Protection
Transformez la cybersécurité et la protection des données avec une approche centrée sur la confidentialité
Créez et maintenez automatiquement un inventaire de données personnelles à grande échelle qui exploite l'intelligence d'identité, la classification ML et la corrélation PI dans toute votre entreprise pour plusieurs mandats de confidentialité.
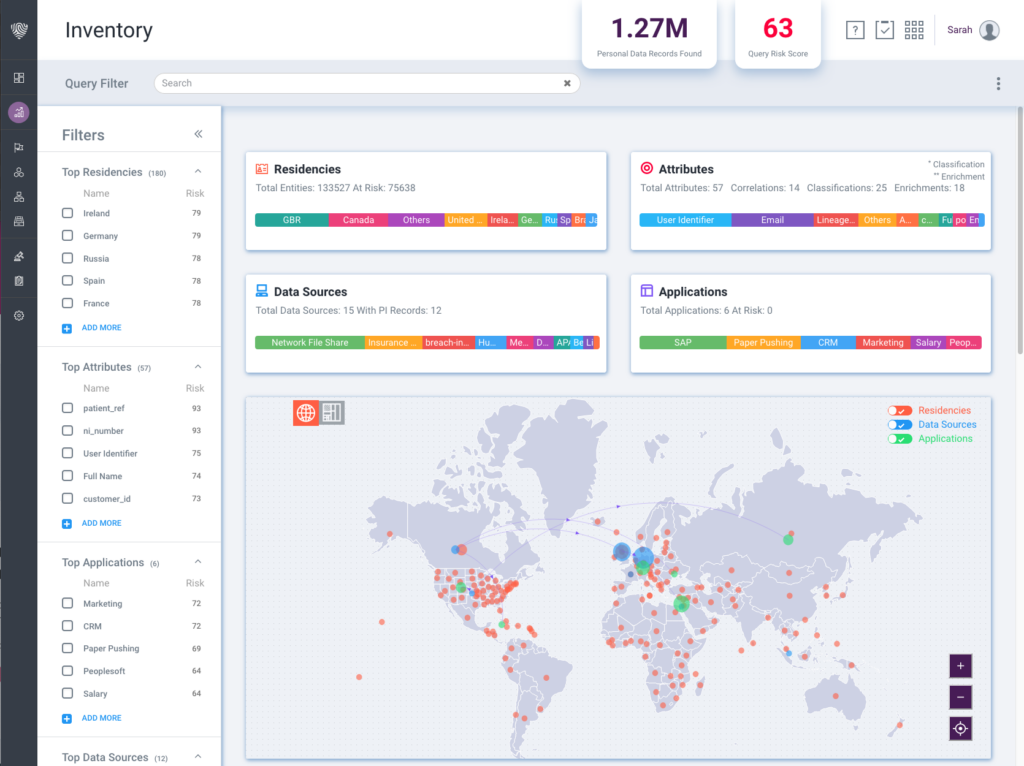
Classez, corrélez et cataloguez les données en mouvement et les données au repos, sur des données non structurées, structurées, Big Data, SaaS, IaaS, des entrepôts et des lacs de données, des plateformes de messagerie et des applications commerciales critiques comme SAP et Salesforce.

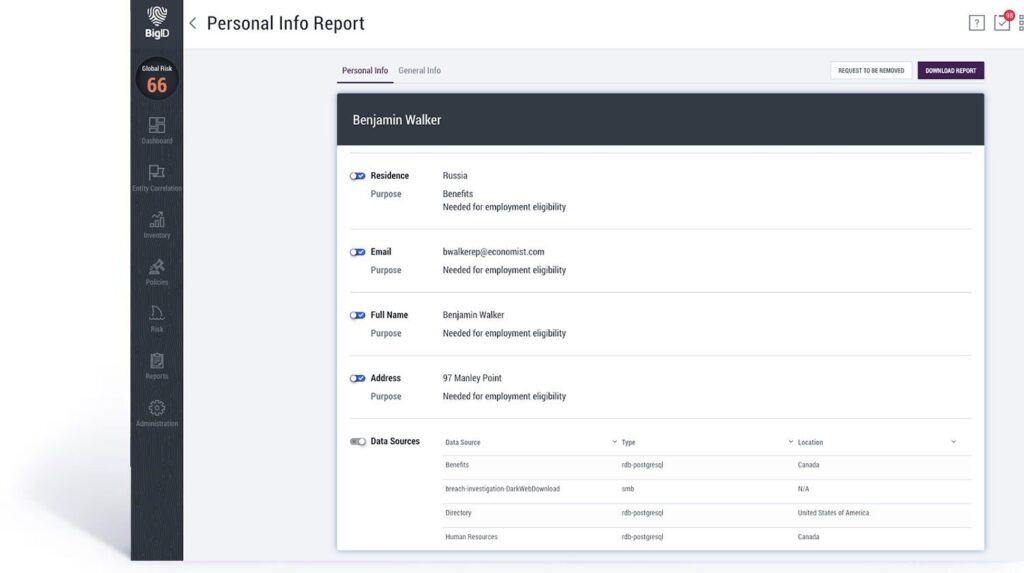
Générez automatiquement des rapports d'accès des personnes concernées à partir de l'inventaire à grande échelle, avec possibilité de personnalisation selon les besoins de l'entreprise et d'intégration aux glossaires métier. Facilitez les demandes de suppression de données.
