Eine Sicherheitsmission rund um die Uhr – unterstützt durch intelligentere Operationen
Bei BigID bieten wir rund um die Uhr Sicherheitsvorfälle priorisieren und darauf reagierend – für all unsere Cloud-Angebote. Dieselbe Sorgfalt wenden wir auch bei unserer internen Unternehmenssicherheit an, denn der Schutz unserer Mitarbeiter und Systeme reduziert Risiken in allen Bereichen, einschließlich der Wahrscheinlichkeit von Kompromittierung und Datenverlust aus unseren Cloud-Produkten.
Wie viele Sicherheitsteams standen auch wir vor Herausforderungen bei der Priorisierung und Reaktion auf Erstwarnungen. Um dem entgegenzuwirken, setzten wir zunächst auf … Managed Detection and Response (MDR) Ein externer Dienstleister übernahm die erste Analyse und leitete verdächtige Aktivitäten an unser internes Team weiter. Dieses Modell funktionierte zwar jahrelang, wies aber deutliche Schwächen auf: mangelnde Anpassungsfähigkeit an den jeweiligen Kontext, hohe Fluktuation der Analysten und ständige Alarmmüdigkeit.
Agentic AI: Mehr als nur MDR
Um uns von diesen Zwängen zu befreien, haben wir uns dafür entschieden Agentische KI und ging über zu einem AI-SOC (KI-gestütztes Sicherheitsoperationszentrum). Durch diese Umstrukturierung können wir die gesamte Erstversorgung auslagern und unsere Mitarbeiter auf höherwertige, strategische Reaktionen und Untersuchungen konzentrieren.
Wie KI-SOC funktioniert
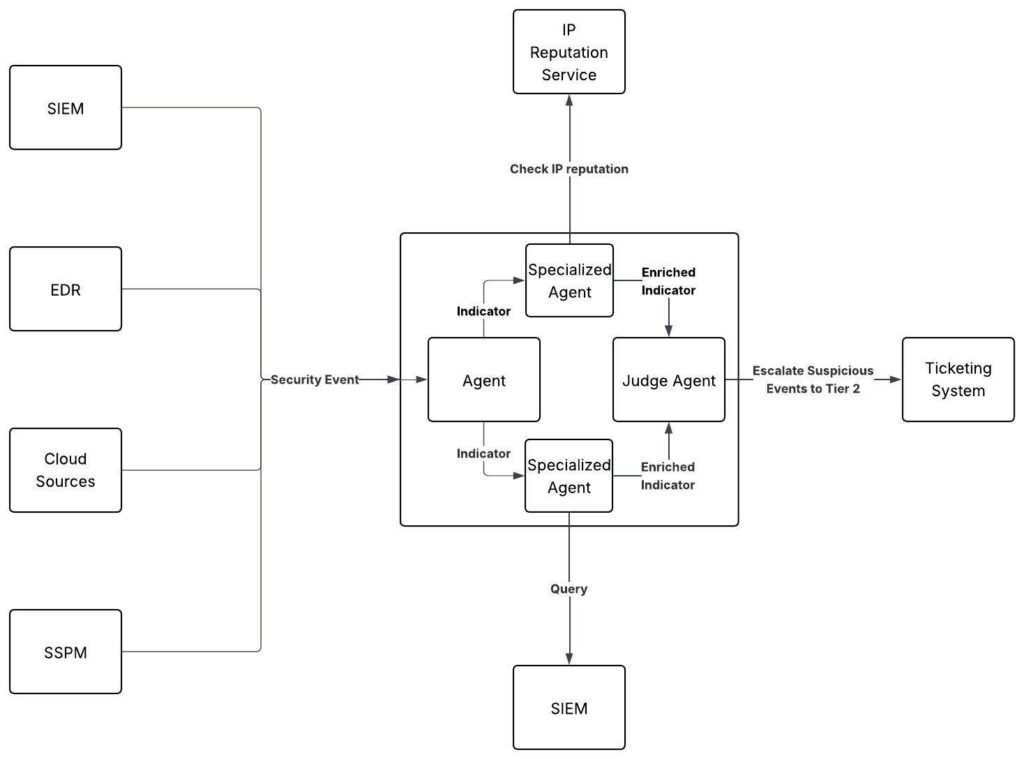
Ein KI-gestütztes SOC erfasst Ereignisse aus einer Vielzahl von Quellen – SIEM, IdP, EDR, IPS, SSPM und mehr. Es führt agentenbasierte Playbooks aus, die jedes Ereignis in Indikatoren aufschlüsseln. Spezialisierte Agenten reichern jeden Indikator mithilfe von Threat-Intelligence-Feeds an und bewerten ihn., CSPM Tools, SIEM-Abfragen und andere interne oder externe Datenquellen.
