In der heutigen verteilten Datenumgebung ist das “Geringste Privilegien”Das „Minimalzugriffsmodell“, das sicherstellt, dass Einzelpersonen und Systeme nur über die minimal notwendigen Zugriffsrechte verfügen, gilt als Goldstandard für Sicherheit. Doch die Umsetzung ist oft leichter gesagt als getan. Sicherheitsteams sehen sich mit einer unüberschaubaren Menge an Berechtigungen konfrontiert, deren manuelle Überprüfung tausender Berechtigungen für Benutzer, Rollen und Gruppen nicht praktikabel ist. Erschwerend kommt hinzu, dass häufig der Kontext fehlt: Die Zugriffsverwaltung ist ohne Kenntnis der sensiblen, regulierten oder geschäftskritischen Daten äußerst schwierig.
Um dieses Problem zu lösen, müssen Unternehmen von einer zentralisierten Steuerung zu einem dezentralen Ansatz übergehen und diejenigen stärken, die die Daten am besten kennen: die Dateneigentümer. Hier finden Sie eine praktische 5-Schritte-Anleitung zur Reduzierung Ihrer Angriffsfläche und zur Durchführung effektiver Berechtigungsprüfungen, abgestimmt auf die BigID-Produkte, die dies ermöglichen.
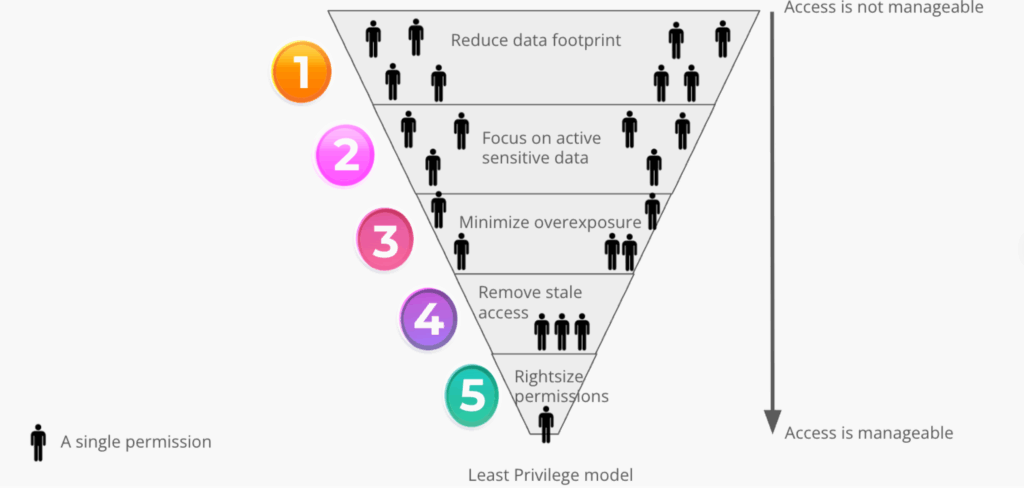
Schritt 1: Fokus auf aktive, sensible Daten
Die Herausforderung: Was man nicht sieht, kann man nicht schützen. Der Versuch, die Zugriffsrechte für jede einzelne Datei im Unternehmen zu überprüfen, führt nur zu Frustration.
Die Lösung: Priorisieren Sie. Identifizieren Sie die wichtigsten Daten – sensible, regulierte und kritische Geschäftsdaten – und konzentrieren Sie Ihre Bemühungen darauf.
- BigID-Produkt: Datenermittlung und -klassifizierung.
- So hilft es: BigID durchsucht Ihren gesamten Datenbestand (Cloud, On-Premise, SaaS) um sensible Informationen zu ermitteln und zu klassifizieren. Dies liefert Ihnen den nötigen Kontext, um irrelevante Informationen herauszufiltern und die Überprüfung auf risikoreiche Daten zu konzentrieren.
Schritt 2: Reduzieren Sie Ihren Daten-Fußabdruck
Die Herausforderung: Datenhortung führt zu erhöhten Risiken. Veraltete, ungenutzte Daten behalten oft alte Berechtigungen, die nicht mehr überwacht werden.