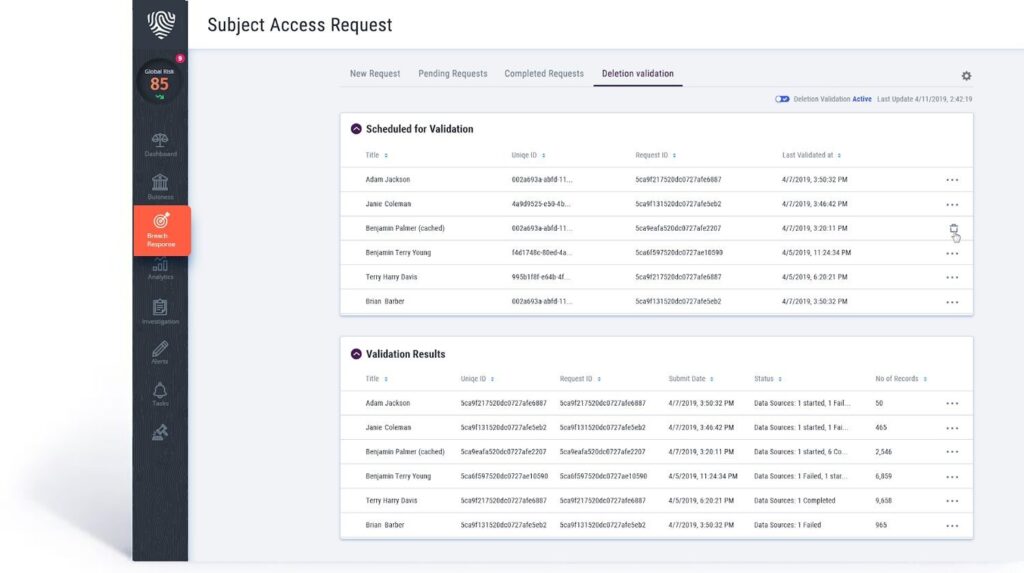
Exploitez les flux de travail des modèles de suppression pour opérationnaliser les demandes de droit à l'oubli, garantir la validation automatisée de la suppression des données et la surveillance des violations des politiques pour une conformité continue.
Interrogez votre inventaire de données personnelles par plusieurs attributs pour identifier directement le profil d'un utilisateur.
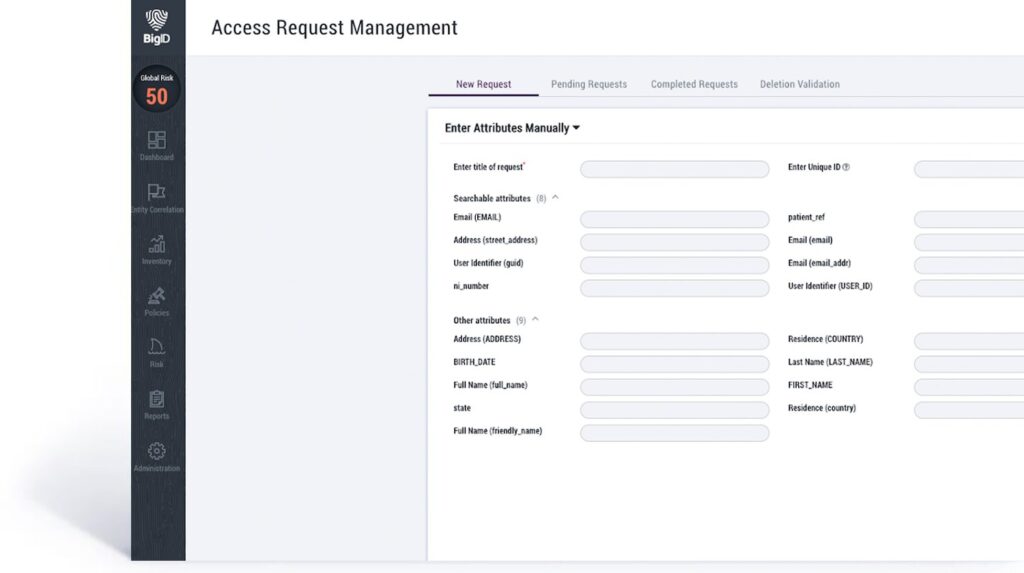
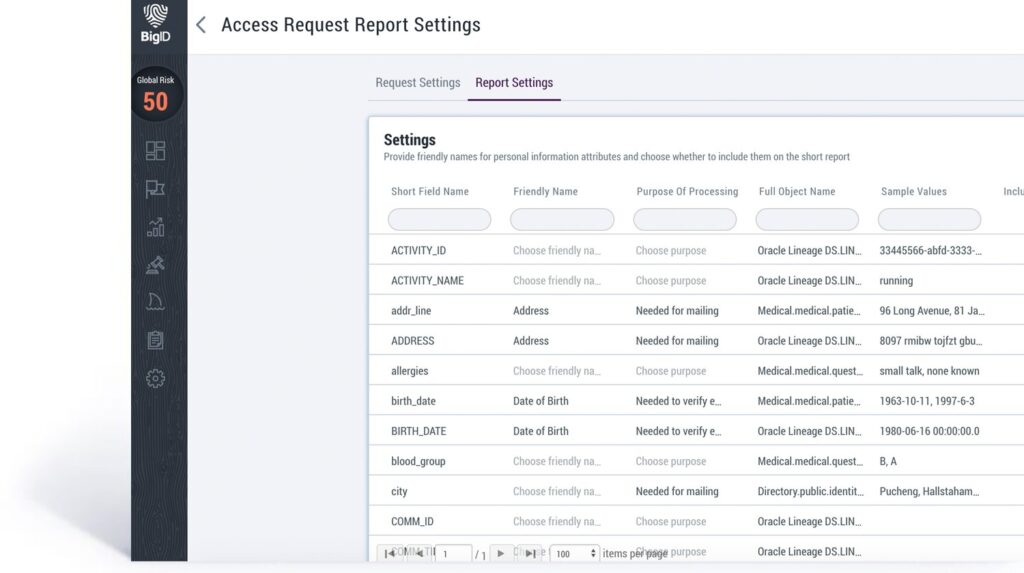
Personnalisez les modèles de rapports et définissez les paramètres en fonction des règles métier pour des types d'utilisateurs spécifiques. Modifiez la représentation externe de l'attribut et de la finalité du traitement.
