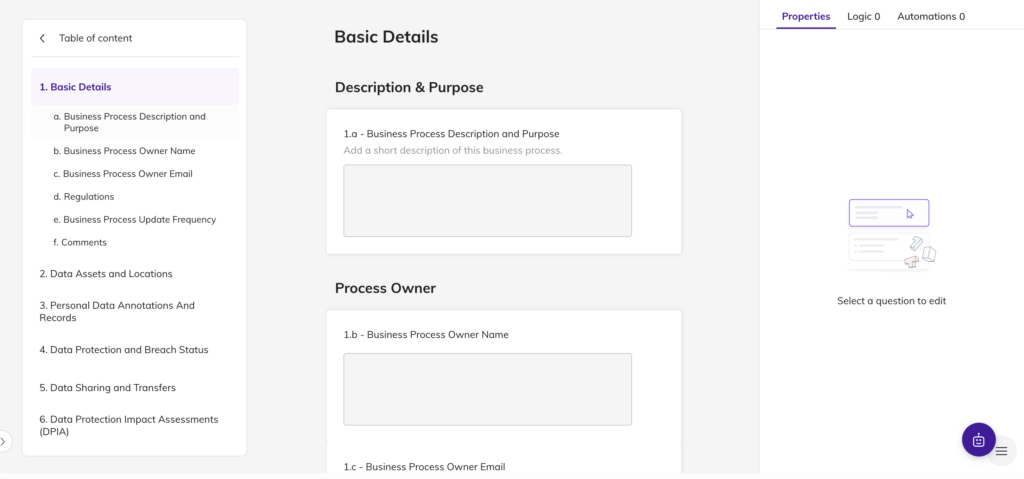
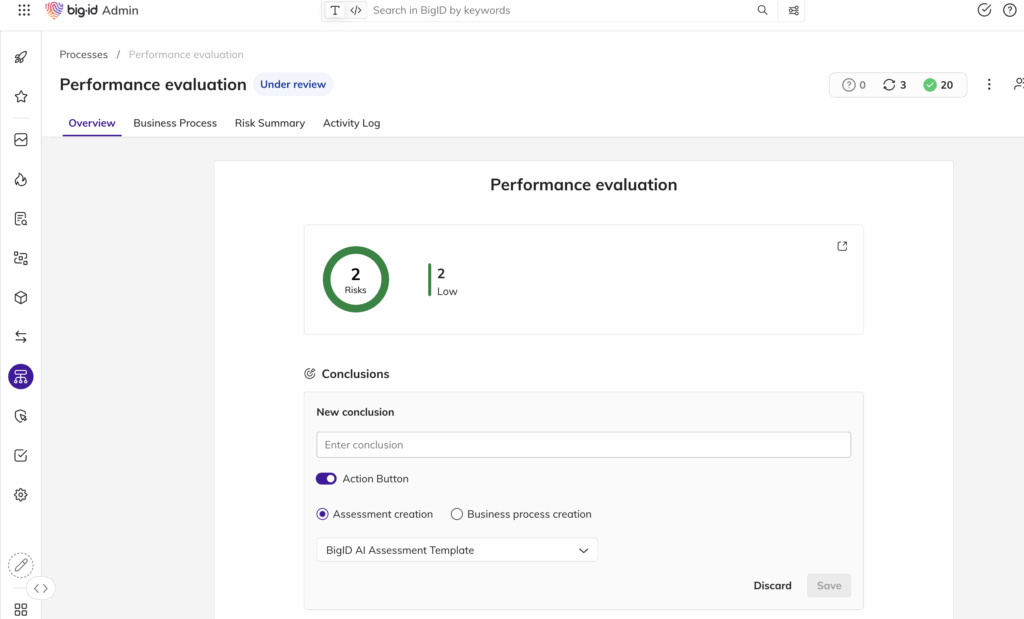
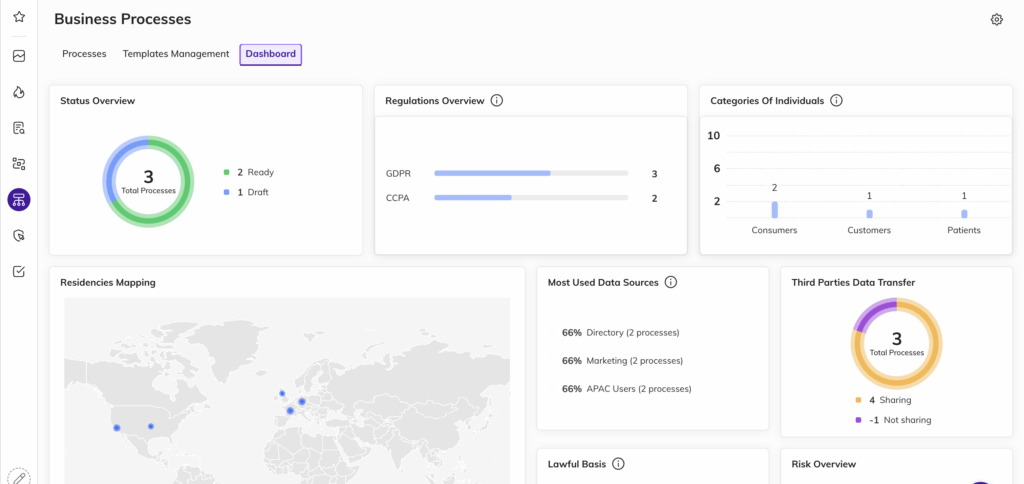
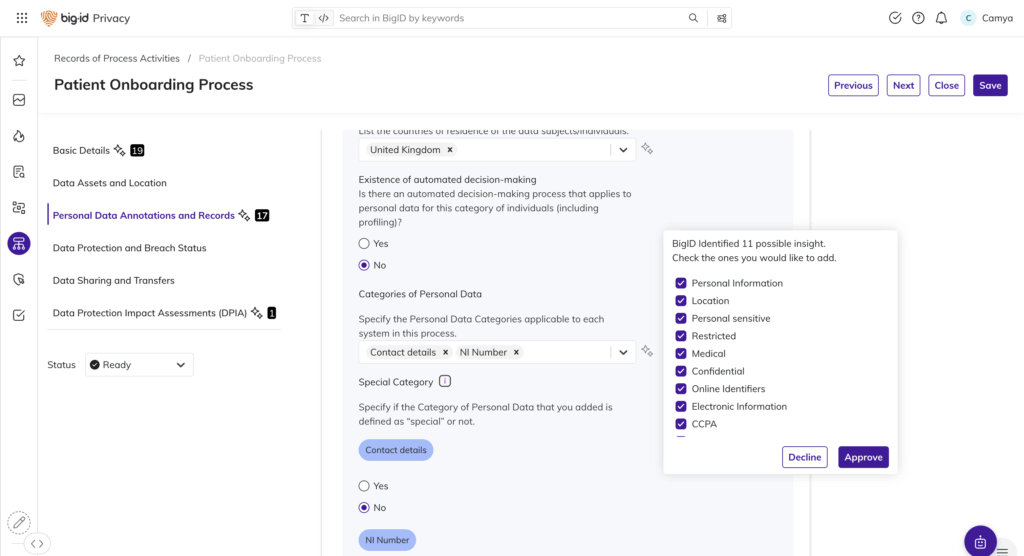
Création automatisée de RoPA
- Découverte automatique et remplissage des enregistrements RoPA à partir de données structurées et non structurées
- Importez des données à partir de fichiers ou de formulaires, ou invitez des collaborateurs de différentes équipes
- Tenir un journal à jour et complet des activités de traitement des données