Die Lösung: Löschen oder archivieren Sie ungenutzte und veraltete Daten, bevor Sie überhaupt mit der Zugriffsprüfung beginnen. Wenn die Daten nicht existieren, können sie auch nicht offengelegt werden.
- BigID-Produkt: Aufbewahrung von Daten und Datenlöschung.
- So hilft es: Durch die Automatisierung von Aufbewahrungsrichtlinien hilft BigID Ihnen, Daten zu identifizieren und zu löschen, die ihren geschäftlichen Wert verloren haben. Dies reduziert die Anzahl der Dateien, die Dateneigentümer überprüfen müssen, erheblich.
Schritt 3: Veraltete Zugriffsrechte entfernen
Die Herausforderung: Im Laufe der Zeit sammeln Benutzer Berechtigungen an, die sie nicht mehr verwenden, wodurch “ruhende” Zugriffspfade entstehen, die Angreifer ausnutzen können.
Die Lösung: Nicht verwendete oder veraltete Berechtigungen sollten umgehend widerrufen werden.
- BigID-Produkt: Zugriff auf Intelligenz.
- So hilft es: BigID identifiziert Berechtigungen, die seit Längerem nicht mehr genutzt wurden. Der Widerruf dieser offensichtlich veralteten Berechtigungen kann automatisiert werden, ohne dass eine manuelle Entscheidung erforderlich ist. Dies erleichtert die manuelle Überprüfung.
Schritt 4: Überbelichtung minimieren
Die Herausforderung: Zu den größten Risiken zählen weit verbreitete Zugriffseinstellungen, die leicht übersehen werden können, wie beispielsweise Dateien, die über öffentliche Links geteilt werden oder für “Jeder” in der Organisation zugänglich sind.
Die Lösung: Bevor Sie die Dateneigentümer um Unterstützung bitten, sollten Sie offene und externe Zugriffe auf sensible Daten unterbinden. Dadurch wird die Angriffsfläche sofort verringert.
- BigID-Produkt: Zugang zur Intelligenz & DSPM (Management des Datensicherheitsstatus). .
- So hilft es: BigID erkennt und kennzeichnet übermäßig exponierte Daten und identifiziert offenen und externen Zugriff auf sensible Informationen. Sicherheitsteams können diese risikoreichen Zugriffe global absichern und so sicherstellen, dass nur bestimmte, unbedingt notwendige Benutzer für die abschließende Überprüfung zugelassen werden.
Schritt 5: Berechtigungen richtig dimensionieren (Die menschliche Ebene)
Die Herausforderung: Sobald die offensichtlichen Risiken automatisiert sind, bleiben legitime Benutzer übrig, die möglicherweise immer noch über übermäßige Berechtigungen verfügen. Um dies zu überprüfen, ist ein geschäftlicher Kontext erforderlich, der Sicherheitsteams fehlt.
Die Lösung: Ermächtigen Sie die Dateneigentümer, die verbleibenden Zugriffsrechte zu überprüfen und zu bestätigen, um ein echtes Prinzip der minimalen Berechtigungen zu gewährleisten.
- BigID-Produkt: Delegierte Sanierungs-App.
- So hilft es: Hier zeigt sich, was wirklich zählt. BigID verlagert die Verantwortung vom Sicherheitsteam auf die Dateneigentümer durch einen optimierten, automatisierten Workflow. Eigentümer können die aktuellen Berechtigungen einfach überprüfen und entscheiden, ob sie diese beibehalten oder widerrufen möchten.
Abschluss
Durch die Kombination einer automatisierten Reduzierung der Datenoberfläche mit einer Überprüfung delegierter Berechtigungen können Organisationen von einem chaotischen, datenintensiven Durcheinander zu einem optimierten, sicheren Modell der minimalen Berechtigungen übergehen.
Sind Sie bereit, Ihre Angriffsfläche zu verringern? Identifizieren Sie Ihre sensiblen Daten, bereinigen Sie veraltete und offene Zugriffe und geben Sie die Kontrolle mit BigID wieder in die Hände Ihrer Dateneigentümer.
Nehmen Sie noch heute Kontakt mit einem unserer Datensicherheitsexperten auf. Vereinbaren Sie hier ein 1:1-Gespräch, um loszulegen!