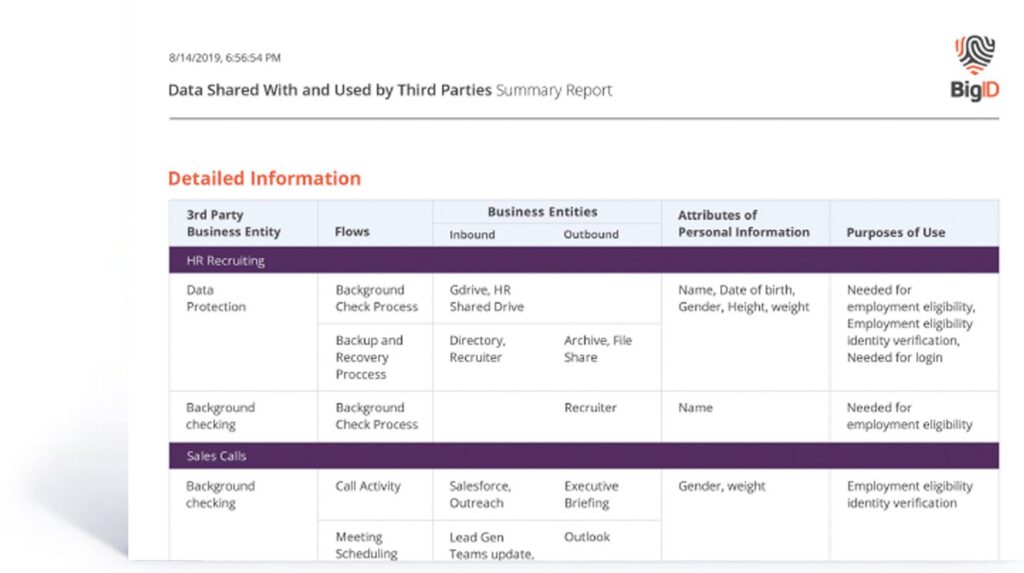
Générez automatiquement des cartes de flux de données et des rapports par tiers, directionnalité, processus métier et attributs pour les données au repos et en mouvement.
Obtenez une démonstration personnalisée avec nos experts en données sur la confidentialité, la protection et la perspective - et voyez BigID en action.
Transformez la cybersécurité et la protection des données avec une approche centrée sur la confidentialité
Optimisez la gouvernance et appliquez une intelligence approfondie des données pour tirer le meilleur parti de vos données



















