A 24/7 Security Mission—Backed by Smarter Ops
At BigID, we provide around-the-clock, follow-the-sun security event triage and response across all our cloud offerings. We apply the same rigor to our internal corporate security—because protecting our employees and systems reduces risk across the board, including the probability of compromise and data leakage from our cloud products.
Like many security teams, we faced challenges with first-line alert triage and response. To address this, we initially leaned on a Managed Detection and Response (MDR) provider to handle initial analysis and escalate suspicious activity to our internal team. While this model worked for years, it had clear limitations: lack of contextual adaptation, high analyst turnover, and persistent alert fatigue.
Enter Agentic AI: Moving Beyond MDR
To break free from these constraints, we embraced Agentic AI and transitioned to an AI-SOC (AI-powered Security Operations Center). This shift lets us offload the entire first-line triage and focus our human talent on higher-value, strategic response and investigation.
How AI-SOC Works
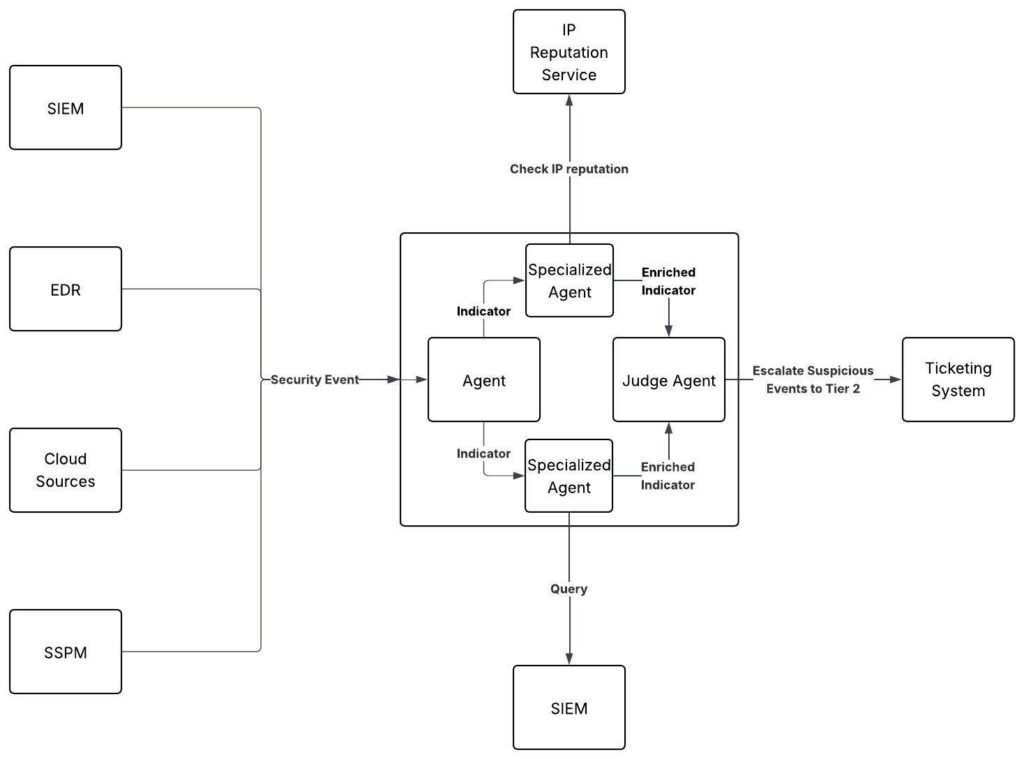
An AI-SOC ingests events from a wide range of sources—SIEM, IdP, EDR, IPS, SSPM, and more. It runs agent-powered playbooks that break down each event into indicators. Specialized agents enrich and assess each indicator using threat intel feeds, CSPM tools, SIEM queries, and other internal or external data sources.
Each agent makes a determination—malicious or benign. Once all indicators are evaluated, the system concludes whether the overall event requires tier-2 escalation or should be marked as non-suspicious.
Operationalizing AI at BigID
Full Visibility, Smart Enrichment
We feed the AI-SOC a continuous stream of security events—from our cloud infrastructure, SIEM alerts, EDR data, and cloud audits. The AI-SOC is also connected to internal tools like our CSPM and Security Data Lake to enrich analysis with deeper context.
Additionally, it’s integrated with our escalation platform to trigger tier-2 handoffs automatically for suspicious events.
Results: Faster, Fewer Escalations—and Greater Confidence
Since implementing our AI-SOC, we’ve seen:
- Faster triage and analysis
- Fewer escalations to tier 2
- No degradation in quality
Every week, we run quality control checks by randomly reviewing AI-classified false positives to validate outcomes. So far, the AI’s conclusions have consistently matched human judgment—thanks to one crucial capability: transparency.
Why Transparency Matters
An AI-SOC is only as trustworthy as it is explainable. We chose a solution that allows us to trace every decision, every indicator, and every enrichment step. This auditability builds confidence, keeps us compliant, and ensures that human oversight is always possible when needed.
“Paranoia Mode”—Without the Fatigue
One of the biggest advantages of AI? It doesn’t burn out. Alert fatigue is no longer a bottleneck. We’ve actually increased the volume of events we analyze—switching to what we call “paranoia mode.” We cast a wider net, even if it means more false positives, because the AI handles them swiftly and consistently.
What’s Next: AI-SOC + BigID Platform Integration
We’re working with our AI-SOC vendor to integrate directly with the BigID platform. This means:
- Security events from the BigID platform will feed directly into the AI-SOC
- BigID will serve as an enrichment source—providing context about sensitive data and asset criticality
The result: smarter triage, faster prioritization, and shorter response times for data-sensitive threats.
Stay tuned—this is just the beginning of our AI-SOC journey.