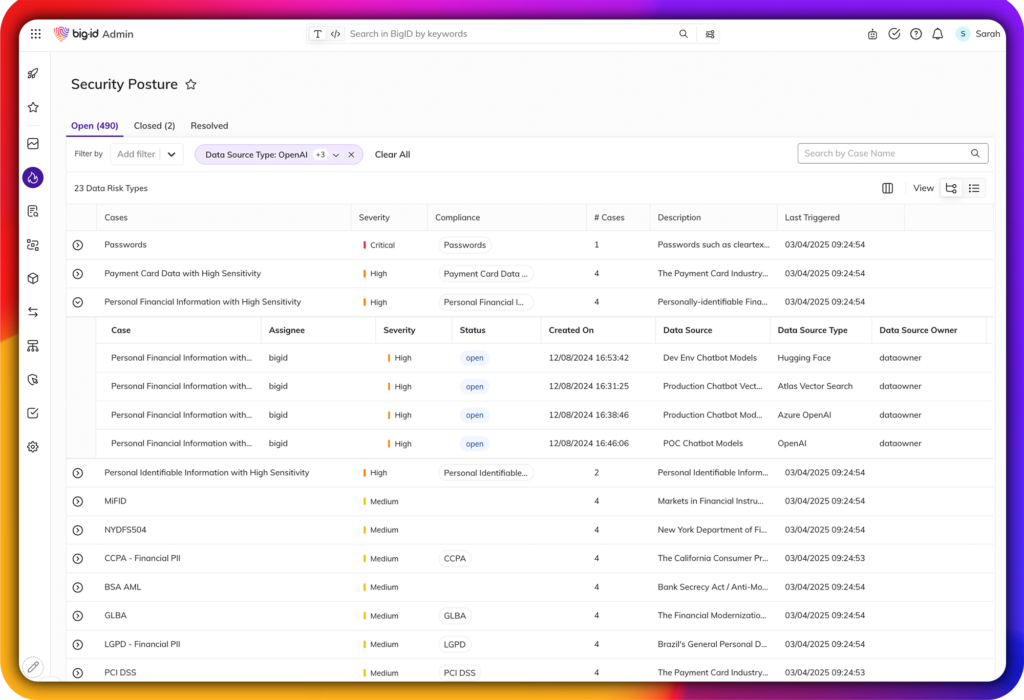
Real-Time Data Activity Monitoring
Track and analyze how sensitive, critical, and regulated data moves inside and outside your organization- across cloud, SaaS, file shares, and messaging apps.
With BigID DDR, security and risk teams can:
Monitor and detect risky data activity across cloud, SaaS, and on-prem environments
Identify insider threats, malicious behavior, and exposure events before they escalate
Take immediate action to reduce risk and strengthen your data security posture
Go beyond traditional monitoring - connect detection to real action:
Track and analyze how sensitive, critical, and regulated data moves inside and outside your organization- across cloud, SaaS, file shares, and messaging apps.
Surface unusual activity like unsanctioned data movement, anomalous access, privilege escalation, or suspicious usage patterns.
Focus your response on what matters most – highlighting the highest-risk activities tied to your most sensitive and valuable data assets.
Trigger quarantine, revoke access, or initiate incident workflows based on customizable policies to neutralize threats fast.
Correlate risky behavior with data sensitivity, user access rights, entitlements, and AI activity to understand who did what, where, and why.
Feed DDR insights into your SIEM, SOAR, DLP, and IRM systems for faster triage, investigation, and response across your enterprise.
Protect your growing data ecosystems—including AI pipelines and cloud-native services—without slowing down innovation or operations.
Discover, detect, and defend with BigID’s Data Detection and Response.



















