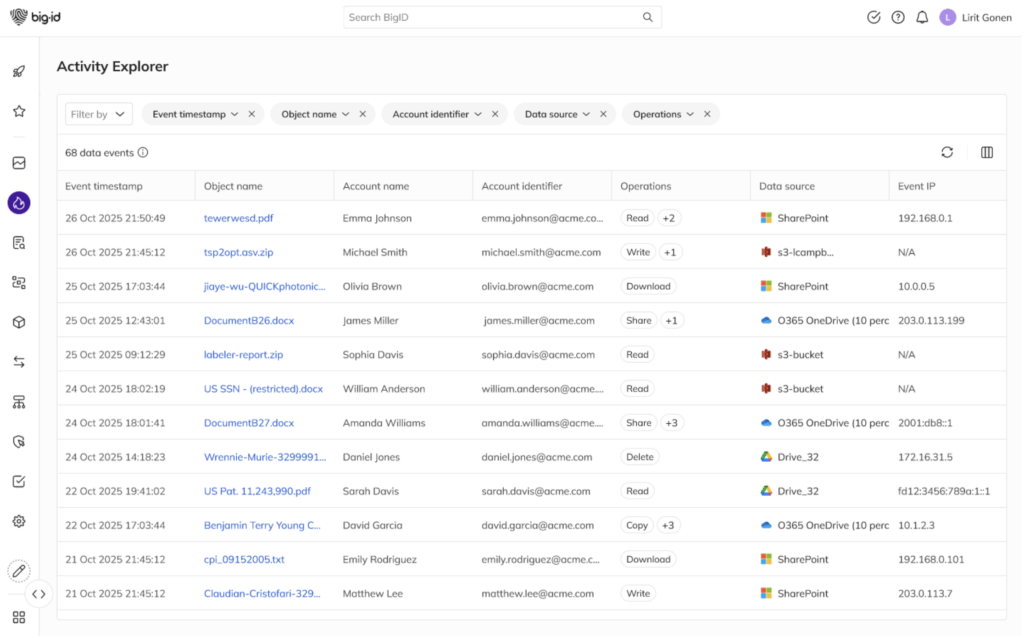
Search and Investigate with Precision
Filter and trace activity by identity (human or machine), operation type, data resource, time range, or sensitivity level. Investigations that once took hours now take seconds.
Trace Every Action Across Hybrid Environments
See how data moves — what was accessed, shared, downloaded, deleted, or modified — across cloud, SaaS, and on-prem environments, all in one view.
Monitor All Identity Types, Not Just Users
Activity Explorer captures activity from:
- Users
- Service accounts
- Automated workflows
- AI assistants and AI-driven agents
As identity models evolve, visibility keeps pace.
Investigate and Respond Faster
Answer questions like:
- “Who deleted this file?”
- “What did this user touch yesterday?”
- “Which sensitive files were downloaded during this time window?”
Analyze Breach Blast Radius with Confidence
Instantly see every file and repository a compromised identity touched – reducing containment time and clarifying exposure.
Maintain Compliance-Ready Audit Trails
Activity Explorer enriches every event with sensitivity, classification, and ownership, providing clear evidence for regulatory audits across HIPAA, GLBA, GDPR, CCPA, and more.
Why Activity Explorer Is Different
Activity Explorer introduces a level of context and visibility that legacy data activity monitoring tools and other DSPM platforms simply don’t provide. It’s built on BigID’s deep data insights and context – turning raw events into meaningful insights.
With Activity Explorer, organizations gain:
- Context-rich investigations: Activity correlated with sensitivity, identity, permissions, and ownership
- Hybrid visibility: A unified audit view spanning cloud, SaaS, and on-prem data systems
- Identity coverage: From human users to service accounts, automation, and AI agents
- Data-aware detection: High-risk actions surfaced with contextual intelligence
- Faster time-to-answer: Search-driven investigations powered by BigID’s data context
This is BigID’s Data Activity Monitoring – designed for modern, distributed, AI-accelerated environments.
Move Beyond Fragmented Logs. See What’s Really Happening With Your Data.
Organizations can no longer rely on fragmented logs or siloed monitoring to understand how sensitive data is being used. Activity Explorer delivers the visibility, context, and investigative speed needed to detect insider threats early, accelerate incident response, and maintain compliance across hybrid environments.
Want to learn more? Set up a 1:1 with one of our AI and data security experts today!