Jeder Agent trifft eine Entscheidung – ob böswillig oder gutartig.. Sobald alle Indikatoren ausgewertet sind, kommt das System zu dem Schluss, ob das Gesamtereignis eine Eskalation auf Stufe 2 erfordert oder als nicht verdächtig eingestuft werden sollte.
Operationalisierung von KI bei BigID
Volle Transparenz, intelligente Anreicherung
Wir speisen das KI-gestützte Security Operations Center (AI-SOC) kontinuierlich mit Sicherheitsereignissen – aus unserer Cloud-Infrastruktur, SIEM-Warnungen, EDR-Daten und Cloud-Audits. Das AI-SOC ist außerdem mit internen Tools wie unserem System verbunden. CSPM und Security Data Lake, um die Analyse mit tiefergehendem Kontext anzureichern.
Darüber hinaus ist es in unsere Eskalationsplattform integriert, um bei verdächtigen Ereignissen automatisch eine Weiterleitung an die zweite Ebene auszulösen.
Ergebnisse: Schnellere, weniger Eskalationen – und mehr Vertrauen
Seit der Implementierung unseres KI-SOC haben wir Folgendes beobachtet:
- Schnellere Triage und Analyse
- Weniger Eskalationen auf Stufe 2
- Keine Qualitätsminderung
Wöchentlich führen wir Qualitätskontrollen durch, indem wir stichprobenartig KI-klassifizierte Fehlalarme überprüfen, um die Ergebnisse zu validieren. Bisher stimmten die Schlussfolgerungen der KI stets mit dem menschlichen Urteil überein – dank einer entscheidenden Fähigkeit: Transparenz.
Warum Transparenz wichtig ist
Ein KI-gestütztes Security Operations Center (SOC) ist nur so vertrauenswürdig wie nachvollziehbar. Wir haben uns für eine Lösung entschieden, die es uns ermöglicht, jede Entscheidung, jeden Indikator und jeden Anreicherungsschritt nachzuverfolgen. Diese Nachvollziehbarkeit schafft Vertrauen, gewährleistet die Einhaltung von Vorschriften und stellt sicher, dass bei Bedarf jederzeit eine menschliche Kontrolle möglich ist.
“Paranoia-Modus” – ohne Erschöpfung
Einer der größten Vorteile von KI? Sie ermüdet nicht. Alarmmüdigkeit ist kein Problem mehr. Wir haben die Anzahl der analysierten Ereignisse sogar erhöht – wir sind quasi in den “Paranoia-Modus” geschaltet. Wir gehen noch weiter und analysieren mehr Ereignisse, auch wenn das mehr Fehlalarme bedeutet, denn die KI verarbeitet diese schnell und zuverlässig.
Nächstes Ziel: Integration von AI-SOC und der BigID-Plattform
Wir arbeiten mit unserem KI-SOC-Anbieter zusammen, um die Plattform direkt in die BigID-Plattform zu integrieren. Das bedeutet:
- Sicherheitsereignisse der BigID-Plattform werden direkt in das AI-SOC eingespeist.
- BigID dient als Anreicherungsquelle und liefert Kontextinformationen zu sensiblen Daten und zur Kritikalität von Anlagen.
Das Ergebnis: intelligentere Triage, schnellere Priorisierung und kürzere Reaktionszeiten bei datensensiblen Bedrohungen.
Bleiben Sie dran – dies ist erst der Anfang unserer Reise zum KI-SoC.